Your boss, Miss ,is interested in CEF.
What should you tell her? ()
Your network contains an Active Directory domain. All servers run Windows Server 2008 R2.
You need to audit the deletion of registry keys on each server.
What should you do()
A customer currently buys HP ProLiant servers and EMC storage. The customer has encountered various problems getting certain servers to work with their storage.
Which of the following arguments can the Sales Specialist present to best position IBM? ()
You are the desktop administrator for ExamSheet.
Your Windows 2000 Professional computer is configured to support two monitors. You install a DOS-based application on your computer. The application uses the Windows 2000 Professional default settings Autoexec.nt and Config.nt.
Your primary video adapter is set to 24 bit color, 800 x 600 resolution, and default refresh rates. Your secondary video adapter is set to 32 bit color, 1024 x 768 resolution, and a refresh refresh of 72 hertz. You create a shortcut for the DOS-based application on the secondary monitor's desktop and use the
default PIF settings. You attempt to run the DOS-based application on the secondary monitor. The application opens, but the display area is scrambled. You then attempt to run the DOS-based application on the primary monitor.
The application does not open. Both monitors function correctly when you run Windows based applications.
You want to be able to run the DOS-based application on either monitor.
What should you do?()
Your Windows 2000 Professional computer is configured to support two monitors. You install a DOS-based application on your computer. The application uses the Windows 2000 Professional default settings Autoexec.nt and Config.nt.
Your primary and secondary video adapter are both set to 16-bit color,1024x 768 resolution, and default refresh rates. You create a shortcut for the DOS-based application on the primary monitor’s desktop and use the default PIF settings.
Your attempt to run the DOS-based application on the primary monitor. The application opens, but the display area is scrambled. You then attempt to run the DOS-based application on the secondary monitor. The application does not open. Both monitors function correctly when you run Windows-based applications. What should you do?()
You are peer reviewing a fellow DBAs backup plan for his NOARCHIVELOG mode database, as shown here:
Put the tablespaces in backup mode.
Back up the datafiles for all tablespaces.
Take the tablespaces out of backup mode.
Back up all archived redo logs.
Your colleague asks for you to comment on his plan.
Which response would be correct?()
Your company plans to replace the current virtualization solution by using multiple Hyper-V hosts that run Windows Server 2008 R2 Service Pack 1 (SP1).
You are evaluating the power consumption technologies available in Hyper-V.
You need to identify which technology will reduce the power consumption of the Hyper-V hosts.
Which technology should you identify?()
A customer is interested in reducing energy consumption and infrastructure consolidation for space. The customer needs a maximum of 14 servers in 7U rack.
Which IBM BladeCenter Chassis should be recommended? ()
You want to back up your 100-GB database on a remote tape device. You are required to ensure that minimum network bandwidth is consumed while transferring the backups to the tape device.
The current consumption of your CPU is approximately 40 percent.
Which type of backup should you perform?()
You are designing a top-level OU structure to meet the business and technical requirements.
Which top-evel OU or OUs should you use? ()
A customer has installed an IBM System Storage DS8700 with 20 TB of storage, two-way processor version, 32 GB cache, and 16 Fibre Channel ports. The customer is beginning to experience throughput performance issues.
To address this performance consideration with minimal cost to the customer, which of the following should be the FIRST step to resolve the problem()
A System p administrator in a manufacturing customer plans to migrate an AIX 5.2 system to a new LPAR on an existing System p using VIOS.
Which of the following must be completed prior to this migration ()
You are designing a strategy for migrating to the new environment.
Which two factions from your current environment will affect your migration strategy?()

Your network consists of a single Active Directory forest that contains two domains named contoso.com and litwareinc.com. All domain controllers for contoso.com are in an office located in Singapore. All domain controllers for litwareinc.com are in an office located in Los Angeles.
There is a single 128-Kbps WAN link between the two offices.All domain controllers run Windows Server 2003 Service Pack 2 (SP2) and are configured as DNS servers. Each domain controller contains a standard DNS zone for its respective domain.You need to ensure that users in the Singapore office can resolve IP addresses for servers in the Los Angeles office. The solution must minimize replication traffic over the WAN link.
What should you do?()
Your network consists of a single Active Directory forest. The sales department in your company has 600 Windows Server 2008 R2 servers. You need to recommend a solution to monitor the performance of the 600 servers.
Your solution must meet the following requirements:
èGenerate alerts when the average processor usage is higher than 90 percent for 20 minutes.
èAutomatically adjust the processor monitoring threshold to allow for temporary changes in the workload.
