Your company has several branch offices. Your network consists of a single Active Directory domain.
Each branch office contains domain controllers and member servers. The domain controllers run Windows Server 2003 SP2. The member servers run Windows Server 2008 R2. Physical security of the servers at the branch offices is a concern.
You plan to implement Windows BitLocker Drive Encryption (BitLocker) on the member servers. You need to ensure that you can access the BitLocker volume if the BitLocker keys are corruptedon the member servers. The recovery information must be stored in a central location.
What should you do?()
根据写作要求,写出一篇作文。
You are Susan. Your company will hold an opening ceremony for a new factory. You are asked to write an invitation letter to David, an important client of your company. The following information should he included:the reasons to invite him; the time for the event;the place for the event;early reply expected.
A customer currently buys HP ProLiant servers and EMC storage. The customer has encountered various problems getting certain servers to work with their storage.
Which of the following arguments can the Sales Specialist present to best position IBM? ()
Your company plans to replace the current virtualization solution by using multiple Hyper-V hosts that run Windows Server 2008 R2 Service Pack 1 (SP1).
You are evaluating the power consumption technologies available in Hyper-V.
You need to identify which technology will reduce the power consumption of the Hyper-V hosts.
Which technology should you identify?()
You want to back up your 100-GB database on a remote tape device. You are required to ensure that minimum network bandwidth is consumed while transferring the backups to the tape device.
The current consumption of your CPU is approximately 40 percent.
Which type of backup should you perform?()
A customer has installed an IBM System Storage DS8700 with 20 TB of storage, two-way processor version, 32 GB cache, and 16 Fibre Channel ports. The customer is beginning to experience throughput performance issues.
To address this performance consideration with minimal cost to the customer, which of the following should be the FIRST step to resolve the problem()
A current Sun Solaris customer has just purchased their first p5 590. During the Solution Assurance, the backup requirements were discussed.
Which of the following should be recommended to the customer with regards to restoring rootvg?()
A customer SAN environment has undergone significant growth over the past two years. They havealso suffered a high turnover rate with administrative personnel. The customer has asked a storage specialist for help in documenting and understanding their changing SAN environment. The ability to make configuration changes to devices would be a plus.
Which tool should the storage specialist suggest()
You are employed as the Exchange administrator at Company.com.You are in the process of
installing a new Exchange Server 2010 Organization.After the installation you send a text message to an external client and receive the subsequent non-delivery report (NDR): "Delivery has failed to these recipients or groups: [email protected] ([email protected]).The recipient’s e-mail system isn’t accepting messages now.Please try resending this message later or contact the recipient directly." You attempt to e-mail the user from an external e-mail system with great success.To ensure productivity you need to make sure e-mails can be sent to external clients from within the organization.
What should you do?()
You are the administrator of Etechsol.com Enterprises. Your company consists of a small 20-user network. Management has decided to upgrade all computers to Windows 2000.
After having a closer examination of your company’s network, you realize that only half of the network interface cards are Net PC compliant. You decide to create Windows 2000 remote boot floppies.
What executable is used for creating RIS boot disks for non-PXE compliant clients?()
You are a professional level SQL Server 2005 database administrator in an international corporation named Wiikigo. You are experienced in implementing high-availability solutions, monitoring the database server, and design deployment. In the company, you major job is the deployment, maintenance and support of Microsoft SQL Server 2005. You work as a database administrator for your company. There is a database named Inventory on a SQL Server 2005 computer, and the computer is named SQL01. SQL01 is utilized to aggregate manufacturing part numbers from your company’s trading partners. And the company stores the manufacturing part numbers in the Product table in the Inventory database. The company requests the users to deliver data as text files from each trading partner to SQL1 every night. The data should be imported, and no duplicate manufacturing part numbers should exist in the data which is imported from the text files, and the text files are stored in the Inventory database on SQL01. You should cut the effect on your company’s trading partners and your IT department to the least.
Which action should you perform?()
A customer has two Power 770 systems with 4 enclosures each. Thirty two cores and 1TB of memory are activated on each system. Each system has 3 database partitions and each partition has 10 cores and 300GB of memory.
Which solution will provide automated recovery of unplanned outages at least cost?()
You are designing a strategy for migrating to the new environment.
Which two factions from your current environment will affect your migration strategy?()

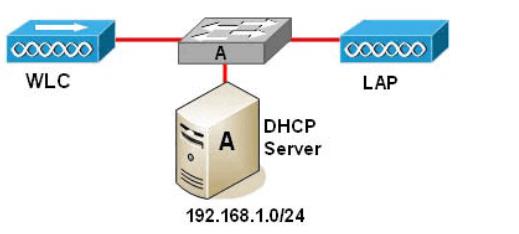
You work as a network technician at Company. Please study the exhibit carefully. In this
Company wireless network, the LAP (lightweight access point) attempts to register to a WLC (Wireless LAN Controller).
What kind of message is transmitted?()
You work in a company which is named Wiikigo Corp. The company uses SQL Server 2008. You are the administrator of the company database. Now you are in charge of a SQL Server 2008 instance. There is a database named DB1 in the instance. In the database, a small percentage of data is modified everyday. Ever day in the morning, you have to create a read-only copy of the database for reporting purposes and make sure that you use as little disk space as possible.
