Cer-tech .com has a server named Server01.Server01 runs Windows Server 2008.A web server(IIS) roleis also installed on Server01.A public website is hosted on Server01.While monitoring the traffic on thepublic site,you notice an unusual high volume of traffic on the website. You need to find the source of thetraffic.
What should you do to achieve this objective?()
Your network contains an Active Directory domain. All servers run Windows Server 2008 R2.
You need to audit the deletion of registry keys on each server.
What should you do()
A customer currently buys HP ProLiant servers and EMC storage. The customer has encountered various problems getting certain servers to work with their storage.
Which of the following arguments can the Sales Specialist present to best position IBM? ()
You are the network administrator for the Paris branch office of Fourth Coffee.The Paris office has a Windows Server 2003 DNS server named Server10. Server10 hosts a DNS primary zone named fourthcoffee.com. All computers in the Paris office are configured to use Server10 as their preferred DNS server. The Berlin branch office of Fourth Coffee has a UNIX DNS server named Server11. Server11 hosts a primary zone named engineering.fourthcoffee.com. The refresh interval of the engineering.fourthcoffee.com zone is set to 24 hours. In the Berlin office, a firewall filters all incoming network traffic from other offices. A rule on this firewall prevents all computers from the Paris office network, except Server10, from performing DNS lookups against Server11.There is a business requirement that no delay should occur between the time that a new record is created in the engineering.fourthcoffee.com zone and the time that the record can be resolved from any computers in the Paris office. All computers in the Paris office must be able to resolve names in the engineering.fourthcoffee.com namespace.You need to configure DNS on Server10 to meet the requirements.
What should you do?()
Given:
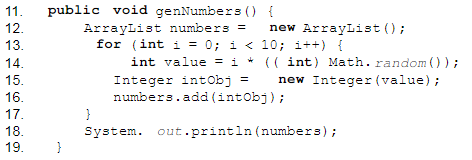
Which line of code marks the earliest point that an object referenced by intObj becomes a candidate for garbage collection?()
Which line of code marks the earliest point that an object referenced by intObj becomes a candidate for garbage collection?()

A customer has installed an IBM System Storage DS8700 with 20 TB of storage, two-way processor version, 32 GB cache, and 16 Fibre Channel ports. The customer is beginning to experience throughput performance issues.
To address this performance consideration with minimal cost to the customer, which of the following should be the FIRST step to resolve the problem()
A current Sun Solaris customer has just purchased their first p5 590. During the Solution Assurance, the backup requirements were discussed.
Which of the following should be recommended to the customer with regards to restoring rootvg?()
You work as a senior administrator at ABC.com. The ABC.com network consists of a single domain named ABC.com. All servers on the ABC.com network have Windows Server 2012 R2 installed.
You are running a training exercise for junior administrators. You are currently discussing the Windows Firewall with Advanced Security feature.
Which of the following is TRUE with regards to Windows Firewall with Advanced Security?()
A customer SAN environment has undergone significant growth over the past two years. They havealso suffered a high turnover rate with administrative personnel. The customer has asked a storage specialist for help in documenting and understanding their changing SAN environment. The ability to make configuration changes to devices would be a plus.
Which tool should the storage specialist suggest()
You are employed as the Exchange administrator at Company.com.You are in the process of
installing a new Exchange Server 2010 Organization.After the installation you send a text message to an external client and receive the subsequent non-delivery report (NDR): "Delivery has failed to these recipients or groups: [email protected] ([email protected]).The recipient’s e-mail system isn’t accepting messages now.Please try resending this message later or contact the recipient directly." You attempt to e-mail the user from an external e-mail system with great success.To ensure productivity you need to make sure e-mails can be sent to external clients from within the organization.
What should you do?()
A System p administrator in a manufacturing customer plans to migrate an AIX 5.2 system to a new LPAR on an existing System p using VIOS.
Which of the following must be completed prior to this migration ()
A customer has two Power 770 systems with 4 enclosures each. Thirty two cores and 1TB of memory are activated on each system. Each system has 3 database partitions and each partition has 10 cores and 300GB of memory.
Which solution will provide automated recovery of unplanned outages at least cost?()

You administer a Windows 2000 Professional computer that is shared by multiple users. You receive a phone call from one of the users of the shared computer that tells you that the computer is reporting a kernel stop error. You notice that a user has tried to install video drivers that have caused the computer to become unstable. You want to ensure that users can install only the drivers that are approved by the manufacturer.
