The routers named Testking1 and Testking2 are both configured with RIP only.What will happen in the event of Testking1 receiving a routing update that contains a higher cost path to a network already in its routing table?()
You are a network administrator at TestKing, Inc. and you're getting complaintsthat users on the TestKing2 Ethernet network can't access the TestKing1 site. Totroubleshoot this, you begin by looking at the Testking1 and Testking2 routerconfigurations as shown below:

Based on the above output, what is the underlying cause of this problem?()
A CCNA candidate is working on a 2600 Cisco router. The person needs to verify that the configuration register is set to boot the router IOS from flash memory and use the commands saved in the startup-configuration file.
Which command will display this information, and what is the configuration register value that should be displayed?()

You are the network administrator for The network consists of a single Active Directory domain named All servers run Windows Server 2003. All client computers run Windows XP Professional.
You install Software Update Services (SUS) on a network server named Testking1.
When you attempt to synchronize Testking1 with the Windows Update servers, you receive an error message. You suspect that your proxy server requires authentication. You open Internet Explorer and verify that you can communicate with an external Web site by using the proxy server.
You need to ensure that Testking1 can communicate with the Windows Update servers.
What should you do on Testking1?()
You are the network administrator for The network contains a Windows Server 2003 compter named TestKing1. TestKing1 functions as a file server.
Six users in the accounting department use an accounting software application to open files that are stored in a shared folder on TestKing1. The users keep these files open for an extended period of time.
You need to restart TestKing1. You need to find out if any files on Testking1 are open before you restart the computer.
What should you do?()
 If you were to enter the "show interface serial 0" command on router testking1,which of the following will be displayed?()
If you were to enter the "show interface serial 0" command on router testking1,which of the following will be displayed?()

You are the network administrator for TestKing. The network contains a Windows
Server 2003 computer named testking1, which hosts a critical business application
named Salesapp. Testking1 has one disk that contains a single NTFS volume.
Five days ago, the System State of testking1 was backed up, and an Automated
System Recovery (ASR) backup was created. No additional backups were
performed. Subsequently, many changes were made to the Salesapp data files.
You apply an update to the application, which requires you to restart testking1.
Windows startup terminates with a Stop error. You restart the computer and boot
to a floppy disk. A utility on this disk gives you read-only access to the NTFS file
system. You discover that one of the .dll files for the Salesapp application is
corrupted. The corrupted file is stored in the C.\Windows\System32 folder.
You need to restore the corrupted file. You need to avoid losing any changes made
to the data files on testking1.
What should you do onTestKing1?()
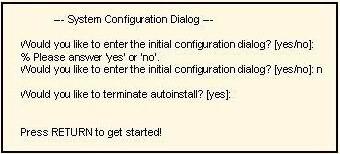
Refer to the exhibit. A network administrator configures a new router and enters the copy startup-config running-config on the router. The network administrator powers down the router and sets it up at a remote location. When the router starts, it enter the system configuration dialog as shown. What is the caust of the problem?()
A company has a Frame Relay WAN with one central - site router and 100 branch office routers. A partial mesh of PVCs exists: one PVC between the central site and each of the 100 branch routers.
Which of the following could be true about the number of EIGRP neighbor ships?()
A company has a Frame Relay WAN with one central - site router and 100 branch office routers. A partial mesh of PVCs exists: one PVC between the central site and each of t he 100 branch routers. All routers use point - to - point subinterfaces and one subnet per PVC.
Which of the following is true about OSPF in this design?()
A company uses Routers R1 and R2 to connect to ISP1 and ISP2, respectively, with Routers I1 and I2 used at th e ISPs. R1 peers with I1 and R2; R2 peers with I2 and R1. R1 and R2 do not share a common subnet, relying on other routers internal to the Enterprise for IP connectivity between the two routers.
Which of the following could be used to prevent potential routing loops in this design?()
免费的网站请分享给朋友吧