You have an enterprise subordinate certification authority (CA) configured for key archival. Three key recovery agent certificates are issued.
The CA is configured to use two recovery agents.
You need to ensure that all of the recovery agent certificates can be used to recover all new private keys.
What should you do()
You have a Windows Server 2008 R2 Hyper-V server. You take periodic snapshots of your virtual
machines (VMs) when the VMs are not running. You delete several snapshots from the snapshot tree of a VM. The .avhd files that are associated with the deleted snapshots are not deleted from the volume where the VHD files are stored. You need to ensure that the .avhd files are deleted.
What should you do?()
You are designing a top-level OU structure to meet the business and technical requirements.
Which top-evel OU or OUs should you use? ()
You have a computer that runs Windows 7. The computer is in a workgroup. You need to ensure that youcan decrypt Encrypting File System (EFS) files on the computer if you forget your password.
What are two possible ways to achieve this goal?()
You have a single Active Directory directory service forest with one domain. You have an existing top-level organizational unit (OU) named Sales. You are planning to create a new top-level OU named Training. The Sales and Training OUs must have the same security and auditing settings. You need to identify the security permissions and audit settings for the Sales OU so that you can delegate the same permissions for the Training OU.
What should you do first?()
You are the administrator of a Windows XP Professional computer named Pro1. The computer is connected to the Internet. Pro1 provides Internet access to eight other Windows XP Professional computers that are connected to Pro1. You enable Internet Connection Sharing (ICS) and Internet Connection Firewall (ICF) on Pro1. You run an application named App1 on Pro1. App1 communicates with an online training company on the Internet. In order to display an online seminar, the training company needs to contact the App1 application at port 5800. You want to ensure that the training company can connect to the App1 application.
What should you do?()
You are the administrator of a Windows XP Professional computer named Pro1. The computer is connected to the Internet. Pro1 provides Internet access to eight other Windows XP Professional computers that are connected to Pro1. You enable Internet Connection Sharing (ICS) and Windows Firewall on Pro1. You run an application named App1 on Pro1. App1 communicates with an online training company on the Internet. To display an online seminar, the training company needs to contact the App1 application at port 5800. You want to ensure that the training company can connect to the App1 application.
What should you do?()
An administrator is beginning a set of failover tests. The administrator would like to have clean log files foreach test.
Which command will achieve this?()
You are employed as the Exchange administrator at Company.com.You are in the process of
installing a new Exchange Server 2010 Organization.After the installation you send a text message to an external client and receive the subsequent non-delivery report (NDR): "Delivery has failed to these recipients or groups: [email protected] ([email protected]).The recipient’s e-mail system isn’t accepting messages now.Please try resending this message later or contact the recipient directly." You attempt to e-mail the user from an external e-mail system with great success.To ensure productivity you need to make sure e-mails can be sent to external clients from within the organization.
What should you do?()
You work in a company which uses SQL Server 2008. You are the administrator of the company database. Now you are in charge of a SQL Server 2008 instance. The instance has databases for a finance application and a manufacturing application. You want to put some limitation on the maximum CPU query time allowed by the applications, so you configure the Resource Governor to achieve this. But you notice that certain reports do not execute successfully any longer on the manufacturing application. You have to allow the manufacturing application to consume more CPU time, so you have to change the Resource Governor configuration.
Which Resource Governor component should you configure?()
You have a portable computer that runs Windows 7. You configure the computer to enter sleep mode after10 minutes of inactivity. You do not use the computer for 15 minutes and discover that the computer has notentered sleep mode. You need to identify what is preventing the computer from entering sleep mode.
What should you do?()
Your portable computer is in sleep mode. When you resume work on the portable computer, you are not prompted for a password.
You need to ensure that you are prompted for a password each time the portable computer recovers from sleep mode.
What should you do?()
You have a portable computer that runs Windows XP Professional. The computer supports Advanced Configuration and Power Interface (ACPI). You need to ensure that the computer enters Sleep Mode when you close the lid of the computer.
What should you do?()

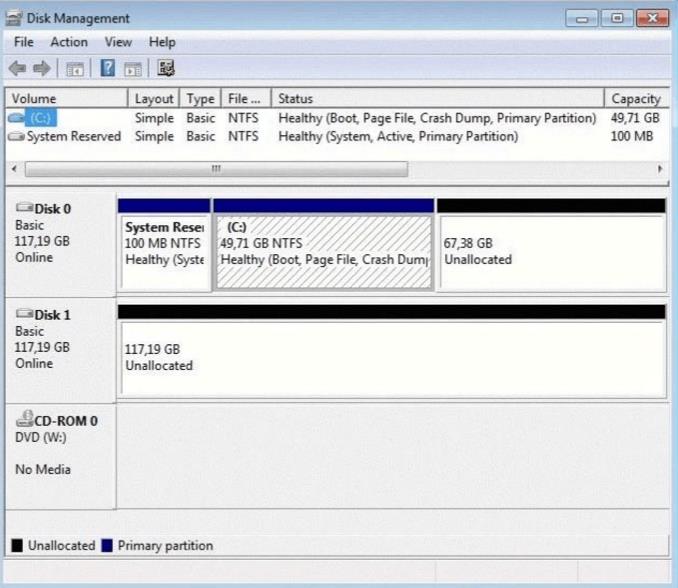
You have a computer that runs Windows 7. Your computer s disk configuration is shown in the exhibit.(Click the Exhibit button.) You need to ensure that you can create a striped volume on the computer.
