Company.com has a four-node cluster (nodes ’A’, ’B’, ’C’, and ’D’). The nodes are set up in Resource group pairs. Node ’A’ falls over to Node ’B’, and Node ’C’ falls over to Node ’C’. During a maintenance windows, it was discovered that the six resource groups on Node ’A’ are too much to be adequately handled by Node ’B’.
What could be done to better utilize the available resources during fallover?()
Virtualization is a technology that can help reduce power and cooling requirements. IT organizations can consolidate multiple OS and application stacks on each server with virtualization software.
What IBM solution simplifies virtualization for IBM hardware? ()
You are designing a top-level OU structure to meet the business and technical requirements.
Which top-evel OU or OUs should you use? ()
A customer has purchased three IBM System Storage DS8700 systems and would like to have their administrators trained.
Which training alternative provides the necessary training with the least financial impact()
You are the administrator of a Windows 2000 network. You use a user account named Hans1 to log on to a Windows 2000 Professional computer named Company1 that is used by different students in a classroom. Hans1 is a user with administrative rights. Another administrator has created a command file named AddUsers.cmd that automatically adds student user accounts. You have scheduled a task on Company1 to run AddUsers.cmd later in the evening. The next day you find that the job did not run. There are no errors reported in the Event Log. You want to schedule a task to successfully run AddUsers.cmd.
What should you do? ()
A customer has installed an IBM System Storage DS8700 with 20 TB of storage, two-way processor version, 32 GB cache, and 16 Fibre Channel ports. The customer is beginning to experience throughput performance issues.
To address this performance consideration with minimal cost to the customer, which of the following should be the FIRST step to resolve the problem()
A current Sun Solaris customer has just purchased their first p5 590. During the Solution Assurance, the backup requirements were discussed.
Which of the following should be recommended to the customer with regards to restoring rootvg?()
A customer SAN environment has undergone significant growth over the past two years. They havealso suffered a high turnover rate with administrative personnel. The customer has asked a storage specialist for help in documenting and understanding their changing SAN environment. The ability to make configuration changes to devices would be a plus.
Which tool should the storage specialist suggest()
A customer’s SAN environment has undergone significant growth over the past two years. They have also suffered a high turnover rate with administrative personnel. The customer has asked a storage specialist for help in documenting and understanding their changing SAN environment. The ability to make configuration changes to devices would be a plus.
Which tool should the storage specialist suggest()
You are employed as the Exchange administrator at Company.com.You are in the process of
installing a new Exchange Server 2010 Organization.After the installation you send a text message to an external client and receive the subsequent non-delivery report (NDR): "Delivery has failed to these recipients or groups: [email protected] ([email protected]).The recipient’s e-mail system isn’t accepting messages now.Please try resending this message later or contact the recipient directly." You attempt to e-mail the user from an external e-mail system with great success.To ensure productivity you need to make sure e-mails can be sent to external clients from within the organization.
What should you do?()
You are the administrator of Etechsol.com Enterprises. Your company consists of a small 20-user network. Management has decided to upgrade all computers to Windows 2000.
After having a closer examination of your company’s network, you realize that only half of the network interface cards are Net PC compliant. You decide to create Windows 2000 remote boot floppies.
What executable is used for creating RIS boot disks for non-PXE compliant clients?()
A System p administrator in a manufacturing customer plans to migrate an AIX 5.2 system to a new LPAR on an existing System p using VIOS.
Which of the following must be completed prior to this migration ()
A customer has two Power 770 systems with 4 enclosures each. Thirty two cores and 1TB of memory are activated on each system. Each system has 3 database partitions and each partition has 10 cores and 300GB of memory.
Which solution will provide automated recovery of unplanned outages at least cost?()

You administer a Windows 2000 Professional computer that is shared by multiple users. You receive a phone call from one of the users of the shared computer that tells you that the computer is reporting a kernel stop error. You notice that a user has tried to install video drivers that have caused the computer to become unstable. You want to ensure that users can install only the drivers that are approved by the manufacturer.
What should you do? ()
In a JSP-centric shopping cart application, you need to move a client’s home address of the Customerobject into the shipping address of the Order object. The address data is stored in a value object classcalled Address with properties for: street address, city, province, country, and postal code.
Which two JSPcode snippets can be used to accomplish this goal?()
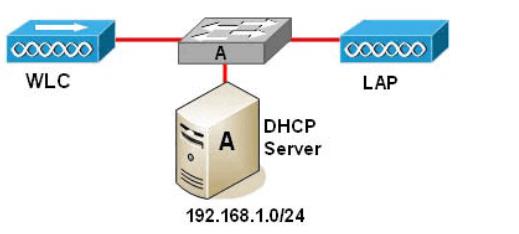
You work as a network technician at Company. Please study the exhibit carefully. In this
Company wireless network, the LAP (lightweight access point) attempts to register to a WLC (Wireless LAN Controller).