What should you do? ()
Your network consists of a single Active Directory forest that contains two domains named contoso.com and litwareinc.com. All domain controllers for contoso.com are in an office located in Singapore. All domain controllers for litwareinc.com are in an office located in Los Angeles.
There is a single 128-Kbps WAN link between the two offices.All domain controllers run Windows Server 2003 Service Pack 2 (SP2) and are configured as DNS servers. Each domain controller contains a standard DNS zone for its respective domain.You need to ensure that users in the Singapore office can resolve IP addresses for servers in the Los Angeles office. The solution must minimize replication traffic over the WAN link.
What should you do?()
The switched LAN is shown below:
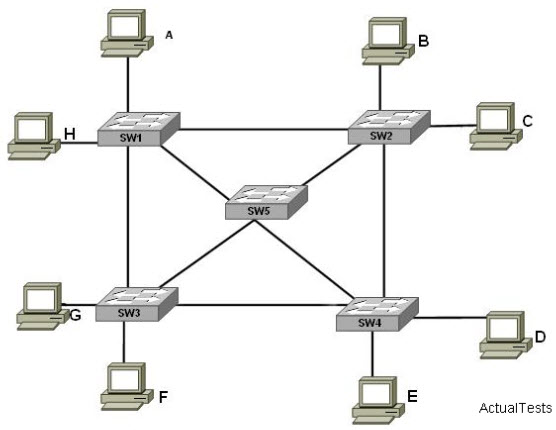
Study the exhibit above carefully. Switch SW5 is configured as the root switch for VLAN 10 but notfor VLAN 20. If the STP configuration is correct, what will be true about Switch SW5?()
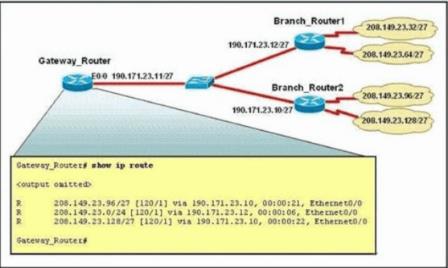
What is the most likely reason for the dispartly between the actual network numbers at the branches and the routes in the routing table on Gateway-Router?()
You have very few Cisco 7920 wireless IP phones on your network, but lots of wireless laptops. You want toincrease the bandwidth available for the laptops by decreasing the bandwidth reserved for the Cisco 7920phones.
What is the lowest percentage of voice-allocated bandwidth you can select on the WLANcontroller?()
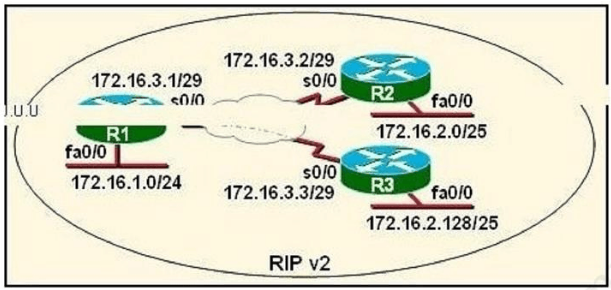
S0/0 on R1 is configured as a multipoint interface to communicate with R2 and R3 in the hub-and-spoke Frame Relay topology shown in the exhibit. Originally, static routes were configured between these routers to successfully route traffic between the attached networks. What will need to be done in order to use RIPv2 in place of the static routes?()
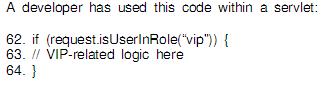
What else must the developer do to ensure that the intended security goal is achieved()?
You work as an administrator at ABC.com. The ABC.com network consists of a single domain named ABC.com. All servers on the ABC.com network have Windows Server 2012 R2 installed. ABC.com has its headquarters in London, and several widespread satellite offices. When ABC.com releases a new written policy stating that the graphical user interface (GUI) should not be installed on any servers deployed to ABC.com’s satellite offices.It is reported that a server in one of the satellite offices are not compliant with the new written policy. You are required to remedy the situation, while using the least amount of user interaction.
Which of the following actions should you take?()
Cer-tech .com has a server named Server01.Server01 runs Windows Server 2008.A web server(IIS) roleis also installed on Server01.A public website is hosted on Server01.While monitoring the traffic on thepublic site,you notice an unusual high volume of traffic on the website. You need to find the source of thetraffic.
