A co-worker is unable to invite you to a Microsoft Windows Meeting Space meeting. You need to receive an invite to the meeting.
What should you do?()
Given that Thing is a class, how many objects and reference variables are created by the following code?()
Thing item, stuff;
item = new Thing();
Thing entity = new Thing();
There are 30 managed access points on the wlse. a radio scan is started but fails. Upon
inspection of the device list in the reports tab, you notice a red indicator on the wds access point. upon inspection of the wds access point through its guid, it is discovered that the security keys are not set up between the wds access point and the wlse.
Which of the following is mis configured?()
There are 30 managed access points on the WLSE. A radio scan is started but fails. Upon inspection of the device list in the reports tab, you notice a red indicator on the WDS access point.Upon inspection of the WDS access point through its GUI, it is discovered that the security keys arenot set up between the WDS access point and the WLSE.
Which of the following is misconfigured?()
An administrator performs a Live Partition Mobility operation. After the operation completes, the administrator runs errpt -a.
What is the machine ID reported by errpt command?()
A customer is interested in reducing energy consumption and infrastructure consolidation for space. The customer needs a maximum of 14 servers in 7U rack.
Which IBM BladeCenter Chassis should be recommended? ()
You want to back up your 100-GB database on a remote tape device. You are required to ensure that minimum network bandwidth is consumed while transferring the backups to the tape device.
The current consumption of your CPU is approximately 40 percent.
Which type of backup should you perform?()
You are designing a top-level OU structure to meet the business and technical requirements.
Which top-evel OU or OUs should you use? ()
You have a computer that runs Windows 7. The computer is in a workgroup. You need to ensure that youcan decrypt Encrypting File System (EFS) files on the computer if you forget your password.
What are two possible ways to achieve this goal?()
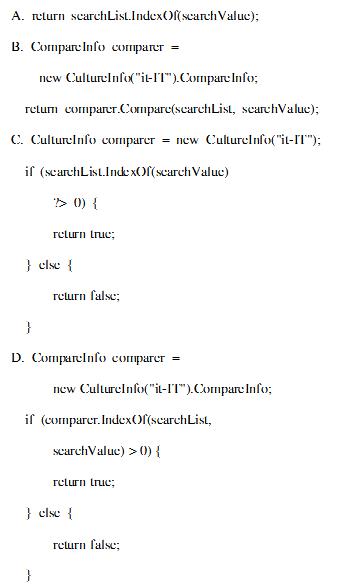
You are developing a method that searches a string for a substring. The method will be localized to Italy. Your method accepts the following parameters:
The string to be searched, which is named searchList
The string for which to search, which is named searchValue You need to write the code.
Which code segment should you use?()
You are the administrator of a Windows 2000 network. You use a user account named Hans1 to log on to a Windows 2000 Professional computer named Company1 that is used by different students in a classroom. Hans1 is a user with administrative rights. Another administrator has created a command file named AddUsers.cmd that automatically adds student user accounts. You have scheduled a task on Company1 to run AddUsers.cmd later in the evening. The next day you find that the job did not run. There are no errors reported in the Event Log. You want to schedule a task to successfully run AddUsers.cmd.
What should you do? ()
An administrator is beginning a set of failover tests. The administrator would like to have clean log files foreach test.
Which command will achieve this?()
A System p administrator in a manufacturing customer plans to migrate an AIX 5.2 system to a new LPAR on an existing System p using VIOS.
Which of the following must be completed prior to this migration ()

You administer a Windows 2000 Professional computer that is shared by multiple users. You receive a phone call from one of the users of the shared computer that tells you that the computer is reporting a kernel stop error. You notice that a user has tried to install video drivers that have caused the computer to become unstable. You want to ensure that users can install only the drivers that are approved by the manufacturer.
What should you do? ()
A user is unable to determine the default system text editor.
How can the local administrator assist the user by identifying the default text editor for the system?()
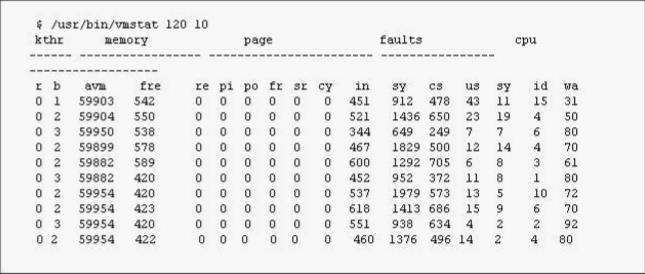
To examine the Exhibit, press the Exhibit button. While a user is compiling a C program, "vmstat 120 10" is run to determine the cause of a performance problem. Given the vmstat output as shown in the exhibit, which of the following conclusions is most appropriate to draw about the machine?()
Companycom wants to buy a new p5 570 running AIX 5.3. The applications require 4 processors and 8GB of memory. There is a requirement to have a Virtual IO Server.
