●Users also need (71) systems to help them explore the web and discover interesting data sources and interfaces that support different query and search paradigms.

You share your computer with ohter users. You install a new Microsoft Windows Internet Explorer add-on to view videos on the computer. You discover that this add-on conflicts with existing add-ons that other users frequently require. You need to ensure that you are able to view videos without affecting other users.
What should you do?()
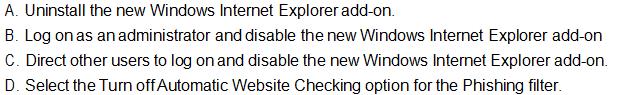
免费的网站请分享给朋友吧