You want to check the details of few errors that users have reported. You search for the alert log file andexecute few commands to find the location of the alert log file. View the Exhibit and check the commandsexecuted.
What is the location of the alert_orcl.log file()
Your network contains an Active Directory domain. All servers run Windows Server 2008 R2.
You need to audit the deletion of registry keys on each server.
What should you do()
You deploy a mobile messaging solution with Microsoft Exchange Server 2003 Service Pack 2.
When the application is running, it must not be able to access protected registry keys.
You need to ensure that the application meets the outlined requirement.
What are two possible ways to achieve this goal?()
You are the administrator of your company's network. A user named David runs Windows 2000 Professional on his portable computer. David wants to be able to work at home on files that he created at the office and stored on the company network. Prior to logging off the network and leaving the office, David enables offline files.
David calls you from home and reports that copies of his folders and files on the network are not available on his portable computer. What should you instruct David to do, so that he can proceed with his work?()
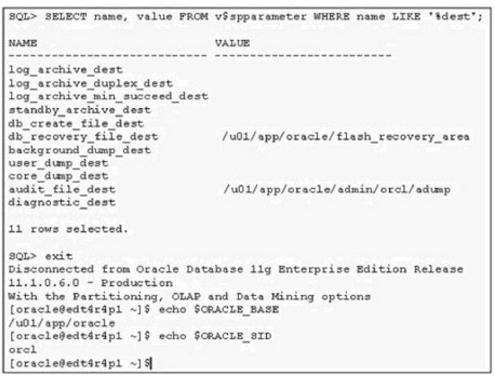
You want to check the details of few errors that users have reported. You search for the alert log fileand execute few commands to find the location of the alert log file. View the Exhibit and check the commands executed.

What is the location of the alert_orcl.log file()
You want to check the details of few errors that users have reported. You search for the alert log file andexecute few commands to find the location of the alert log file. View the Exhibit and check the commandsexecuted.
What is the location of the alert_orcl.log file()

You are the desktop administrator for ExamSheet.
Your Windows 2000 Professional computer is configured to support two monitors. You install a DOS-based application on your computer. The application uses the Windows 2000 Professional default settings Autoexec.nt and Config.nt.
Your primary video adapter is set to 24 bit color, 800 x 600 resolution, and default refresh rates. Your secondary video adapter is set to 32 bit color, 1024 x 768 resolution, and a refresh refresh of 72 hertz. You create a shortcut for the DOS-based application on the secondary monitor's desktop and use the
default PIF settings. You attempt to run the DOS-based application on the secondary monitor. The application opens, but the display area is scrambled. You then attempt to run the DOS-based application on the primary monitor.
The application does not open. Both monitors function correctly when you run Windows based applications.
You want to be able to run the DOS-based application on either monitor.
What should you do?()
You want to back up your 100-GB database on a remote tape device. You are required to ensure that minimum network bandwidth is consumed while transferring the backups to the tape device.
The current consumption of your CPU is approximately 40 percent.
Which type of backup should you perform?()
You are designing a top-level OU structure to meet the business and technical requirements.
Which top-evel OU or OUs should you use? ()
You are the administrator of a Windows 2000 network. You use a user account named Hans1 to log on to a Windows 2000 Professional computer named Company1 that is used by different students in a classroom. Hans1 is a user with administrative rights. Another administrator has created a command file named AddUsers.cmd that automatically adds student user accounts. You have scheduled a task on Company1 to run AddUsers.cmd later in the evening. The next day you find that the job did not run. There are no errors reported in the Event Log. You want to schedule a task to successfully run AddUsers.cmd.
What should you do? ()
You are a network administrator for ExamSheet.net's Windows 2000 network.
You use a user account named User1 to log on tot a Windows 2000 Professional computer. The computer is used by different students in a classroom. User1 does not have administrative rights. However, you prefer to use this account for your daily activities. Using the Task Scheduler you schedule a task to run a command file named AddUsers.cmd that automatically adds six more student user accounts. You configure the task to run as the administrator account.
