You experience a loss of the disk on which the USER_DATA tablespace data files are stored. You attempt to recover the data files but discover that the archived redo log file with sequence number 45, which is needed to perform complete recovery, is invalid. You then begin incomplete recovery-You receive this prompt:
ORA-00279:change 309012...03/09/01 11:33:56 needed for thread ORA-00289: suggestion :
/disk1/archive/arch_45.rdo ORA-00280: change 309012 for thread 1 is in sequence #45 Specify log:
{
filename
AUTO
CANCEL}
What is the correct response?()
You need to recommend a solution for controlling access to the Internet.The solution must meet the museum’s security polic.
What should you include in the recommendation?()
You need to recommend a monitoring solution for App1 that meets the museum’s technical requirements.
What should you include in the recommendation?()
You need to recommend a management solution for the corporate Web sites that meets the museum’s security policy
What should you include in the recommendation?()
You create an ASP.NET server control in the SampleControl namespace. The control uses a JavaScript file names Refresh.js to implement AJAX functionality.You need to ensre that the JavaScript file is included in the assembly.
Which two actions should you perform?()
You are designing a top-level OU structure to meet the business and technical requirements.
Which top-evel OU or OUs should you use? ()
You have a computer that runs Windows 7. The computer is in a workgroup. You need to ensure that youcan decrypt Encrypting File System (EFS) files on the computer if you forget your password.
What are two possible ways to achieve this goal?()
You are the administrator of a Windows 2000 network. You use a user account named Hans1 to log on to a Windows 2000 Professional computer named Company1 that is used by different students in a classroom. Hans1 is a user with administrative rights. Another administrator has created a command file named AddUsers.cmd that automatically adds student user accounts. You have scheduled a task on Company1 to run AddUsers.cmd later in the evening. The next day you find that the job did not run. There are no errors reported in the Event Log. You want to schedule a task to successfully run AddUsers.cmd.
What should you do? ()
You are a network administrator for ExamSheet.net's Windows 2000 network.
You use a user account named User1 to log on tot a Windows 2000 Professional computer. The computer is used by different students in a classroom. User1 does not have administrative rights. However, you prefer to use this account for your daily activities. Using the Task Scheduler you schedule a task to run a command file named AddUsers.cmd that automatically adds six more student user accounts. You configure the task to run as the administrator account.
After the task was scheduled to have run you open the Task Scheduler and discover a status of "Could not start" for the task. You also discover account logon failure audit events in the computer's Security log.You want the scheduled task to successfully run AddUsers.cmd. You want to accomplish this with the least amount of administrative effort.
What should you do?()
You work in a company which uses SQL Server 2008. You are the administrator of the company database. Now you are in charge of a SQL Server 2008 instance. The instance has databases for a finance application and a manufacturing application. You want to put some limitation on the maximum CPU query time allowed by the applications, so you configure the Resource Governor to achieve this. But you notice that certain reports do not execute successfully any longer on the manufacturing application. You have to allow the manufacturing application to consume more CPU time, so you have to change the Resource Governor configuration.
Which Resource Governor component should you configure?()
You have a portable computer that runs Windows 7. You configure the computer to enter sleep mode after10 minutes of inactivity. You do not use the computer for 15 minutes and discover that the computer has notentered sleep mode. You need to identify what is preventing the computer from entering sleep mode.
What should you do?()
Your portable computer is in sleep mode. When you resume work on the portable computer, you are not prompted for a password.
You need to ensure that you are prompted for a password each time the portable computer recovers from sleep mode.
What should you do?()
You have a portable computer that runs Windows XP Professional. The computer supports Advanced Configuration and Power Interface (ACPI). You need to ensure that the computer enters Sleep Mode when you close the lid of the computer.
What should you do?()

You administer a Windows 2000 Professional computer that is shared by multiple users. You receive a phone call from one of the users of the shared computer that tells you that the computer is reporting a kernel stop error. You notice that a user has tried to install video drivers that have caused the computer to become unstable. You want to ensure that users can install only the drivers that are approved by the manufacturer.