In the options below, which strategy should you use?()
You work in a company which is named Wiikigo Corp. The company uses SQL Server 2008. You are the administrator of the company database. Now you are in charge of a SQL Server 2008 instance. There is a text file which is named SQL01.log on the E: drive. A SQL Server Agent job executes every 2 minutes and logs information to the text file. You get a report from users saying that the sever doesn't make response. As the technical support, you check and find that the SQL Server Agent service does not run and the SQL Server Agent job no longer functions. You have to identify the reason why the SQL Server Agent service is unresponsive.
In the options below, which log should you check? ()
Your network consists of a single Active Directory forest. The sales department in your company has 600 Windows Server 2008 R2 servers. You need to recommend a solution to monitor the performance of the 600 servers.
Your solution must meet the following requirements:
èGenerate alerts when the average processor usage is higher than 90 percent for 20 minutes.
èAutomatically adjust the processor monitoring threshold to allow for temporary changes in the workload.
What should you recommend?()
You have very few Cisco 7920 wireless IP phones on your network, but lots of wireless laptops. You want toincrease the bandwidth available for the laptops by decreasing the bandwidth reserved for the Cisco 7920phones.
What is the lowest percentage of voice-allocated bandwidth you can select on the WLANcontroller?()
Your company has a single Active Directory Domain Services (AD DS) domain and 1,000 Windows 7 computers.
You are planning to deploy a custom application.
You need to schedule the deployment to occur outside of business hours and without user interaction.
Which deployment method should you choose?()
You are the desktop administrator for your company. You are responsible for automating the deployment of Windows XP Professional to new computers in your company. You are preparing a Windows XP Professional computer, which you will use to test disk imaging. You install Windows XP Professional on the test computer and run the Sysprep utility. You use a third-party software package to create a disk image. You apply the disk image to a new computer and then restart the computer. Instead of completing the Windows XP Professional installation, the computer starts the Windows Welcome program, requiring you to enter additional setup information.
Because you will be deploying a large number of computers, you want to ensure that the disk image can be applied without additional user interaction. What should you do?()
Company.com has a resource group that contains a database that is accessed by a web client based on another system. The communication to the database is TCP/IP. Occasionally after a failure, the end users get unusual error messages that indicate the database server is not available. It has been determined that the web server is trying to access the database server’s information before it has completed file system recovery after a failure.
How can HACMP affect this problem?()
Kevin, the Software Developer of Perfect Solution Inc., recently left his job. The company's Administrator moves all of his home folder files to his Manager's home folder. The NTFS partition that contains the home folders has the Encrypting File System (EFS) enabled. When the Manager attempts to open Kevin's files, he is denied access.
What should be done, so that the Manager can access those files with least administrative burden? ()
Your computer has Microsoft Windows Firewall enabled.
Your child plays an online game that uses connectionless traffic over port 5678 for inbound and outbound traffic.
You need to prevent your child from playing this game.
What should you do? ()
Company.com has a non-IBM disk storage unit connected by two Fibre channel connections. The Nodes have multiple connections to the storage device that allow load balancing. A failure with one Fibre adapter or connection will not be noticed by the application, but it needs to be addressed.
How can HACMP help make this environment more robust?()
Your company has a single Active Directory directory service domain. All servers in your environment run Windows Server 2003. You have a stand-alone server that serves as a Stand-alone root certification authority (CA). You need to ensure that a specific user can back up the CA and configure the audit parameters on the CA.
What should you do?()
Your boss, Miss ,is interested in CEF.
What should you tell her? ()
You work as a network technician at Company. Your boss, Mrs., is interested in LWAPP (Lightweight Access Point Protocol).
What should you tell her regarding this technology? ()
You work as a network technician at Company. Your boss, Mrs., is interested in the Cisco Compatible Extensions program.
What are three features of this program? ()
You need to configure a new Company switch to support DTP.
Which DTP switchport mode parameter sets the switch port to actively send and respond to DTP negotiation frames? ()
You are the administrator of your company’s network. You attempt to install a printer driver on a Windows 2000 computer for a user named Linda.
You receive the following error message: "Error 11-Cannot install printer driver."
The driver was originally downloaded from the printer manufacturer’s Web site. You have successfully used the driver in the past on their Windows 2000 Professional computers.
You want to configure Linda’s computer to check for driver integrity and to allow you to install this printer driver.
What should you do? ()
You are the network administrator for ExamSheet.net. Your network has 210 Windows 2000 Professional computers and eleven Windows 2000 Server computers. Users on the network save their work files in home folders on a network server. The NTFS partition that contains the home folders has Encrypting File System (EFS) enabled. A user named Sandra leaves ExamSheet.net. You decrypt the files for her manager. When the manager attempts to open any of the files, he receives the following error message: "Access is denied." You want the manager to be able to access the files.
What should do? ()
Your network contains an Active Directory domain. All servers run Windows Server 2008 R2.
You need to audit the deletion of registry keys on each server.
What should you do()
You are the administrator of your company's network. A user named David runs Windows 2000 Professional on his portable computer. David wants to be able to work at home on files that he created at the office and stored on the company network. Prior to logging off the network and leaving the office, David enables offline files.
David calls you from home and reports that copies of his folders and files on the network are not available on his portable computer. What should you instruct David to do, so that he can proceed with his work?()
免费的网站请分享给朋友吧