A user is unable to determine the default system text editor.
How can the local administrator assist the user by identifying the default text editor for the system?()
The session of user SCOTT receives the following error after executing an UPDATE command onthe EMP table:
ERROR at line 1:
ORA-00060: deadlock detected while waiting for resource
On investigation, you find that a session opened by user JIM has a transaction that caused the deadlock.
two statements are true regarding the session of SCOTT in this scenario()
User SCOTT wants to perform a bulk insert operation in the EMP_DEP table. SCOTT receives the followingerror after the INSERT statement is issued and few rows are inserted:INSERT INTO EMP_DEP (emp_id,name,salary,dep_name,mgr_id) *ERROR at line 1:
ORA-01653: unable to extend table SCOTT.EMP_DEP by 128 in tablespace USERS Identify two actions eitherof which will help you resolve this problem. ()
A banking user with the userid of ’joe’ is unable to rsh from SYSTEMA to SYSTEMB without having to retype their password, but they can rsh from SYSTEMB to SYSTEMA. No other users are experiencing the same issue.
Both systems have a /home/joe/.rhosts file that contain the proper references to the other host. The /home/joe/.rhosts files on both SYSTEMA and SYSTEMB are owned by userid ’joe’.
Which of the following is the most likely cause of this problem()
You have a computer that runs Windows XP Professional. Two users named User1 and User2 share the computer. User1 and User2 encrypt files on the computer. User1 encrypts a file named file1. doc. You need ensure that both User1 and User2 can view the contents of file1. doc.
What should you instruct User1 to do?()
A customer with a well-known brand wants to make sure they have a Green decision in their next IT infrastructure investment.
How can IBM Cool Blue help this customer? ()
A client has requested an IBM System x solution. Pricing is the most sensitive decision factor. They are looking for 12 TB of storage, with a projected growth of 10-15%. As this is the only server accessing this amount of data, the customer does not require a SAN.
What should the System x Sales Specialist recommend?()
A UNIX customer has a Symmetrix DMX that has crashed three times in the past six months, causing data loss. The customer is shopping for an enterprise storage solution to provide point-in- time copy functionality without a fixed relationship to its primaries.
Which IBM solution best meets this customer’s requirements()
A customer is interested in reducing energy consumption and infrastructure consolidation for space. The customer needs a maximum of 14 servers in 7U rack.
Which IBM BladeCenter Chassis should be recommended? ()
Virtualization is a technology that can help reduce power and cooling requirements. IT organizations can consolidate multiple OS and application stacks on each server with virtualization software.
What IBM solution simplifies virtualization for IBM hardware? ()
A customer has purchased three IBM System Storage DS8700 systems and would like to have their administrators trained.
Which training alternative provides the necessary training with the least financial impact()
You are the administrator of a Windows 2000 network. You use a user account named Hans1 to log on to a Windows 2000 Professional computer named Company1 that is used by different students in a classroom. Hans1 is a user with administrative rights. Another administrator has created a command file named AddUsers.cmd that automatically adds student user accounts. You have scheduled a task on Company1 to run AddUsers.cmd later in the evening. The next day you find that the job did not run. There are no errors reported in the Event Log. You want to schedule a task to successfully run AddUsers.cmd.
What should you do? ()
You are a network administrator for ExamSheet.net's Windows 2000 network.
You use a user account named User1 to log on tot a Windows 2000 Professional computer. The computer is used by different students in a classroom. User1 does not have administrative rights. However, you prefer to use this account for your daily activities. Using the Task Scheduler you schedule a task to run a command file named AddUsers.cmd that automatically adds six more student user accounts. You configure the task to run as the administrator account.
After the task was scheduled to have run you open the Task Scheduler and discover a status of "Could not start" for the task. You also discover account logon failure audit events in the computer's Security log.You want the scheduled task to successfully run AddUsers.cmd. You want to accomplish this with the least amount of administrative effort.
What should you do?()

You administer a Windows 2000 Professional computer that is shared by multiple users. You receive a phone call from one of the users of the shared computer that tells you that the computer is reporting a kernel stop error. You notice that a user has tried to install video drivers that have caused the computer to become unstable. You want to ensure that users can install only the drivers that are approved by the manufacturer.
What should you do? ()
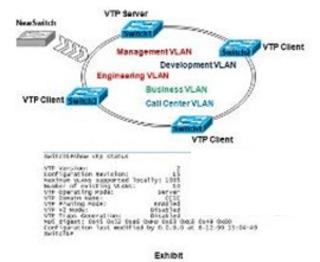
Refer to the exhibit. Users from the Engineering VLAN complain that every time Business VLAN users have a network connectivity issue, the Engineering VLAN users usually have problems experiencing slow response or network connectivity problems. After troubleshooting, an unauthorized switch 2 was found. This unauthorized switch has been a regular problem, assuming the root bridge function under the spanning-tree domain and causing the Engineering VLAN to be unstable. Which three of these actions could be suggested to fix the problem?()
A user is unable to determine the default system text editor.