What should you do? ()
You are designing a Windows 7 deployment image.
You plan to partition the hard disk of each client computer during deployment. You need to modify the unattended answer file by using a text editor.
Where should you add the disk information?()
Your network consists of a single Active Directory forest that contains two domains named contoso.com and litwareinc.com. All domain controllers for contoso.com are in an office located in Singapore. All domain controllers for litwareinc.com are in an office located in Los Angeles.
There is a single 128-Kbps WAN link between the two offices.All domain controllers run Windows Server 2003 Service Pack 2 (SP2) and are configured as DNS servers. Each domain controller contains a standard DNS zone for its respective domain.You need to ensure that users in the Singapore office can resolve IP addresses for servers in the Los Angeles office. The solution must minimize replication traffic over the WAN link.
What should you do?()
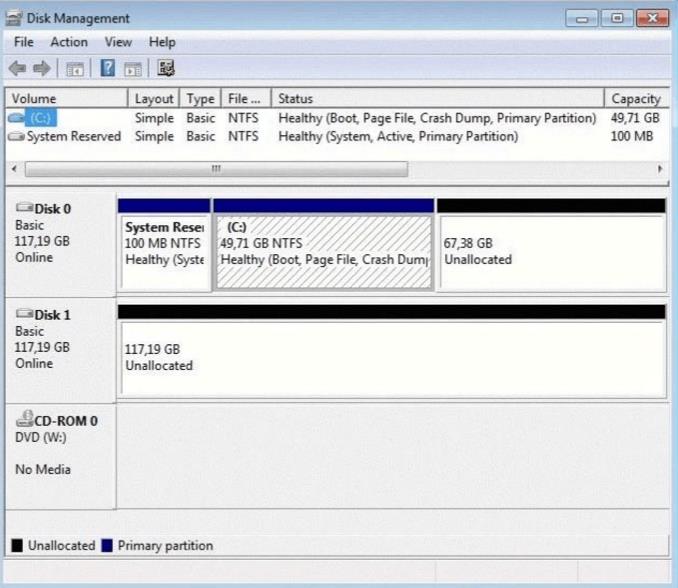
You have a computer that runs Windows 7. Your computer s disk configuration is shown in the exhibit.(Click the Exhibit button.) You need to ensure that you can create a striped volume on the computer.
What should you do?()
You are working on a very large database. You had performed a binary backup of the control file a month ago. After this you added a few tablespaces, and dropped a couple of tablespaces. This morning, due to hardware failure, you lost all your control files.
How would you recover the database from this situation?()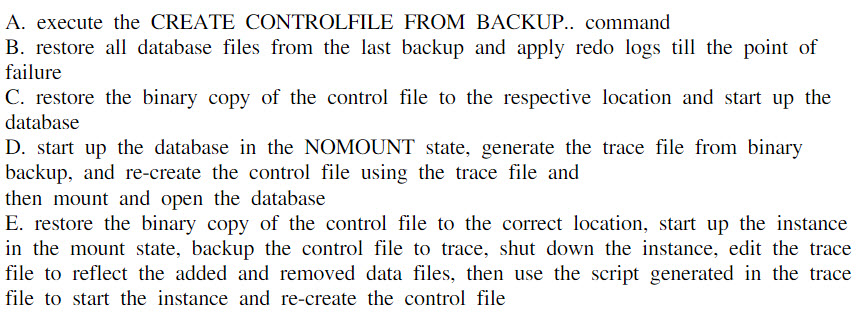
You work in a company which is named Wiikigo Corp. The company uses SQL Server 2008. You are the administrator of the company database. Now you are in charge of a SQL Server 2008 instance. There is a database named DB1 in the instance. In the database, a small percentage of data is modified everyday. Ever day in the morning, you have to create a read-only copy of the database for reporting purposes and make sure that you use as little disk space as possible.
