Evaluate the following command:
SQL>ALTER SYSTEM SET db_securefile = ’IGNORE’;
What is the impact of this setting on the usage of SecureFiles?()
You are responsible for increasing the security within the Company LAN. Of the following choices listed below,
which is true regarding layer 2 security and mitigation techniques? ()
You are the administrator of your company’s network. You attempt to install a printer driver on a Windows 2000 computer for a user named Linda.
You receive the following error message: "Error 11-Cannot install printer driver."
The driver was originally downloaded from the printer manufacturer’s Web site. You have successfully used the driver in the past on their Windows 2000 Professional computers.
You want to configure Linda’s computer to check for driver integrity and to allow you to install this printer driver.
What should you do? ()
You are the network administrator for ExamSheet.net. Your network has 210 Windows 2000 Professional computers and eleven Windows 2000 Server computers. Users on the network save their work files in home folders on a network server. The NTFS partition that contains the home folders has Encrypting File System (EFS) enabled. A user named Sandra leaves ExamSheet.net. You decrypt the files for her manager. When the manager attempts to open any of the files, he receives the following error message: "Access is denied." You want the manager to be able to access the files.
What should do? ()
Your network contains an Active Directory domain. All servers run Windows Server 2008 R2.
You need to audit the deletion of registry keys on each server.
What should you do()
There are 30 managed access points on the wlse. a radio scan is started but fails. Upon
inspection of the device list in the reports tab, you notice a red indicator on the wds access point. upon inspection of the wds access point through its guid, it is discovered that the security keys are not set up between the wds access point and the wlse.
Which of the following is mis configured?()
There are 30 managed access points on the WLSE. A radio scan is started but fails. Upon inspection of the device list in the reports tab, you notice a red indicator on the WDS access point.Upon inspection of the WDS access point through its GUI, it is discovered that the security keys arenot set up between the WDS access point and the WLSE.
Which of the following is misconfigured?()
A customer currently buys HP ProLiant servers and EMC storage. The customer has encountered various problems getting certain servers to work with their storage.
Which of the following arguments can the Sales Specialist present to best position IBM? ()
A customer has installed an IBM System Storage DS8700 with 20 TB of storage, two-way processor version, 32 GB cache, and 16 Fibre Channel ports. The customer is beginning to experience throughput performance issues.
To address this performance consideration with minimal cost to the customer, which of the following should be the FIRST step to resolve the problem()
A current Sun Solaris customer has just purchased their first p5 590. During the Solution Assurance, the backup requirements were discussed.
Which of the following should be recommended to the customer with regards to restoring rootvg?()
Which of the following statements is true regarding the initialization parameter DIAGNOSTIC_DEST?()
The default value is the value of the environment variable $ORACLE_HOME; if $ORACLE_HOME isn’t set
A System p administrator in a manufacturing customer plans to migrate an AIX 5.2 system to a new LPAR on an existing System p using VIOS.
Which of the following must be completed prior to this migration ()
A customer would like to have the ability to permanently activate processor and memory resources as their workload increases.
Which of the following supports the customer requirement?()

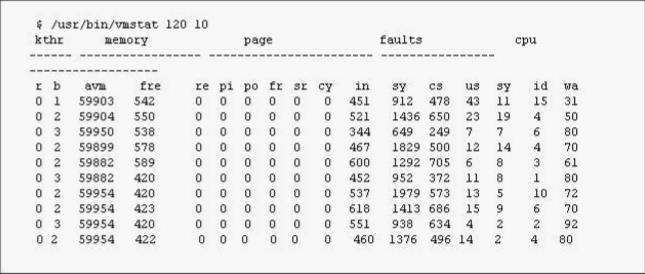
To examine the Exhibit, press the Exhibit button. While a user is compiling a C program, "vmstat 120 10" is run to determine the cause of a performance problem. Given the vmstat output as shown in the exhibit, which of the following conclusions is most appropriate to draw about the machine?()
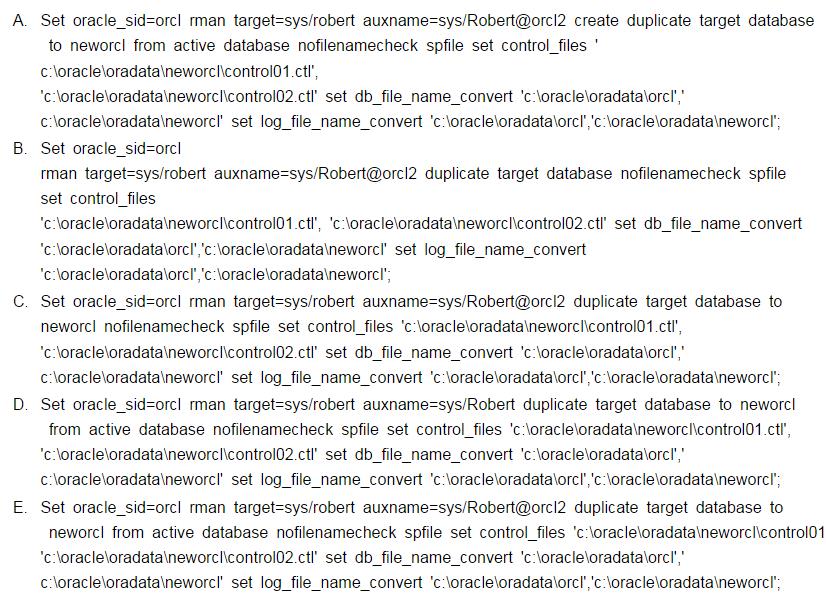
Which of the following commands will perform an active database duplication of the ORCL database to the ORCL2 database?()
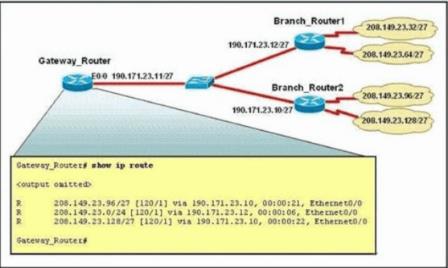
What is the most likely reason for the dispartly between the actual network numbers at the branches and the routes in the routing table on Gateway-Router?()
You have very few Cisco 7920 wireless IP phones on your network, but lots of wireless laptops. You want toincrease the bandwidth available for the laptops by decreasing the bandwidth reserved for the Cisco 7920phones.