How can the local administrator assist the user by identifying the default text editor for the system?()
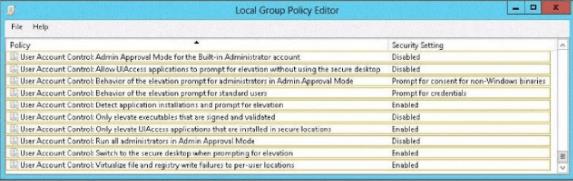
You have a server named Server1. Server1 runs Windows Server 2012 R2. A user named Admin1
is a member of the local Administrators group. You need to ensure that Admin1 receives a User Account Control (UAC) prompt when attempting to open Windows PowerShell as an administrator.
Which setting should you modify from the Local Group Policy Editor? To answer, select the appropriate setting in the answer area.
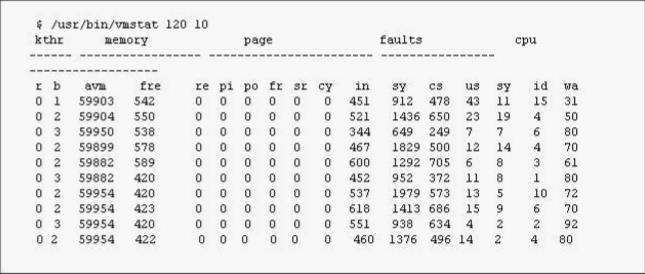
To examine the Exhibit, press the Exhibit button. While a user is compiling a C program, "vmstat 120 10" is run to determine the cause of a performance problem. Given the vmstat output as shown in the exhibit, which of the following conclusions is most appropriate to draw about the machine?()
Companycom wants to buy a new p5 570 running AIX 5.3. The applications require 4 processors and 8GB of memory. There is a requirement to have a Virtual IO Server.
What is the smallest p5 570 that should be sold to this customer?()
You work in a company which is named Wiikigo Corp. The company uses SQL Server 2008. You are the administrator of the company database. Now you are in charge of a SQL Server 2008 instance. There is a text file which is named SQL01.log on the E: drive. A SQL Server Agent job executes every 2 minutes and logs information to the text file. You get a report from users saying that the sever doesn't make response. As the technical support, you check and find that the SQL Server Agent service does not run and the SQL Server Agent job no longer functions. You have to identify the reason why the SQL Server Agent service is unresponsive.
In the options below, which log should you check? ()
Youre performing tablespace point-in-time recovery on a tablespace called USERS. If an object in that tablespace has a foreign key constraint owned by another object in the INDEX_TBS
which statement is true?()
At the request of a user, you issue the following command to restore a dropped table: flashback table "BIN$F2JFfMq8Q5unbC0ceE9eJg==$0" to before drop; Later, the user notifies you that the data in the table seems to be very old and out of date.
What might be the problem?()
A co-worker is unable to invite you to a Microsoft Windows Meeting Space meeting. You need to receive an invite to the meeting.
What should you do?()
A highly available WebLogic cluster in UNIX is configured for automatic server migration. Node Managed is configured on both machines to start managed servers.
How should you simulate a managed server failure to test whether automatic server migration is working?()
A customer would like to share the processor resources automatically between logical partitions.
Which of the following would accomplish this requirement without user interaction? ()
You are planning a Windows 7 deployment infrastructure for a new company.
You have the following requirements:
Three domains
10,000 client computers No user interaction
You need to recommend a deployment infrastructure.
What should you recommend?()
Company.com has a resource group that contains a database that is accessed by a web client based on another system. The communication to the database is TCP/IP. Occasionally after a failure, the end users get unusual error messages that indicate the database server is not available. It has been determined that the web server is trying to access the database server’s information before it has completed file system recovery after a failure.
How can HACMP affect this problem?()
A customer wants to purchase an IBM System Storage DS8700 to support a high-performance database environment.
Which technical solution gives the customer the best relationship between I/O performance at the machine’s backend vs. capacity installed in the machine()
A customer wants to realize a server-based computing scenario for trading floor applications with IBM BladeCenter. The customer expects the solution to offer high security and manageability, while delivering hardware-based graphics compression and full USB capability.
Is this possible?()

Company.com has a non-IBM disk storage unit connected by two Fibre channel connections. The Nodes have multiple connections to the storage device that allow load balancing. A failure with one Fibre adapter or connection will not be noticed by the application, but it needs to be addressed.
How can HACMP help make this environment more robust?()
You are a systems administrator responsible for configuring a Windows Server 2008 SMTP server. Yourorganization is currently using the default SMTP virtual server for sending order notifications from a single Web application called ContosoOrderManagement. Recently, you have noticed that a largenumber of messages have been sent to the SMTP virtual server from other computers and users.
Which two methods can you use to prevent unauthorized access to the SMTP server?()
You executed the following command to drop a user:
DROP USER scott CASCADE;
Which two statements regarding the above command are correct?()
View the Exhibit and examine the privileges granted to the SL_REP user.
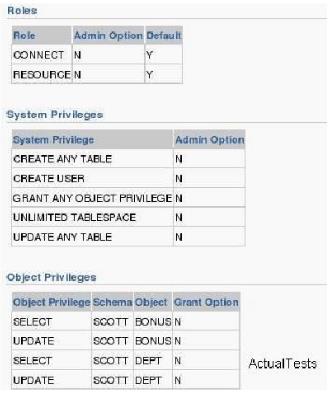
The EMP table is owned by the SCOTT user. The SL_REP user executes the following command: SQL> GRANT SELECT ON scott.emp TO hr;
Which statement describes the outcome of the command()
免费的网站请分享给朋友吧