Exhibit, One of the important tables in the USERStablespace was dropped and purged from the recycle bin at 9:00 a.m. You noticed this at 11:00 a.m. and you want to perform an incomplete recovery to recover the table. Which statement is true?()
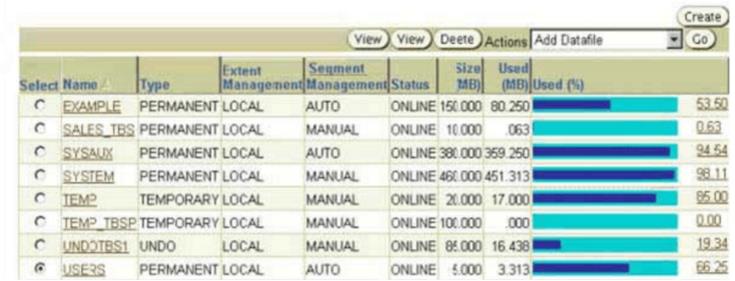
Exhibit:
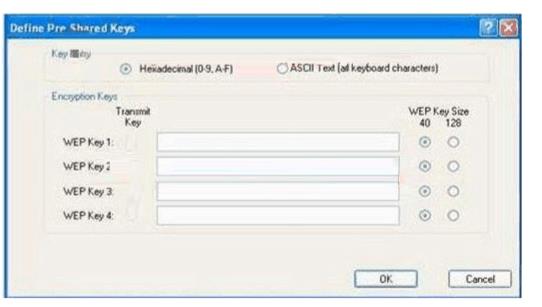
You work as a network technician at. Study the exhibit carefully. You are required configure the static WEP keys on the wireless client adapter using the Cisco ADU (Aironet Desktop Utility).
What should you have in mind when doing this?()
There are 30 managed access points on the wlse. a radio scan is started but fails. Upon
inspection of the device list in the reports tab, you notice a red indicator on the wds access point. upon inspection of the wds access point through its guid, it is discovered that the security keys are not set up between the wds access point and the wlse.
Which of the following is mis configured?()
There are 30 managed access points on the WLSE. A radio scan is started but fails. Upon inspection of the device list in the reports tab, you notice a red indicator on the WDS access point.Upon inspection of the WDS access point through its GUI, it is discovered that the security keys arenot set up between the WDS access point and the WLSE.
Which of the following is misconfigured?()
Exhibit, error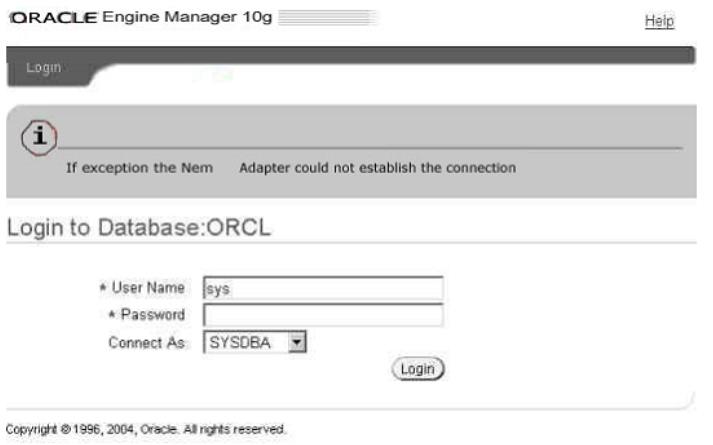
You work as a database administrator for Supportcenter.cn. When you try to connect to the database, you get an error (See exhibit). What could be the possible reason for getting such an error?()
You want to check the details of few errors that users have reported. You search for the alert log fileand execute few commands to find the location of the alert log file. View the Exhibit and check the commands executed.

What is the location of the alert_orcl.log file()
You want to check the details of few errors that users have reported. You search for the alert log file andexecute few commands to find the location of the alert log file. View the Exhibit and check the commandsexecuted.
What is the location of the alert_orcl.log file()
Companycom has seven days of vmstat data on four p5 590 production LPARs of four processors each. The data shows that all four LPARs have periodic utilizations of 90-95% lasting several minutes in duration. However, the average utilizations of the four LPARs were between 15-30%. The vmstat data shows that the peak utilizations of each LPAR do not occur at the same time.
Which of the following should be set up?()
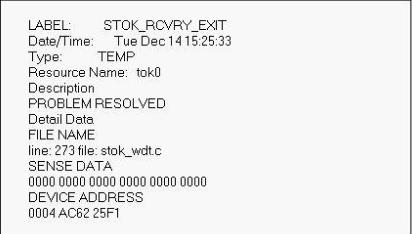
To examine the Exhibit, press the Exhibit button. Which option would produce this output from the errpt command? ()
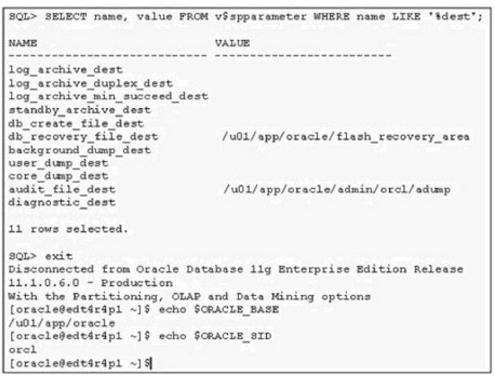
Which of the following statements is true regarding the initialization parameter DIAGNOSTIC_DEST?()
The default value is the value of the environment variable $ORACLE_HOME; if $ORACLE_HOME isn’t set
You are using an Automatic Storage Management (ASM) instance to manage the files of your production database. While studying the parameter file of the ASM instance, you find the following entry:
ASM_DISKSTRING = /devices/*
What could be the reason for this setting?()
Refer to the exhibit. Given the configuration on a Teleworker router, and knowing it was in the process of being booted, what statement would best describe the order in which the head-end peers would be selected?()