In the options below, which strategy should you use?()
You work in a company which is named Wiikigo Corp. The company uses SQL Server 2008. You are the administrator of the company database. Now you are in charge of a SQL Server 2008 instance. There is a text file which is named SQL01.log on the E: drive. A SQL Server Agent job executes every 2 minutes and logs information to the text file. You get a report from users saying that the sever doesn't make response. As the technical support, you check and find that the SQL Server Agent service does not run and the SQL Server Agent job no longer functions. You have to identify the reason why the SQL Server Agent service is unresponsive.
In the options below, which log should you check? ()
A co-worker is unable to invite you to a Microsoft Windows Meeting Space meeting. You need to receive an invite to the meeting.
What should you do?()
You are designing an automated deployment process for a Windows Azure application.
The process must deploy the application to Windows Azure without any user interaction. You need to recommend a deployment strategy.
What should you recommend?()
You are planning a Windows 7 deployment infrastructure for a new company.
You have the following requirements:
Three domains
10,000 client computers No user interaction
You need to recommend a deployment infrastructure.
What should you recommend?()
Your company has a single Active Directory Domain Services (AD DS) domain and 1,000 Windows 7 computers.
You are planning to deploy a custom application.
You need to schedule the deployment to occur outside of business hours and without user interaction.
Which deployment method should you choose?()
You are the network administrator for Company. to do an unattended installation so you create an Answer.txt file by using Setup Manager. The Answer.txt is copied to a floppy disk and you start the installation on a test computer by booting the computer with the Windows 2000 Professional CD-ROM. You insert the floppy disk after the computer starts. Although you had set the user interaction level to full unattended mode, you are prompted for all the required parameters. You want to ensure that the unattended installation upgrades the Windows 98 computers.
What should you do?()
You are the administrator of Red Lington Enterprises. You want to upgrade 125 computers from Windows NT Workstation 4.0 to Windows 2000 Professional. You create an unattend.txt file by using the setup manager.
You copy the file to a floppy disk. You then start the installation on a computer in the test lab using the Windows 2000 Professional CD-ROM. After the computer starts you insert the floppy disk. Even though you set the user interaction level to full-unattended mode you are prompted for all the configuration parameters. You want to ensure that the unattended installation does not prompt you for input.
What should you do? ()
You are the desktop administrator for your company. You are responsible for automating the deployment of Windows XP Professional to new computers in your company. You are preparing a Windows XP Professional computer, which you will use to test disk imaging. You install Windows XP Professional on the test computer and run the Sysprep utility. You use a third-party software package to create a disk image. You apply the disk image to a new computer and then restart the computer. Instead of completing the Windows XP Professional installation, the computer starts the Windows Welcome program, requiring you to enter additional setup information.
Because you will be deploying a large number of computers, you want to ensure that the disk image can be applied without additional user interaction. What should you do?()
Your company has a single Active Directory directory service domain. All servers in your environment run Windows Server 2003. You have a stand-alone server that serves as a Stand-alone root certification authority (CA). You need to ensure that a specific user can back up the CA and configure the audit parameters on the CA.
What should you do?()
You work as a network technician at. Your boss, Mrs. , is interested in the Spanning Tree Protocol timers.
What can you tell her regarding the default STP timers? ()
You work as a network technician at Company. Your boss, Mrs., is interested in LWAPP (Lightweight Access Point Protocol).
What should you tell her regarding this technology? ()
You have a computer that runs Windows XP Professional. You download new video card driver from the Internet, and then install the driver. You restart the computer. You discover that the newly loaded video driver is named VgaSave.
You need to restore the previous version of the video card driver.What should you do?()
You are the administrator of your company’s network. You attempt to install a printer driver on a Windows 2000 computer for a user named Linda.
You receive the following error message: "Error 11-Cannot install printer driver."
The driver was originally downloaded from the printer manufacturer’s Web site. You have successfully used the driver in the past on their Windows 2000 Professional computers.
You want to configure Linda’s computer to check for driver integrity and to allow you to install this printer driver.
What should you do? ()
You need to recommend a backup solution for the VMs that meets the museum's technical requirements.
What should you include in the recommendation?()
免费的网站请分享给朋友吧