Given the Tag:
Assuming the tag referenced by my Tags: get Advice uses the Classic event model,
which is true?()
Given:
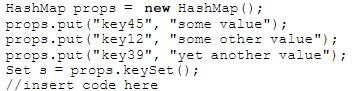
What, inserted at line 39, will sort the keys in the props HashMap?()
Your network contains an Active Directory domain. All servers run Windows Server 2008 R2.
You need to audit the deletion of registry keys on each server.
What should you do()
There are 30 managed access points on the wlse. a radio scan is started but fails. Upon
inspection of the device list in the reports tab, you notice a red indicator on the wds access point. upon inspection of the wds access point through its guid, it is discovered that the security keys are not set up between the wds access point and the wlse.
Which of the following is mis configured?()
There are 30 managed access points on the WLSE. A radio scan is started but fails. Upon inspection of the device list in the reports tab, you notice a red indicator on the WDS access point.Upon inspection of the WDS access point through its GUI, it is discovered that the security keys arenot set up between the WDS access point and the WLSE.
Which of the following is misconfigured?()
A customer currently buys HP ProLiant servers and EMC storage. The customer has encountered various problems getting certain servers to work with their storage.
Which of the following arguments can the Sales Specialist present to best position IBM? ()
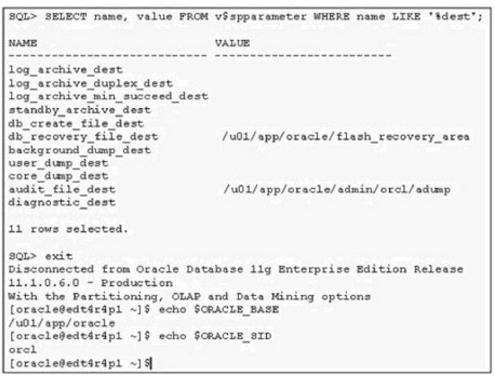
You want to check the details of few errors that users have reported. You search for the alert log file andexecute few commands to find the location of the alert log file. View the Exhibit and check the commandsexecuted.
What is the location of the alert_orcl.log file()
The sl:shoppingList and sl:item tags output a shopping list to the response and are used as follows:
12.<sl:item name="Bread" />
13.<sl:item name="Milk" />
14.<sl:item name="Eggs" />
15.</sl:shoppingList>
The tag handler for sl:shoppingList is ShoppingListTag and the tag handler for sl:item is ItemSimpleTag.ShoppingListTag extends BodyTagSupport and ItemSimpleTag extends SimpleTagSupport.Which is true?()
Given:
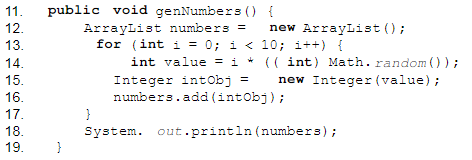
Which line of code marks the earliest point that an object referenced by intObj becomes a candidate for garbage collection?()
A customer has installed an IBM System Storage DS8700 with 20 TB of storage, two-way processor version, 32 GB cache, and 16 Fibre Channel ports. The customer is beginning to experience throughput performance issues.
To address this performance consideration with minimal cost to the customer, which of the following should be the FIRST step to resolve the problem()
You are responsible for implementing maintenance jobs on a SQL Server 2005 database server. Certain jobs run every Sunday and other jobs run at the beginning of every month. You need to schedule the jobs in the way that uses the least amount of administrative effort.
What should you do?()
A current Sun Solaris customer has just purchased their first p5 590. During the Solution Assurance, the backup requirements were discussed.
Which of the following should be recommended to the customer with regards to restoring rootvg?()
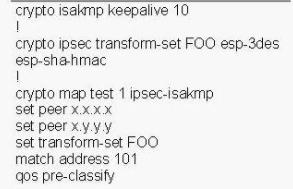
Refer to the exhibit. Given the configuration on a Teleworker router, and knowing it was in the process of being booted, what statement would best describe the order in which the head-end peers would be selected?()

You administer a Windows 2000 Professional computer that is shared by multiple users. You receive a phone call from one of the users of the shared computer that tells you that the computer is reporting a kernel stop error. You notice that a user has tried to install video drivers that have caused the computer to become unstable. You want to ensure that users can install only the drivers that are approved by the manufacturer.
What should you do? ()
In a JSP-centric shopping cart application, you need to move a client’s home address of the Customerobject into the shipping address of the Order object. The address data is stored in a value object classcalled Address with properties for: street address, city, province, country, and postal code.
Which two JSPcode snippets can be used to accomplish this goal?()
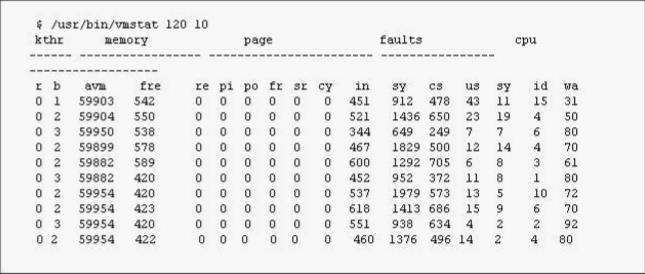
To examine the Exhibit, press the Exhibit button. While a user is compiling a C program, "vmstat 120 10" is run to determine the cause of a performance problem. Given the vmstat output as shown in the exhibit, which of the following conclusions is most appropriate to draw about the machine?()
You work in a company which is named Wiikigo Corp. The company uses SQL Server 2008. You are the administrator of the company database. Now you are in charge of a SQL Server 2008 instance. There is a database named DB1 in the instance. In the database, a small percentage of data is modified everyday. Ever day in the morning, you have to create a read-only copy of the database for reporting purposes and make sure that you use as little disk space as possible.