What should you recommend?()
Refer to the exhibit. You would like to guarantee 7 Mb/s for FTP traffic in your LAN, as it seems that peer-to-peer traffic is taking up a large amount of bandwidth. When testing the configuration, you notice that FTP traffic doesn't reach 7 Mb/s. What is the problem?()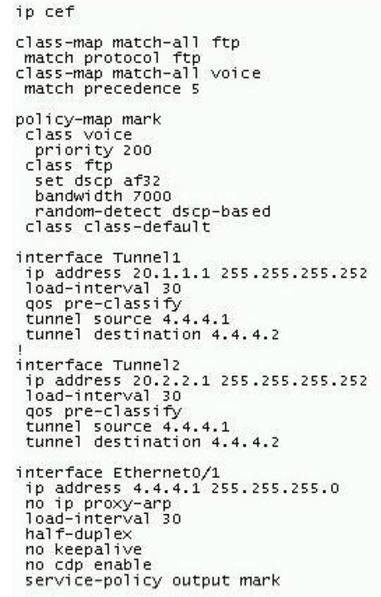
You have very few Cisco 7920 wireless IP phones on your network, but lots of wireless laptops. You want toincrease the bandwidth available for the laptops by decreasing the bandwidth reserved for the Cisco 7920phones.
What is the lowest percentage of voice-allocated bandwidth you can select on the WLANcontroller?()
You have very few Cisco 7920 wireless IP phones on your network, but lots of wireless laptops.You want to increase the bandwidth available for the laptops by decreasing the bandwidth reserved forthe Cisco 7920 phones.
What is the lowest percentage of voice-allocated bandwidth you can select ontheWLAN controller?()
You have very few cisco 7920 wireless ip phones on your network, but lots of wireless laptops. You want to increase the bandwidth available for the laptops by decreasing the bandwidth
reserved for the cisco 7920 phones.
What is the lowest percentage of voice-allocated bandwidth you can select on the wlan controller?()
You have very few Cisco 7920 wireless IP phones on your network, but lots of wireless laptops. Youwant to increase the bandwidth available for the laptops by decreasing the bandwidth reserved forthe Cisco 7920 phones.
What is the lowest percentage of voice-allocated bandwidth you can select onthe WLAN controller?()
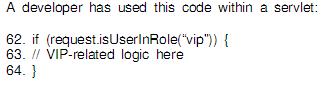
What else must the developer do to ensure that the intended security goal is achieved()?
You are the desktop administrator for your company. You are responsible for automating the deployment of Windows XP Professional to new computers in your company. You are preparing a Windows XP Professional computer, which you will use to test disk imaging. You install Windows XP Professional on the test computer and run the Sysprep utility. You use a third-party software package to create a disk image. You apply the disk image to a new computer and then restart the computer. Instead of completing the Windows XP Professional installation, the computer starts the Windows Welcome program, requiring you to enter additional setup information.
Because you will be deploying a large number of computers, you want to ensure that the disk image can be applied without additional user interaction. What should you do?()
In your database instance, the STATISTICS_LEVEL initialization parameter is set to BASIC.
What isthe impact of this setting()
A customer wants to purchase an IBM System Storage DS8700 to support a high-performance database environment.
Which technical solution gives the customer the best relationship between I/O performance at the machine’s backend vs. capacity installed in the machine()
Your computer has Microsoft Windows Firewall enabled.
Your child plays an online game that uses connectionless traffic over port 5678 for inbound and outbound traffic.
You need to prevent your child from playing this game.
What should you do? ()
You add an Online Responder to an Online Responder Array.
You need to ensure that the new Online Responder resolves synchronization conflicts for all members of the Array.
What should you do()
Your database is running in ARCHIVELOG mode. The SCOTT.EMP table belongs to the DATA1 tablespace. The junior DBA erroneously runs a script that executes the following statement:
SQL> DROP TABLE SCOTT.EMP PURGE;
After one hour, you are performing the user managed incomplete recovery. Which datafiles will you restore from the last full backup?()
Your boss, Miss ,is interested in CEF.
What should you tell her? ()
You work as a network technician at. Your boss, Mrs. , is interested in the Spanning Tree Protocol timers.
What can you tell her regarding the default STP timers? ()
You work as a network technician at Company. Your boss, Mrs., is interested in LWAPP (Lightweight Access Point Protocol).
What should you tell her regarding this technology? ()
You work as a network technician at Company. Your boss, Mrs., is interested in the Cisco Compatible Extensions program.
What are three features of this program? ()
You are the administrator of your company’s network. You attempt to install a printer driver on a Windows 2000 computer for a user named Linda.
You receive the following error message: "Error 11-Cannot install printer driver."
The driver was originally downloaded from the printer manufacturer’s Web site. You have successfully used the driver in the past on their Windows 2000 Professional computers.
You want to configure Linda’s computer to check for driver integrity and to allow you to install this printer driver.
What should you do? ()
You are the network administrator for ExamSheet.net. Your network has 210 Windows 2000 Professional computers and eleven Windows 2000 Server computers. Users on the network save their work files in home folders on a network server. The NTFS partition that contains the home folders has Encrypting File System (EFS) enabled. A user named Sandra leaves ExamSheet.net. You decrypt the files for her manager. When the manager attempts to open any of the files, he receives the following error message: "Access is denied." You want the manager to be able to access the files.
What should do? ()
免费的网站请分享给朋友吧