What is the lowest percentage of voice-allocated bandwidth you can select on the WLANcontroller?()
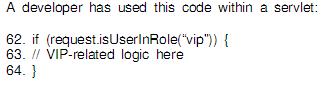
What else must the developer do to ensure that the intended security goal is achieved()?
A customer would like to share the processor resources automatically between logical partitions.
Which of the following would accomplish this requirement without user interaction? ()
You are the network administrator for Company. to do an unattended installation so you create an Answer.txt file by using Setup Manager. The Answer.txt is copied to a floppy disk and you start the installation on a test computer by booting the computer with the Windows 2000 Professional CD-ROM. You insert the floppy disk after the computer starts. Although you had set the user interaction level to full unattended mode, you are prompted for all the required parameters. You want to ensure that the unattended installation upgrades the Windows 98 computers.
What should you do?()
You issued the following RMAN command:
RMAN> CONFIGURE CONTROLFILE AUTOBACKUP ON;
What is NOT an impact of using the above command?()
Evaluate the following command:
SQL>ALTER SYSTEM SET db_securefile = ’IGNORE’;
What is the impact of this setting on the usage of SecureFiles?()
What is the impact of the following backup if it exceeds the duration allowance?()
Backup as compressed backupset duration 2:00 partial minimize load database ;
You issued the following command at the UNIX environment:
% setenv ORA_SDTZ ’OZ_TZ’
What will be the impact of issuing the above command?()
In Recovery Manager (RMAN), you set the retention policy to NONE by executing the following command:
CONFIGURE RETENTION POLICY TO NONE;
What would be the impact of this setting?()
A customer wants to purchase an IBM System Storage DS8700 to support a high-performance database environment.
Which technical solution gives the customer the best relationship between I/O performance at the machine’s backend vs. capacity installed in the machine()
While installing the equipment for a new two-node cluster, it is discovered that the disk subsystem Rack has one connection to the power mains. The explanation given was that the disks are to be mirrored between the two disk drawers in the rack and that a failure in either of the disk drawers would simply result in half of the disk being lost.
What can be done to avoid a single point of failure?()
Kevin, the Software Developer of Perfect Solution Inc., recently left his job. The company's Administrator moves all of his home folder files to his Manager's home folder. The NTFS partition that contains the home folders has the Encrypting File System (EFS) enabled. When the Manager attempts to open Kevin's files, he is denied access.
What should be done, so that the Manager can access those files with least administrative burden? ()
After using the alt_disk_install command to clone a system image to another disk, the system administrator noticed a large number of defined devices not allocated to the LPAR.
Which of the following is the most likely cause of this situation?()
You executed the following command to drop a user:
DROP USER scott CASCADE;
Which two statements regarding the above command are correct?()
Your database is running in ARCHIVELOG mode. The SCOTT.EMP table belongs to the DATA1 tablespace. The junior DBA erroneously runs a script that executes the following statement:
SQL> DROP TABLE SCOTT.EMP PURGE;
After one hour, you are performing the user managed incomplete recovery. Which datafiles will you restore from the last full backup?()
You issued the following command to analyze the SCOTT.EMP table for block corruption:
ANALYZE TABLE SCOTT.EMP VALIDATE STRUCTURE; You received the following error:
ORA-01578: ORACLE data block corrupted (file # %s, block # %s)
How will you resolve the block corruption problem?()
Which statements concerning the relationships between the following classes are true?()
class Foo { int num;
Baz comp = new Baz();
}
class Bar { boolean flag;
}
class Baz extends Foo {
Bar thing = new Bar();
double limit;
}
免费的网站请分享给朋友吧