You work as an application developer at Certkiller .com. Certkiller .com has given you the task of creating medical billing application that will deal with various insurance vendors.The appropriate assemblies have to be loaded and unloaded dynamically based on the patient’s insurance provider. All of these insurance assemblies are located in C:\Insurance Assemblies.
You have to ensure that when the new application first loads, it has to load allassemblies into a separate application domain. You need to create the child application domain and load all assemblies it using the correct code. What should you do?()
Exhibit:
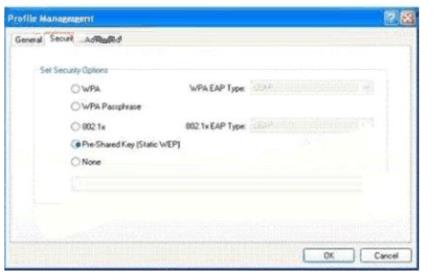
You work as a network administrator at. You study the exhibit carefully. In the wireless LAN all devices are configured with static WEP keys.
What will happen if the access point receives packets sent by the wireless client adapter that are not encrypted with the appropriate key?()
Exhibit:
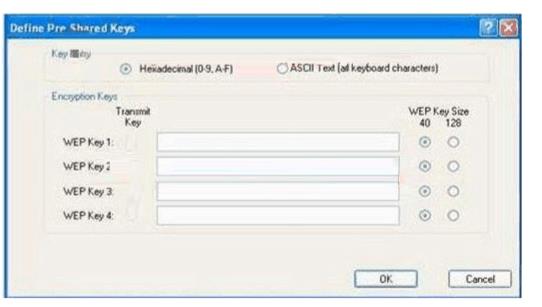
You work as a network technician at. Study the exhibit carefully. You are required configure the static WEP keys on the wireless client adapter using the Cisco ADU (Aironet Desktop Utility).
What should you have in mind when doing this?()
根据写作要求,写出一篇作文。
You are Susan. Your company will hold an opening ceremony for a new factory. You are asked to write an invitation letter to David, an important client of your company. The following information should he included:the reasons to invite him; the time for the event;the place for the event;early reply expected.
Exhibit, error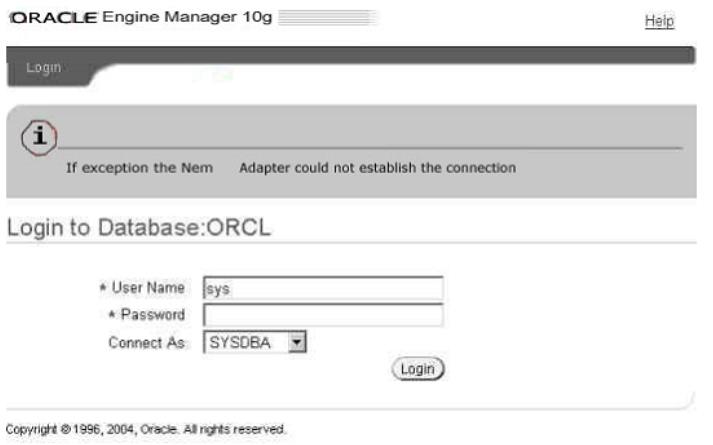
You work as a database administrator for Supportcenter.cn. When you try to connect to the database, you get an error (See exhibit). What could be the possible reason for getting such an error?()
You create an ASP.NET server control in the SampleControl namespace. The control uses a JavaScript file names Refresh.js to implement AJAX functionality.You need to ensre that the JavaScript file is included in the assembly.
Which two actions should you perform?()
You work as a Web Developer at Certkiller.com. You are in the process of creating a Webapplication using Microsoft ASP.NET 3.5.
You host the Web application in Microsoft Internet Information Services (IIS) 6.0. You browse theapplication and receive the following error message:
Server Application Unavailable
The web application you are attempting to access on this web server is currently unavailable.Please hit the "Refresh" button in your web browser to retry your request.
You view the Application event log and discover the following message:
It is not possible to run two different versions of ASP.NET in the same IIS process. Please use theIIS Administration Tool to reconfigure your server to run the application in a separate process.