What should you do to achieve this objective?()
Company.com has a resource group that contains a database that is accessed by a web client based on another system. The communication to the database is TCP/IP. Occasionally after a failure, the end users get unusual error messages that indicate the database server is not available. It has been determined that the web server is trying to access the database server’s information before it has completed file system recovery after a failure.
How can HACMP affect this problem?()
A customer wants to purchase an IBM System Storage DS8700 to support a high-performance database environment.
Which technical solution gives the customer the best relationship between I/O performance at the machine’s backend vs. capacity installed in the machine()
While installing the equipment for a new two-node cluster, it is discovered that the disk subsystem Rack has one connection to the power mains. The explanation given was that the disks are to be mirrored between the two disk drawers in the rack and that a failure in either of the disk drawers would simply result in half of the disk being lost.
What can be done to avoid a single point of failure?()
Kevin, the Software Developer of Perfect Solution Inc., recently left his job. The company's Administrator moves all of his home folder files to his Manager's home folder. The NTFS partition that contains the home folders has the Encrypting File System (EFS) enabled. When the Manager attempts to open Kevin's files, he is denied access.
What should be done, so that the Manager can access those files with least administrative burden? ()
A customer wants to realize a server-based computing scenario for trading floor applications with IBM BladeCenter. The customer expects the solution to offer high security and manageability, while delivering hardware-based graphics compression and full USB capability.
Is this possible?()

Company.com has a non-IBM disk storage unit connected by two Fibre channel connections. The Nodes have multiple connections to the storage device that allow load balancing. A failure with one Fibre adapter or connection will not be noticed by the application, but it needs to be addressed.
How can HACMP help make this environment more robust?()
You work as the enterprise exchange administrator at TestKing.com. TestKing.com makes use of
Microsoft Exchange Server messaging solution. The TestKing.com network consists of a single ActiveDirectory domain named testking.com.
TestKing.com has its headquarters in Chicago and a branch office in Dallas. Both offices are an ActiveDirectory site that is connected via high speed WAN link. The employees in these offices connect locallyto the servers in these offices.
You are planning to install Exchange Server 2010; however, you need to plan the installation of theMailbox servers with the following criteria:
* It should maintain user access to mailboxes from a server in their site, if a Mailbox server fails.
* Remote mailboxes should bei accessible if a site fails.* Use the minimum amount of serves.
What should you do?()
User SCOTT executes the following command on the EMP table but has not issued COMMIT, ROLLBACK,or any data definition language (DDL) command:
SQL> SELECT job FROM emp
2 WHERE job=’CLERK’ FOR UPDATE OF empno;
SCOTT has opened another session to work with the database. Which three operations would wait when issued in SCOTT’s second session?()
User SCOTT executes the following command on the EMP table but has not issued COMMIT, ROLLBACK, or any data definition language (DDL) command: SQL> SELECT ename FROM emp
2 WHERE job=’CLERK’ FOR UPDATE OF empno;
SCOTT has opened another session to work with the database instance.
Which three operations wouldwait when issued in SCOTT’s second session()
You are the network administrator for ExamSheet.net. Your network has 210 Windows 2000 Professional computers and eleven Windows 2000 Server computers. Users on the network save their work files in home folders on a network server. The NTFS partition that contains the home folders has Encrypting File System (EFS) enabled. A user named Sandra leaves ExamSheet.net. You decrypt the files for her manager. When the manager attempts to open any of the files, he receives the following error message: "Access is denied." You want the manager to be able to access the files.
What should do? ()
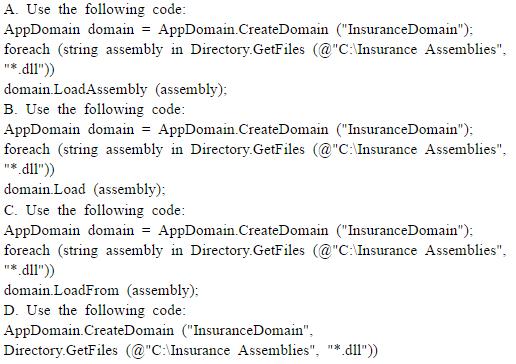
You work as an application developer at Certkiller .com. Certkiller .com has given you the task of creating medical billing application that will deal with various insurance vendors.The appropriate assemblies have to be loaded and unloaded dynamically based on the patient’s insurance provider. All of these insurance assemblies are located in C:\Insurance Assemblies.
You have to ensure that when the new application first loads, it has to load allassemblies into a separate application domain. You need to create the child application domain and load all assemblies it using the correct code. What should you do?()
免费的网站请分享给朋友吧