A(75)system placed between the company network and the outside world may limit outside access to the internal network.
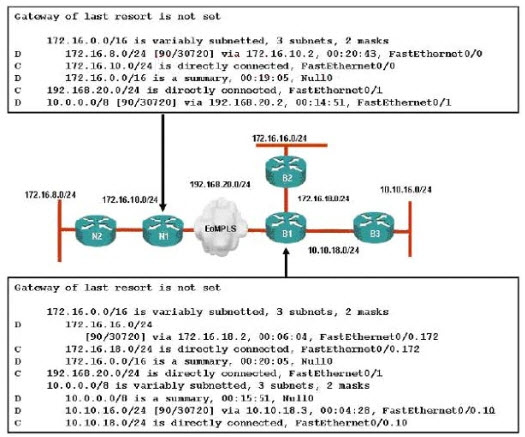
Refer to the exhibit. A Boston company bought the asse ts of a New York company and is trying to route traffic between the two data networks using EIGRP over EoMPLS. As a network consultant, you were asked to verify the interoperability of the two networks. From the show ip route command output, what can yo u tell the customer about the traffic flow between the subnet in New York (172.16.8.0/24) and the subnets in Boston (172.16.16.0/24 and 10.10.16.0/24)?()
Your company's corporate network uses Network Access Protection (NAP).Users are able to connect to the corporate network remotely.You need to ensure that data transmissions between remote client computers and the corporate network are as secure as possible.
What should you do?()

免费的网站请分享给朋友吧