What kind of message is transmitted?()
Company.com has a resource group that contains a database that is accessed by a web client based on another system. The communication to the database is TCP/IP. Occasionally after a failure, the end users get unusual error messages that indicate the database server is not available. It has been determined that the web server is trying to access the database server’s information before it has completed file system recovery after a failure.
How can HACMP affect this problem?()
Company.com has a four-node cluster (nodes ’A’, ’B’, ’C’, and ’D’). The nodes are set up in Resource group pairs. Node ’A’ falls over to Node ’B’, and Node ’C’ falls over to Node ’C’. During a maintenance windows, it was discovered that the six resource groups on Node ’A’ are too much to be adequately handled by Node ’B’.
What could be done to better utilize the available resources during fallover?()
A customer wants to purchase an IBM System Storage DS8700 to support a high-performance database environment.
Which technical solution gives the customer the best relationship between I/O performance at the machine’s backend vs. capacity installed in the machine()
While installing the equipment for a new two-node cluster, it is discovered that the disk subsystem Rack has one connection to the power mains. The explanation given was that the disks are to be mirrored between the two disk drawers in the rack and that a failure in either of the disk drawers would simply result in half of the disk being lost.
What can be done to avoid a single point of failure?()
A customer wants to realize a server-based computing scenario for trading floor applications with IBM BladeCenter. The customer expects the solution to offer high security and manageability, while delivering hardware-based graphics compression and full USB capability.
Is this possible?()

Company.com has a non-IBM disk storage unit connected by two Fibre channel connections. The Nodes have multiple connections to the storage device that allow load balancing. A failure with one Fibre adapter or connection will not be noticed by the application, but it needs to be addressed.
How can HACMP help make this environment more robust?()
During Company.com planning session,Company.com presents the details of the current Network design. The network design serves four separate company facilities, each on as separate subnet. As part of a disaster recovery plan, the customer is evaluating the use of HACMP. Specifically, the have reviewed IPAT via IP aliasing and are questioning the number of IP subnets required.
Given the customer’s current configuration,what is the recommended minimum number of IP subnets that would be required?()
A customer with a well-known brand wants to make sure they have a Green decision in their next IT infrastructure investment.
How can IBM Cool Blue help this customer? ()
A client has requested an IBM System x solution. Pricing is the most sensitive decision factor. They are looking for 12 TB of storage, with a projected growth of 10-15%. As this is the only server accessing this amount of data, the customer does not require a SAN.
What should the System x Sales Specialist recommend?()
You are the administrator of your company’s network. You attempt to install a printer driver on a Windows 2000 computer for a user named Linda.
You receive the following error message: "Error 11-Cannot install printer driver."
The driver was originally downloaded from the printer manufacturer’s Web site. You have successfully used the driver in the past on their Windows 2000 Professional computers.
You want to configure Linda’s computer to check for driver integrity and to allow you to install this printer driver.
What should you do? ()
A UNIX customer has a Symmetrix DMX that has crashed three times in the past six months, causing data loss. The customer is shopping for an enterprise storage solution to provide point-in- time copy functionality without a fixed relationship to its primaries.
Which IBM solution best meets this customer’s requirements()
You are the network administrator for ExamSheet.net. Your network has 210 Windows 2000 Professional computers and eleven Windows 2000 Server computers. Users on the network save their work files in home folders on a network server. The NTFS partition that contains the home folders has Encrypting File System (EFS) enabled. A user named Sandra leaves ExamSheet.net. You decrypt the files for her manager. When the manager attempts to open any of the files, he receives the following error message: "Access is denied." You want the manager to be able to access the files.
What should do? ()
A healthcare provider has two applications that they need to redundantly protect in a SAN environment. Their patient record application runs on Oracle 11i and consists of many small, randomly accessed files. The database is kept on three clustered Sun servers and currently uses 30 TB of data space. Their imaging application that retains and manages x-rays, consists of Filenet, CommonStore, and TSM running on an IBM Power750 server, and is currently using 65
TB of data space.
Which of the following disk solutions meets the customer’s requirement()
Company.com has a three-node cluster with six resource groups. There are two resource groups for each node. A new hardware component will be added to one of the nodes. The customer wants to move the resource groups to other nodes,but not necessarily in the normal fallover order. Also,the resource groups must be moved at night when there is no one in the computer center. What can be done so that the resource group is moved at the most convenient normal fallover order. Also,the resource groups must be moved at night when there is no one in the computer center.
What can be done so that the resource group is moved at the most convenient time for the customer?()
Your network contains an Active Directory domain. All servers run Windows Server 2008 R2.
You need to audit the deletion of registry keys on each server.
What should you do()
A customer currently buys HP ProLiant servers and EMC storage. The customer has encountered various problems getting certain servers to work with their storage.
Which of the following arguments can the Sales Specialist present to best position IBM? ()
A customer is interested in reducing energy consumption and infrastructure consolidation for space. The customer needs a maximum of 14 servers in 7U rack.
Which IBM BladeCenter Chassis should be recommended? ()
免费的网站请分享给朋友吧