Kevin, the Software Developer of Perfect Solution Inc., recently left his job. The company's Administrator moves all of his home folder files to his Manager's home folder. The NTFS partition that contains the home folders has the Encrypting File System (EFS) enabled. When the Manager attempts to open Kevin's files, he is denied access.
What should be done, so that the Manager can access those files with least administrative burden? ()
You plan to deploy a Virtual Desktop Infrastructure (VDI) for the public relations users.
You need to identify which additional software must be deployed on the network to support the planned VDI deployment.
Which additional software should you identify?()
根据写作要求,写出一篇作文。
You are Susan. Your company will hold an opening ceremony for a new factory. You are asked to write an invitation letter to David, an important client of your company. The following information should he included:the reasons to invite him; the time for the event;the place for the event;early reply expected.
You are implementing a read-only page that includes the following controls.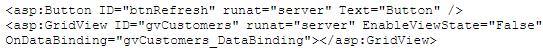
You disable view state to improve performance. You need to ensure that the page is updated to display the latest data when the user clicks the refresh button. Which code segment should you use?()
You have a Windows Server 2008 R2 Hyper-V server. You take periodic snapshots of your virtual
machines (VMs) when the VMs are not running. You delete several snapshots from the snapshot tree of a VM. The .avhd files that are associated with the deleted snapshots are not deleted from the volume where the VHD files are stored. You need to ensure that the .avhd files are deleted.
What should you do?()
Companycom has seven days of vmstat data on four p5 590 production LPARs of four processors each. The data shows that all four LPARs have periodic utilizations of 90-95% lasting several minutes in duration. However, the average utilizations of the four LPARs were between 15-30%. The vmstat data shows that the peak utilizations of each LPAR do not occur at the same time.
Which of the following should be set up?()
You want to back up your 100-GB database on a remote tape device. You are required to ensure that minimum network bandwidth is consumed while transferring the backups to the tape device.
The current consumption of your CPU is approximately 40 percent.
Which type of backup should you perform?()
You are designing a top-level OU structure to meet the business and technical requirements.
Which top-evel OU or OUs should you use? ()
You have a single Active Directory directory service forest with one domain. You have an existing top-level organizational unit (OU) named Sales. You are planning to create a new top-level OU named Training. The Sales and Training OUs must have the same security and auditing settings. You need to identify the security permissions and audit settings for the Sales OU so that you can delegate the same permissions for the Training OU.
What should you do first?()
Given the following RMAN commands,choose the option that reflects the order required to restore your currently operational ARCHIVELOG-mode database.()
a. restore database
b. recover database
c. shutdown immediate
d. startup
e. restore archivelog all
f. alter database open
You are employed as the Exchange administrator at Company.com.You are in the process of
installing a new Exchange Server 2010 Organization.After the installation you send a text message to an external client and receive the subsequent non-delivery report (NDR): "Delivery has failed to these recipients or groups: [email protected] ([email protected]).The recipient’s e-mail system isn’t accepting messages now.Please try resending this message later or contact the recipient directly." You attempt to e-mail the user from an external e-mail system with great success.To ensure productivity you need to make sure e-mails can be sent to external clients from within the organization.
What should you do?()
You have a portable computer that runs Windows XP Professional. The computer supports Advanced Configuration and Power Interface (ACPI). You need to ensure that the computer enters Sleep Mode when you close the lid of the computer.
What should you do?()
You are designing a strategy for migrating to the new environment.
Which two factions from your current environment will affect your migration strategy?()

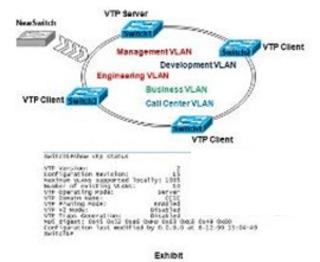
Refer to the exhibit. Users from the Engineering VLAN complain that every time Business VLAN users have a network connectivity issue, the Engineering VLAN users usually have problems experiencing slow response or network connectivity problems. After troubleshooting, an unauthorized switch 2 was found. This unauthorized switch has been a regular problem, assuming the root bridge function under the spanning-tree domain and causing the Engineering VLAN to be unstable. Which three of these actions could be suggested to fix the problem?()
A user is unable to determine the default system text editor.