To ensure productivity you need to solve this problem as quick as possible.
What should you do?()
You are designing a top-level OU structure to meet the business and technical requirements.
Which top-evel OU or OUs should you use? ()
You work as a senior administrator at ABC.com. The ABC.com network consists of a single domain named ABC.com. All servers on the ABC.com network have Windows Server 2012 R2 installed, and all workstations have Windows 8 installed. You are running a training exercise for junior administrators.You are currently discussing the Always Offline Mode.
Which of the following is TRUE with regards to the Always Offline Mode?()
You work as a senior administrator at ABC.com. The ABC.com network consists of a single domain named ABC.com. All servers on the ABC.com network have Windows Server 2012 R2 installed.
You are running a training exercise for junior administrators. You are currently discussing the Windows Firewall with Advanced Security feature.
Which of the following is TRUE with regards to Windows Firewall with Advanced Security?()
The network consists of two separate autonomous systems as shown below:
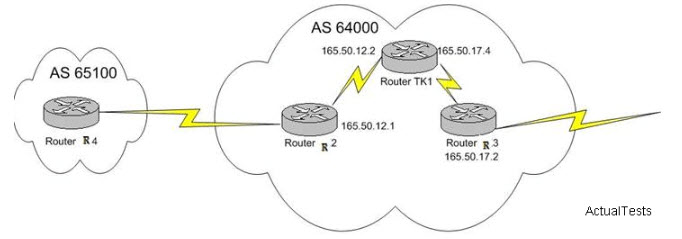
You need to configure Router R2 as a BGP route reflector and Router R1 as the client. Assumingthat Router R3 isn’t running BGP, which two of the commands below would you enter on R2 tosatisfy your goals?()
You are employed as the Exchange administrator at Company.com.You are in the process of
installing a new Exchange Server 2010 Organization.After the installation you send a text message to an external client and receive the subsequent non-delivery report (NDR): "Delivery has failed to these recipients or groups: [email protected] ([email protected]).The recipient’s e-mail system isn’t accepting messages now.Please try resending this message later or contact the recipient directly." You attempt to e-mail the user from an external e-mail system with great success.To ensure productivity you need to make sure e-mails can be sent to external clients from within the organization.
What should you do?()
Your portable computer is in sleep mode. When you resume work on the portable computer, you are not prompted for a password.
You need to ensure that you are prompted for a password each time the portable computer recovers from sleep mode.
What should you do?()

You are working on a very large database. You had performed a binary backup of the control file a month ago. After this you added a few tablespaces, and dropped a couple of tablespaces. This morning, due to hardware failure, you lost all your control files.
How would you recover the database from this situation?()
You work in a company which is named Wiikigo Corp. The company uses SQL Server 2008. You are the administrator of the company database. Now you are in charge of a SQL Server 2008 instance. There is a database named DB1 in the instance. In the database, a small percentage of data is modified everyday. Ever day in the morning, you have to create a read-only copy of the database for reporting purposes and make sure that you use as little disk space as possible.
In the options below, which strategy should you use?()
You work in a company which is named Wiikigo Corp. The company uses SQL Server 2008. You are the administrator of the company database. Now you are in charge of a SQL Server 2008 instance. There is a text file which is named SQL01.log on the E: drive. A SQL Server Agent job executes every 2 minutes and logs information to the text file. You get a report from users saying that the sever doesn't make response. As the technical support, you check and find that the SQL Server Agent service does not run and the SQL Server Agent job no longer functions. You have to identify the reason why the SQL Server Agent service is unresponsive.
In the options below, which log should you check? ()
A co-worker is unable to invite you to a Microsoft Windows Meeting Space meeting. You need to receive an invite to the meeting.
What should you do?()
You are designing an automated deployment process for a Windows Azure application.
The process must deploy the application to Windows Azure without any user interaction. You need to recommend a deployment strategy.
