The user Alice wants to grant all users query privileges on her DEPT table. Which SQL statement accomplishes this? ()
You are a network administrator for Your network consists of a single Active Directory domain named All servers run Windows Server 2003.
A help desk user reports that a user object was accidentally deleted and the user can no longer log on to the domain and access resources. You confirm that the user object was included in the most recent backup.
You need to enable the user to log on to the domain. You must ensure that the user retains access to resources.
What should you do?()



You are the network administrator for . The network consists of a single Active Directory domain named . All servers run Windows Server 2003. All client computers run Windows XP Professional.
The network contains a domain controller named TestKing3. You create a preconfigured user profile on a client computer named TKClient1.
You need to ensure that all users receive the preconfigured user profile when they log on to the network for the first time. All users must still be able to personalize their desktop environments.
What should you do?()
You are the network administrator for TestKing.com. The network consists of a single Active Directory domain named testking.com. All network servers run Windows Server 2003, and all client computers run Windows XP Professional.
All user accounts in the Sales department are located in the Sales organizational unit (OU). You suspect that one or more user accounts in the OU have compromised passwords.
You need to force all users in the Sales department to reset their passwords.
What should you do?()
You create a Web site that is for members only. The Web site allows members to create lists of users that have access to information about member profiles. The name of the list is stored in the listName variable. The user name of the user to whom access is given is stored in the username variable.You need to enable members to manage their lists of users.
Which code segment should you use?()
You are working on a 24X7 database. You want to design a backup strategy for your database that uses user managed backups. You want to be able to perform all backups while the database remains online.
Which statement about performing user-managed backups in a 24x7 environment is true?()
You create a Web Form that contains a button named btnCancel that enables users to exit the page. When users click this button, validation must not occur. During testing you learn that clicking the Cancel button does not enable users to exit the page. You need to ensure that users can always exit the page.
What should you do?()
Your network consists of a single Active Directory domain. All servers run Windows Server 2003 Service
Pack 2 (SP2). All client computers run Windows XP Professional Service Pack 3 (SP3).
A domain user named User1 attempts to log on to a computer named Computer1. After several failed logon
attempts, User1 receives the following error message.
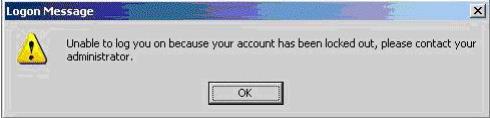
You reset the password for User1 and provide the new password to User1.
You need to ensure that User1 can log on immediately.
What should you do? ()
You are the network administrator for . All network servers run Windows Server 2003. A server named TestKing6 functions as a file server. All client computers run Windows XP Professional and are members of the domain.
TestKing.com periodically hires temporary employees. You need to prepare a custom user profile for all temporary employees.
You log on to a client computer as an administrator, and you configure the desktop settings. You copy the profile to a folder named \\TestKing6\Profiles\Temp_profile.
You rename the Ntuser.dat file in the \\TestKing6\Profiles\Temp_profile folder to Ntuser.man. You create three new user accounts for the temporary employees. The user accounts are named temp_user1, temp_user2, and temp_user3.
You need to configure the temporary user accounts to receive the new desktop settings that you created on TestKing6. The temporary employees must not be allowed to retain customized desktop settings?
What should you do?()
免费的网站请分享给朋友吧