How can the local administrator assist the user by identifying the default text editor for the system?()
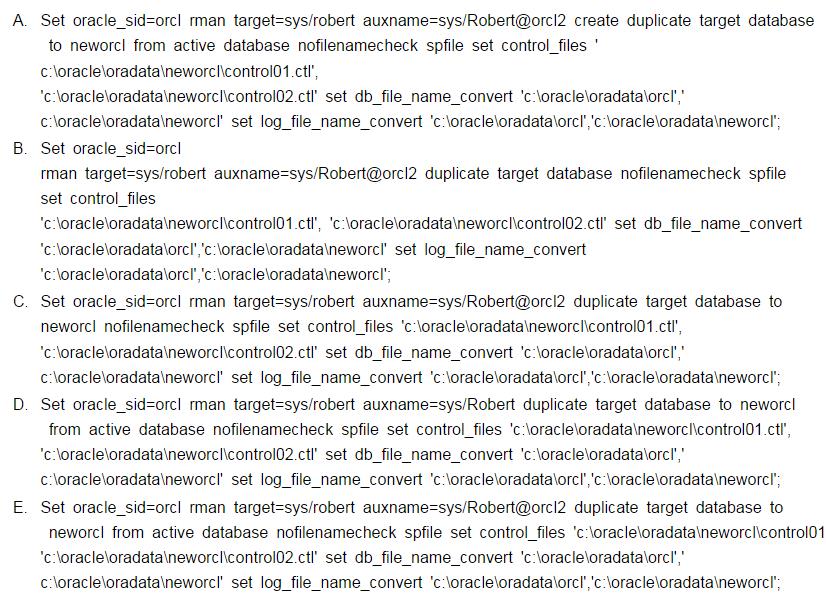
Which of the following commands will perform an active database duplication of the ORCL database to the ORCL2 database?()
You need to recommend a backup strategy for the servers in the San Francisco office. The strategy must meet the company's technical requirements
What should you include in the recommendation?()
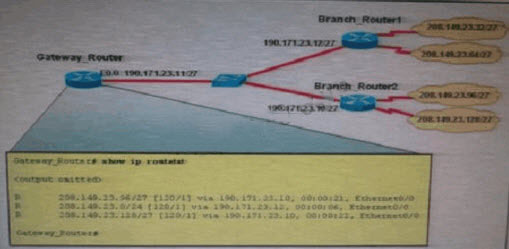
What is the most likely reason for the dispartly between the actual network numbers at the branches and the routes in the routing table on Gateway-Router?()
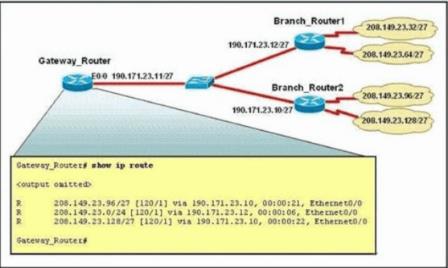
What is the most likely reason for the dispartly between the actual network numbers at the branches andthe routes in the routing table on Gateway-Router?()
Youre performing tablespace point-in-time recovery on a tablespace called USERS. If an object in that tablespace has a foreign key constraint owned by another object in the INDEX_TBS
which statement is true?()
You have a very few Cisco 7920 wireless IP phones on your network, but lots of wireless laptops.You want to increase the bandwidth available for the laptops by decreasing the bandwidth reserved for the Cisco 7920 phones.
What is the lowest percentage of voice-allocated bandwidthyou can select on the WLAN controller?()
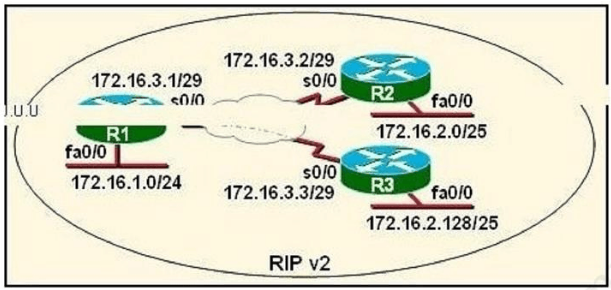
S0/0 on R1 is configured as a multipoint interface to communicate with R2 and R3 in the hub-and-spoke Frame Relay topology shown in the exhibit. Originally, static routes were configured between these routers to successfully route traffic between the attached networks. What will need to be done in order to use RIPv2 in place of the static routes?()
You are the network administrator for Company. to do an unattended installation so you create an Answer.txt file by using Setup Manager. The Answer.txt is copied to a floppy disk and you start the installation on a test computer by booting the computer with the Windows 2000 Professional CD-ROM. You insert the floppy disk after the computer starts. Although you had set the user interaction level to full unattended mode, you are prompted for all the required parameters. You want to ensure that the unattended installation upgrades the Windows 98 computers.
