DPM 812 KEY箱KEY有无传感器属于()

Map接口是键-值对象,即Map中保存Key-value对形式的元素,访问时只能根据每项元素的key来访问其value。key不能重复,value可以重复。
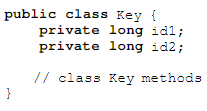 A programmer is developing a class Key, that will be used as a key in a standard java.util.HashMap. Which two methods should be overridden to assure that Key works correctly as a key?()
A programmer is developing a class Key, that will be used as a key in a standard java.util.HashMap. Which two methods should be overridden to assure that Key works correctly as a key?()


 A programmer is developing a class Key, that will be used as a key in a standard java.util.HashMap. Which two methods should be overridden to assure that Key works correctly as a key?()
A programmer is developing a class Key, that will be used as a key in a standard java.util.HashMap. Which two methods should be overridden to assure that Key works correctly as a key?()
免费的网站请分享给朋友吧