What should you recommend?()
You are the network administrator for Company. to do an unattended installation so you create an Answer.txt file by using Setup Manager. The Answer.txt is copied to a floppy disk and you start the installation on a test computer by booting the computer with the Windows 2000 Professional CD-ROM. You insert the floppy disk after the computer starts. Although you had set the user interaction level to full unattended mode, you are prompted for all the required parameters. You want to ensure that the unattended installation upgrades the Windows 98 computers.
What should you do?()
You are the administrator of Red Lington Enterprises. You want to upgrade 125 computers from Windows NT Workstation 4.0 to Windows 2000 Professional. You create an unattend.txt file by using the setup manager.
You copy the file to a floppy disk. You then start the installation on a computer in the test lab using the Windows 2000 Professional CD-ROM. After the computer starts you insert the floppy disk. Even though you set the user interaction level to full-unattended mode you are prompted for all the configuration parameters. You want to ensure that the unattended installation does not prompt you for input.
What should you do? ()
You issued the following RMAN command:
RMAN> CONFIGURE CONTROLFILE AUTOBACKUP ON;
What is NOT an impact of using the above command?()

You work as a network engineer for . You study the exhibit carefully. Three switches are configured for HSRP. Switch1 remains in the HSRP listen state.
What is the most likely cause of this status?()
You work as the exchange administrator at TestKing.com. The TestKing.com network contains anExchange Server 2010 Organization that contains a number of Hub Transport servers.
During the course of day you receive an instruction form management to recommend a messaging
hygiene solution. Your recommendation should ensure that servers known to send spam is blocked andthat the administrative efforts are reduced.
What should you do?()
Your computer has Microsoft Windows Firewall enabled.
Your child plays an online game that uses connectionless traffic over port 5678 for inbound and outbound traffic.
You need to prevent your child from playing this game.
What should you do? ()
You add an Online Responder to an Online Responder Array. You need to ensure that the new Online Responder resolves synchronization conflicts for all members of the Array.
What should you do()
You add an Online Responder to an Online Responder Array.
You need to ensure that the new Online Responder resolves synchronization conflicts for all members of the Array.
What should you do()
You work as the enterprise exchange administrator at TestKing.com. TestKing.com makes use of
Microsoft Exchange Server messaging solution. The TestKing.com network consists of a single ActiveDirectory domain named testking.com.
TestKing.com has its headquarters in Chicago and a branch office in Dallas. Both offices are an ActiveDirectory site that is connected via high speed WAN link. The employees in these offices connect locallyto the servers in these offices.
You are planning to install Exchange Server 2010; however, you need to plan the installation of theMailbox servers with the following criteria:
* It should maintain user access to mailboxes from a server in their site, if a Mailbox server fails.
* Remote mailboxes should bei accessible if a site fails.* Use the minimum amount of serves.
What should you do?()
You are working as a DBA on the decision support system. There is a business requirement to track and store all transactions for at least three years for a few tables in the database. Automatic undo management is enabled in the database.
Which configuration should you use to accomplish this task?()
You work as a network technician at. Your boss, Mrs. , is interested in the Spanning Tree Protocol timers.
What can you tell her regarding the default STP timers? ()
You work as a network technician at Company. Your boss, Mrs., is interested in LWAPP (Lightweight Access Point Protocol).
What should you tell her regarding this technology? ()
You work as a network technician at Company. Your boss, Mrs., is interested in the Cisco Compatible Extensions program.
What are three features of this program? ()
You work as an application developer at Certkiller .com. Certkiller .com has given you the task of creating medical billing application that will deal with various insurance vendors.The appropriate assemblies have to be loaded and unloaded dynamically based on the patient’s insurance provider. All of these insurance assemblies are located in C:\Insurance Assemblies.
You have to ensure that when the new application first loads, it has to load allassemblies into a separate application domain. You need to create the child application domain and load all assemblies it using the correct code. What should you do?()

Your network contains an Active Directory domain. All servers run Windows Server 2008 R2.
You need to audit the deletion of registry keys on each server.
What should you do()
免费的网站请分享给朋友吧