What should you do?()
You are the administrator of Red Lington Enterprises. You want to upgrade 125 computers from Windows NT Workstation 4.0 to Windows 2000 Professional. You create an unattend.txt file by using the setup manager.
You copy the file to a floppy disk. You then start the installation on a computer in the test lab using the Windows 2000 Professional CD-ROM. After the computer starts you insert the floppy disk. Even though you set the user interaction level to full-unattended mode you are prompted for all the configuration parameters. You want to ensure that the unattended installation does not prompt you for input.
What should you do? ()
You are the desktop administrator for your company. You are responsible for automating the deployment of Windows XP Professional to new computers in your company. You are preparing a Windows XP Professional computer, which you will use to test disk imaging. You install Windows XP Professional on the test computer and run the Sysprep utility. You use a third-party software package to create a disk image. You apply the disk image to a new computer and then restart the computer. Instead of completing the Windows XP Professional installation, the computer starts the Windows Welcome program, requiring you to enter additional setup information.
Because you will be deploying a large number of computers, you want to ensure that the disk image can be applied without additional user interaction. What should you do?()
A customer has a 4-core POWER6 570 with 4 partitions and a 2-port 1Gbps Integrated Virtual Ethernet (IVE) Adapter. They are having problems with throughput on the Ethernet adapter and want to improve performance.
Which of the following solutions will help the customer with this issue for the least cost and with the least interruption?()
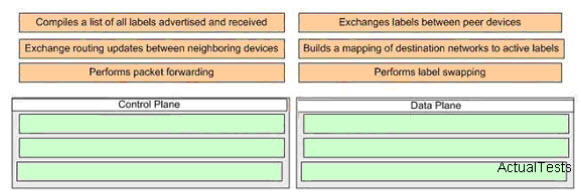
Drag and drop question. The upper gives the MPLS functions, the bottom describes the planes.
Drag the above items to the proper location at the below
Kevin, the Software Developer of Perfect Solution Inc., recently left his job. The company's Administrator moves all of his home folder files to his Manager's home folder. The NTFS partition that contains the home folders has the Encrypting File System (EFS) enabled. When the Manager attempts to open Kevin's files, he is denied access.
What should be done, so that the Manager can access those files with least administrative burden? ()
You add an Online Responder to an Online Responder Array. You need to ensure that the new Online Responder resolves synchronization conflicts for all members of the Array.
What should you do()
Companycom recently ordered a p5 570 and an HMC. Prior to delivery, two additional p5 570 servers were added to the order. Upon installation, the system administrator noticed that they do not have a method to connect the p5 570 servers to the HMC.
Which of the following will allow them to connect all servers to the HMC?()
Which of the following commands should be used to open a tty port configured in the /etc/uucp/Devices file as:
Direct tty2 - 9600 direct
in debug mode, ignoring modem control signal data carrier detect (DCD)?()
You have a computer that runs Windows XP Professional. You download new video card driver from the Internet, and then install the driver. You restart the computer. You discover that the newly loaded video driver is named VgaSave.
You need to restore the previous version of the video card driver.What should you do?()
You are the newly appointed system administrator at Certkiller.com. You are in the process ofcreating a Microsoft ASP.NET application using Microsoft .NET Framework v3.5.
The new application will make use of eleven themes. Certkiller clients will be permitted to selecttheir themes from the Web page. You need to make sure that the theme selected by a client isdisplayed when the client returns to the application. This should occur even when the client returnsto log on at a later date or from another workstation.
You should take cognizance of the fact that the application operates on different storage types andin different environments. Management wants you tp store the themes selected by the clients aswell as retrieving the required theme.
What should you do?()
免费的网站请分享给朋友吧