After the task was scheduled to have run you open the Task Scheduler and discover a status of "Could not start" for the task. You also discover account logon failure audit events in the computer's Security log.You want the scheduled task to successfully run AddUsers.cmd. You want to accomplish this with the least amount of administrative effort.
What should you do?()
You are employed as the Exchange administrator at Company.com.You are in the process of
installing a new Exchange Server 2010 Organization.After the installation you send a text message to an external client and receive the subsequent non-delivery report (NDR): "Delivery has failed to these recipients or groups: [email protected] ([email protected]).The recipient’s e-mail system isn’t accepting messages now.Please try resending this message later or contact the recipient directly." You attempt to e-mail the user from an external e-mail system with great success.To ensure productivity you need to make sure e-mails can be sent to external clients from within the organization.
What should you do?()
You work in a company which uses SQL Server 2008. You are the administrator of the company database. Now you are in charge of a SQL Server 2008 instance. The instance has databases for a finance application and a manufacturing application. You want to put some limitation on the maximum CPU query time allowed by the applications, so you configure the Resource Governor to achieve this. But you notice that certain reports do not execute successfully any longer on the manufacturing application. You have to allow the manufacturing application to consume more CPU time, so you have to change the Resource Governor configuration.
Which Resource Governor component should you configure?()

You administer a Windows 2000 Professional computer that is shared by multiple users. You receive a phone call from one of the users of the shared computer that tells you that the computer is reporting a kernel stop error. You notice that a user has tried to install video drivers that have caused the computer to become unstable. You want to ensure that users can install only the drivers that are approved by the manufacturer.
What should you do? ()
You need to identify all failed logon attempts on the domain controllers.
What should you do()
You work in a company which is named Wiikigo Corp. The company uses SQL Server 2008. You are the administrator of the company database. Now you are in charge of a SQL Server 2008 instance. There is a text file which is named SQL01.log on the E: drive. A SQL Server Agent job executes every 2 minutes and logs information to the text file. You get a report from users saying that the sever doesn't make response. As the technical support, you check and find that the SQL Server Agent service does not run and the SQL Server Agent job no longer functions. You have to identify the reason why the SQL Server Agent service is unresponsive.
In the options below, which log should you check? ()
You have very few Cisco 7920 wireless IP phones on your network, but lots of wireless laptops. You want toincrease the bandwidth available for the laptops by decreasing the bandwidth reserved for the Cisco 7920phones.
What is the lowest percentage of voice-allocated bandwidth you can select on the WLANcontroller?()
You have very few Cisco 7920 wireless IP phones on your network, but lots of wireless laptops.You want to increase the bandwidth available for the laptops by decreasing the bandwidth reserved forthe Cisco 7920 phones.
What is the lowest percentage of voice-allocated bandwidth you can select ontheWLAN controller?()
You have very few cisco 7920 wireless ip phones on your network, but lots of wireless laptops. You want to increase the bandwidth available for the laptops by decreasing the bandwidth
reserved for the cisco 7920 phones.
What is the lowest percentage of voice-allocated bandwidth you can select on the wlan controller?()
A co-worker is unable to invite you to a Microsoft Windows Meeting Space meeting. You need to receive an invite to the meeting.
What should you do?()
You are the network administrator for Company. to do an unattended installation so you create an Answer.txt file by using Setup Manager. The Answer.txt is copied to a floppy disk and you start the installation on a test computer by booting the computer with the Windows 2000 Professional CD-ROM. You insert the floppy disk after the computer starts. Although you had set the user interaction level to full unattended mode, you are prompted for all the required parameters. You want to ensure that the unattended installation upgrades the Windows 98 computers.
What should you do?()
You are the administrator of Red Lington Enterprises. You want to upgrade 125 computers from Windows NT Workstation 4.0 to Windows 2000 Professional. You create an unattend.txt file by using the setup manager.