What is the smallest p5 570 that should be sold to this customer?()
You work in a company which is named Wiikigo Corp. The company uses SQL Server 2008. You are the administrator of the company database. Now you are in charge of a SQL Server 2008 instance. There is a database named DB1 in the instance. In the database, a small percentage of data is modified everyday. Ever day in the morning, you have to create a read-only copy of the database for reporting purposes and make sure that you use as little disk space as possible.
In the options below, which strategy should you use?()
You work in a company which is named Wiikigo Corp. The company uses SQL Server 2008. You are the administrator of the company database. Now you are in charge of a SQL Server 2008 instance. There is a text file which is named SQL01.log on the E: drive. A SQL Server Agent job executes every 2 minutes and logs information to the text file. You get a report from users saying that the sever doesn't make response. As the technical support, you check and find that the SQL Server Agent service does not run and the SQL Server Agent job no longer functions. You have to identify the reason why the SQL Server Agent service is unresponsive.
In the options below, which log should you check? ()
Youre performing tablespace point-in-time recovery on a tablespace called USERS. If an object in that tablespace has a foreign key constraint owned by another object in the INDEX_TBS
which statement is true?()
You just completed a manual open database backup. However there seems to be a problem with the database performance. You discover that the database is generating many log switches and the LGWR is consuming lots of CPU time. You have an idea of what the problem is and you begin looking at the information in V$BACKUP and in V$DATAFILE_HEADER.
What do you suspect is the problem?()
A co-worker is unable to invite you to a Microsoft Windows Meeting Space meeting. You need to receive an invite to the meeting.
What should you do?()
A highly available WebLogic cluster in UNIX is configured for automatic server migration. Node Managed is configured on both machines to start managed servers.
How should you simulate a managed server failure to test whether automatic server migration is working?()
An administrator has a Power 570 in default configuration with a 4 port 1 Gbps Integrated Virtual Ethernet (IVE) adapter. A new application requires that the MCS value for the first port group of the IVE adapter be set to 1.
If this change is made what is the maximum number of logical ports, across both port groups,
that the IVE adapter can provide? ()
Company.com has a resource group that contains a database that is accessed by a web client based on another system. The communication to the database is TCP/IP. Occasionally after a failure, the end users get unusual error messages that indicate the database server is not available. It has been determined that the web server is trying to access the database server’s information before it has completed file system recovery after a failure.
How can HACMP affect this problem?()
Given:
11. static class A {
12. void process() throws Exception { throw new Exception(); }
13. }
14. static class B extends A {
15. void process() { System.out.println("B "); }
16. }
17. public static void main(String[] args) {
18. A a = new B();
19. a.process();
20. }
What is the result? ()
11. static classA {
12. void process() throws Exception { throw new Exception(); }
13. }
14. static class B extends A {
15. void process() { System.out.println(”B “); }
16. }
17. public static void main(String[] args) {
18.A a=new B();
19. a.process();
20.}
What is the result?()
One of the key decision making factors in a very competitive opportunity will be cost. Companycom needs an aggregate rPerf rating of 120.
What is the best solution?()
You are working as a DBA on the decision support system. There is a business requirement to track and store all transactions for at least three years for a few tables in the database. Automatic undo management is enabled in the database.
Which configuration should you use to accomplish this task?()
A client has requested an IBM System x solution. Pricing is the most sensitive decision factor. They are looking for 12 TB of storage, with a projected growth of 10-15%. As this is the only server accessing this amount of data, the customer does not require a SAN.
What should the System x Sales Specialist recommend?()
You work as a network technician at. Your boss, Mrs. , is interested in the Spanning Tree Protocol timers.
What can you tell her regarding the default STP timers? ()
You work as a network technician at Company. Your boss, Mrs., is interested in LWAPP (Lightweight Access Point Protocol).
What should you tell her regarding this technology? ()
You work as a network technician at Company. Your boss, Mrs., is interested in the Cisco Compatible Extensions program.
What are three features of this program? ()
免费的网站请分享给朋友吧