What should you do?()
You just completed a manual open database backup. However there seems to be a problem with the database performance. You discover that the database is generating many log switches and the LGWR is consuming lots of CPU time. You have an idea of what the problem is and you begin looking at the information in V$BACKUP and in V$DATAFILE_HEADER.
What do you suspect is the problem?()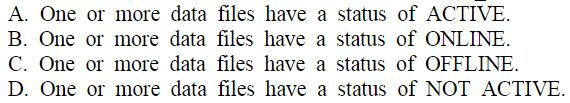
A co-worker is unable to invite you to a Microsoft Windows Meeting Space meeting. You need to receive an invite to the meeting.
What should you do?()
You are designing an automated deployment process for a Windows Azure application.
The process must deploy the application to Windows Azure without any user interaction. You need to recommend a deployment strategy.
What should you recommend?()
You are planning a Windows 7 deployment infrastructure for a new company.
You have the following requirements:
Three domains
10,000 client computers No user interaction
You need to recommend a deployment infrastructure.
What should you recommend?()
You are the network administrator for Company. to do an unattended installation so you create an Answer.txt file by using Setup Manager. The Answer.txt is copied to a floppy disk and you start the installation on a test computer by booting the computer with the Windows 2000 Professional CD-ROM. You insert the floppy disk after the computer starts. Although you had set the user interaction level to full unattended mode, you are prompted for all the required parameters. You want to ensure that the unattended installation upgrades the Windows 98 computers.
What should you do?()
You are the administrator of Red Lington Enterprises. You want to upgrade 125 computers from Windows NT Workstation 4.0 to Windows 2000 Professional. You create an unattend.txt file by using the setup manager.
You copy the file to a floppy disk. You then start the installation on a computer in the test lab using the Windows 2000 Professional CD-ROM. After the computer starts you insert the floppy disk. Even though you set the user interaction level to full-unattended mode you are prompted for all the configuration parameters. You want to ensure that the unattended installation does not prompt you for input.
What should you do? ()
You issued the following RMAN command:
RMAN> CONFIGURE CONTROLFILE AUTOBACKUP ON;
What is NOT an impact of using the above command?()
You add an Online Responder to an Online Responder Array. You need to ensure that the new Online Responder resolves synchronization conflicts for all members of the Array.
What should you do()
You add an Online Responder to an Online Responder Array.
You need to ensure that the new Online Responder resolves synchronization conflicts for all members of the Array.
What should you do()
Your company has a single Active Directory directory service domain. All servers in your environment run Windows Server 2003. You have a stand-alone server that serves as a Stand-alone root certification authority (CA). You need to ensure that a specific user can back up the CA and configure the audit parameters on the CA.
What should you do?()
You have a computer that runs Windows XP Professional. You download new video card driver from the Internet, and then install the driver. You restart the computer. You discover that the newly loaded video driver is named VgaSave.
You need to restore the previous version of the video card driver.What should you do?()
You plan to deploy a Virtual Desktop Infrastructure (VDI) for the public relations users.
You need to identify which additional software must be deployed on the network to support the planned VDI deployment.
Which additional software should you identify?()
You work as an application developer at Certkiller .com. Certkiller .com has given you the task of creating medical billing application that will deal with various insurance vendors.The appropriate assemblies have to be loaded and unloaded dynamically based on the patient’s insurance provider. All of these insurance assemblies are located in C:\Insurance Assemblies.
You have to ensure that when the new application first loads, it has to load allassemblies into a separate application domain. You need to create the child application domain and load all assemblies it using the correct code. What should you do?()
Your network contains an Active Directory domain. All servers run Windows Server 2008 R2.
You need to audit the deletion of registry keys on each server.
What should you do()
You have an enterprise subordinate certification authority (CA) configured for key archival. Three key recovery agent certificates are issued. The CA is configured to use two recovery agents.
You need to ensure that all of the recovery agent certificates can be used to recover all new private keys.
What should you do()
You have an enterprise subordinate certification authority (CA) configured for key archival. Three key recovery agent certificates are issued.
The CA is configured to use two recovery agents.
You need to ensure that all of the recovery agent certificates can be used to recover all new private keys.
What should you do()
根据写作要求,写出一篇作文。
You are Susan. Your company will hold an opening ceremony for a new factory. You are asked to write an invitation letter to David, an important client of your company. The following information should he included:the reasons to invite him; the time for the event;the place for the event;early reply expected.
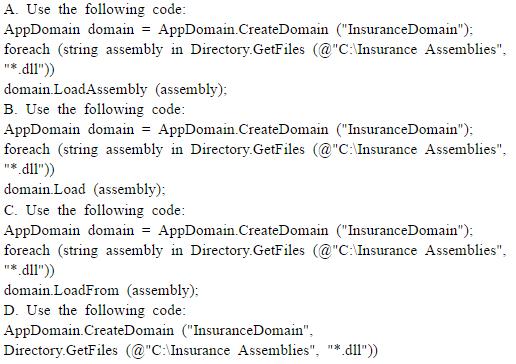
Exhibit, error
You work as a database administrator for Supportcenter.cn. When you try to connect to the database, you get an error (See exhibit). What could be the possible reason for getting such an error?()
You create an ASP.NET server control in the SampleControl namespace. The control uses a JavaScript file names Refresh.js to implement AJAX functionality.You need to ensre that the JavaScript file is included in the assembly.
Which two actions should you perform?()
免费的网站请分享给朋友吧