In the options below, which strategy should you use?()
You work in a company which is named Wiikigo Corp. The company uses SQL Server 2008. You are the administrator of the company database. Now you are in charge of a SQL Server 2008 instance. There is a text file which is named SQL01.log on the E: drive. A SQL Server Agent job executes every 2 minutes and logs information to the text file. You get a report from users saying that the sever doesn't make response. As the technical support, you check and find that the SQL Server Agent service does not run and the SQL Server Agent job no longer functions. You have to identify the reason why the SQL Server Agent service is unresponsive.
In the options below, which log should you check? ()
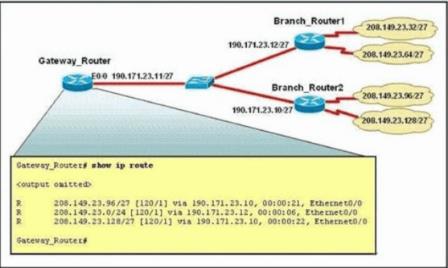
What is the most likely reason for the dispartly between the actual network numbers at the branches and the routes in the routing table on Gateway-Router?()
You have very few Cisco 7920 wireless IP phones on your network, but lots of wireless laptops. You want toincrease the bandwidth available for the laptops by decreasing the bandwidth reserved for the Cisco 7920phones.
What is the lowest percentage of voice-allocated bandwidth you can select on the WLANcontroller?()
You have very few cisco 7920 wireless ip phones on your network, but lots of wireless laptops. You want to increase the bandwidth available for the laptops by decreasing the bandwidth
reserved for the cisco 7920 phones.
What is the lowest percentage of voice-allocated bandwidth you can select on the wlan controller?()
You have very few Cisco 7920 wireless IP phones on your network, but lots of wireless laptops. Youwant to increase the bandwidth available for the laptops by decreasing the bandwidth reserved forthe Cisco 7920 phones.
What is the lowest percentage of voice-allocated bandwidth you can select onthe WLAN controller?()
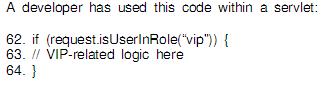
What else must the developer do to ensure that the intended security goal is achieved()?
You are the network administrator for Company. to do an unattended installation so you create an Answer.txt file by using Setup Manager. The Answer.txt is copied to a floppy disk and you start the installation on a test computer by booting the computer with the Windows 2000 Professional CD-ROM. You insert the floppy disk after the computer starts. Although you had set the user interaction level to full unattended mode, you are prompted for all the required parameters. You want to ensure that the unattended installation upgrades the Windows 98 computers.
What should you do?()
A customer wants to purchase an IBM System Storage DS8700 to support a high-performance database environment.
Which technical solution gives the customer the best relationship between I/O performance at the machine’s backend vs. capacity installed in the machine()
While installing the equipment for a new two-node cluster, it is discovered that the disk subsystem Rack has one connection to the power mains. The explanation given was that the disks are to be mirrored between the two disk drawers in the rack and that a failure in either of the disk drawers would simply result in half of the disk being lost.
What can be done to avoid a single point of failure?()
Kevin, the Software Developer of Perfect Solution Inc., recently left his job. The company's Administrator moves all of his home folder files to his Manager's home folder. The NTFS partition that contains the home folders has the Encrypting File System (EFS) enabled. When the Manager attempts to open Kevin's files, he is denied access.
What should be done, so that the Manager can access those files with least administrative burden? ()
You add an Online Responder to an Online Responder Array.
You need to ensure that the new Online Responder resolves synchronization conflicts for all members of the Array.
What should you do()
Your database is running in ARCHIVELOG mode. The SCOTT.EMP table belongs to the DATA1 tablespace. The junior DBA erroneously runs a script that executes the following statement:
SQL> DROP TABLE SCOTT.EMP PURGE;
After one hour, you are performing the user managed incomplete recovery. Which datafiles will you restore from the last full backup?()
Given the Tag:
Assuming the tag referenced by my Tags: get Advice uses the Classic event model,
which is true?()
You are the administrator of your company’s network. You attempt to install a printer driver on a Windows 2000 computer for a user named Linda.
You receive the following error message: "Error 11-Cannot install printer driver."
The driver was originally downloaded from the printer manufacturer’s Web site. You have successfully used the driver in the past on their Windows 2000 Professional computers.
You want to configure Linda’s computer to check for driver integrity and to allow you to install this printer driver.
What should you do? ()
You are the network administrator for ExamSheet.net. Your network has 210 Windows 2000 Professional computers and eleven Windows 2000 Server computers. Users on the network save their work files in home folders on a network server. The NTFS partition that contains the home folders has Encrypting File System (EFS) enabled. A user named Sandra leaves ExamSheet.net. You decrypt the files for her manager. When the manager attempts to open any of the files, he receives the following error message: "Access is denied." You want the manager to be able to access the files.
What should do? ()
What is the end result of these commands if they are successful?()
RMAN> show retention policy;
RMAN configuration parameters for database with db_unique_name
ORCL are: CONFIGURE RETENTION POLICY TO REDUNDANCY 1; # default
Backup database tag=gold_copy plus archivelog tag=gold_copy delete input; Backup
database tag=silver_copy plus archivelog tag=silver_copy delete input;
免费的网站请分享给朋友吧