You copy the file to a floppy disk. You then start the installation on a computer in the test lab using the Windows 2000 Professional CD-ROM. After the computer starts you insert the floppy disk. Even though you set the user interaction level to full-unattended mode you are prompted for all the configuration parameters. You want to ensure that the unattended installation does not prompt you for input.
What should you do? ()
You are the desktop administrator for your company. You are responsible for automating the deployment of Windows XP Professional to new computers in your company. You are preparing a Windows XP Professional computer, which you will use to test disk imaging. You install Windows XP Professional on the test computer and run the Sysprep utility. You use a third-party software package to create a disk image. You apply the disk image to a new computer and then restart the computer. Instead of completing the Windows XP Professional installation, the computer starts the Windows Welcome program, requiring you to enter additional setup information.
Because you will be deploying a large number of computers, you want to ensure that the disk image can be applied without additional user interaction. What should you do?()
A customer wants to purchase an IBM System Storage DS8700 to support a high-performance database environment.
Which technical solution gives the customer the best relationship between I/O performance at the machine’s backend vs. capacity installed in the machine()
You add an Online Responder to an Online Responder Array. You need to ensure that the new Online Responder resolves synchronization conflicts for all members of the Array.
What should you do()
You add an Online Responder to an Online Responder Array.
You need to ensure that the new Online Responder resolves synchronization conflicts for all members of the Array.
What should you do()
You want to enable the user, Scott, to change to the GRP1 consumer group by issuing the following code:
SQL> EXEC DBMS_SESSION.SWITCH_CURRENT_CONSUMER_GROUP
(’SCOTT’, ’GRP1’, FALSE);
How will you grant the switch privilege to the user, Scott?()
You need to configure a new Company switch to support DTP.
Which DTP switchport mode parameter sets the switch port to actively send and respond to DTP negotiation frames? ()
You are the administrator of your company’s network. You attempt to install a printer driver on a Windows 2000 computer for a user named Linda.
You receive the following error message: "Error 11-Cannot install printer driver."
The driver was originally downloaded from the printer manufacturer’s Web site. You have successfully used the driver in the past on their Windows 2000 Professional computers.
You want to configure Linda’s computer to check for driver integrity and to allow you to install this printer driver.
What should you do? ()
You are the administrator of ExamSheet.net's network.
You attempt to install a video driver on a Windows 2000 Professional computer. You receive the following error message: "Error 11 - Cannot install video driver."
The driver was originally downloaded from the video card manufacturer's Web site. You have successfully used the driver in the past on other Windows 2000 Professional computers. You want to configure the Windows 2000 Professional computer to check for driver integrity and to allow you to install this video driver. What should you do? ()
You are the network administrator for ExamSheet.net. Your network has 210 Windows 2000 Professional computers and eleven Windows 2000 Server computers. Users on the network save their work files in home folders on a network server. The NTFS partition that contains the home folders has Encrypting File System (EFS) enabled. A user named Sandra leaves ExamSheet.net. You decrypt the files for her manager. When the manager attempts to open any of the files, he receives the following error message: "Access is denied." You want the manager to be able to access the files.
What should do? ()
You are working as a Database Administrator. Despite having a password in the data dictionary as change_on_install, you always log on to the database MYNEWDB using operating system authentication. Your organization is planning to recruit two junior-level DBAs. You decide to enable remote authentication in your database so that the new DBAs can log on to the database from their workstations to carry out administrative tasks.
To allow the new DBAs to perform the administrative tasks, you create a password file on the database server using the following command:
ORAPWD file=d:\oracle\ora9i\orapwU01 password=admin entries=4
After creating the password file, you remove the operating system authentication and change the value of the REMOTE_LOGIN_PASSWORDFILE parameter to EXCLUSIVE. You also create a net service name as MYNEWDB that allows the new DBAs to connect to the database server from their workstations using this net service name. Which command must you use to connect to the database to start it?()
You plan to deploy a Virtual Desktop Infrastructure (VDI) for the public relations users.
You need to identify which additional software must be deployed on the network to support the planned VDI deployment.
Which additional software should you identify?()
免费的网站请分享给朋友吧