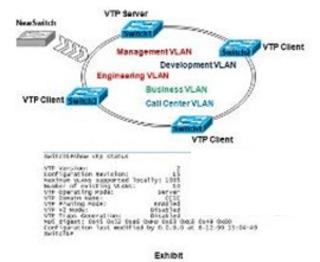
Refer to the exhibit. Users from the Engineering VLAN complain that every time Business VLAN users have a network connectivity issue, the Engineering VLAN users usually have problems experiencing slow response or network connectivity problems. After troubleshooting, an unauthorized switch 2 was found. This unauthorized switch has been a regular problem, assuming the root bridge function under the spanning-tree domain and causing the Engineering VLAN to be unstable. Which three of these actions could be suggested to fix the problem?()
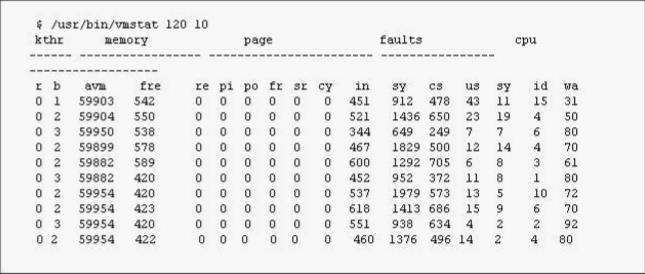
To examine the Exhibit, press the Exhibit button. While a user is compiling a C program, "vmstat 120 10" is run to determine the cause of a performance problem. Given the vmstat output as shown in the exhibit, which of the following conclusions is most appropriate to draw about the machine?()
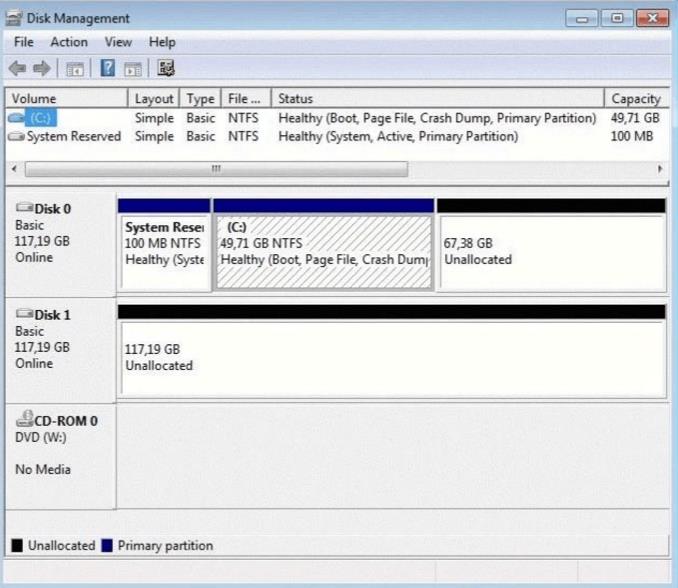
You have a computer that runs Windows 7. Your computer s disk configuration is shown in the exhibit.(Click the Exhibit button.) You need to ensure that you can create a striped volume on the computer.
What should you do?()
Click the Exhibit button.
What is the result?()

You are building a dating web site. The client’s date of birth is collected along with lots of other information.You have created an EL function with the signature:
calcAge(java.util.Date):int and it is assigned to the name, age, in the namespace, funct. In one of your JSPsyou need to print a special message to clients who are younger than 25.
Which EL code snippet will returntrue for this condition?()
Evaluate the following command:
SQL>ALTER SYSTEM SET db_securefile = ’IGNORE’;
What is the impact of this setting on the usage of SecureFiles?()
A customer has a Power 750 with the following: One processor card with 8 cores enabled, and 64GB RAM installed One GX+ adapter with one I/O drawer attached; One 4-port 1Gbps IVE adapterPowerVM Standard Edition; They need to add a GX++ adapter and cable it to an I/O drawer.
Which of the following must also be ordered?()

You work as a network engineer for . You study the exhibit carefully. Three switches are configured for HSRP. Switch1 remains in the HSRP listen state.
What is the most likely cause of this status?()
While installing the equipment for a new two-node cluster, it is discovered that the disk subsystem Rack has one connection to the power mains. The explanation given was that the disks are to be mirrored between the two disk drawers in the rack and that a failure in either of the disk drawers would simply result in half of the disk being lost.
What can be done to avoid a single point of failure?()
After using the alt_disk_install command to clone a system image to another disk, the system administrator noticed a large number of defined devices not allocated to the LPAR.
Which of the following is the most likely cause of this situation?()
Exhibit, One of the important tables in the USERStablespace was dropped and purged from the recycle bin at 9:00 a.m. You noticed this at 11:00 a.m. and you want to perform an incomplete recovery to recover the table. Which statement is true?()

View the Exhibit.
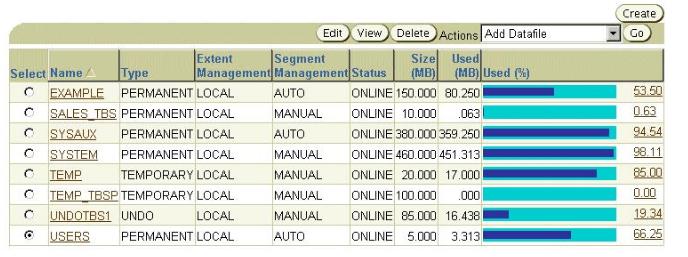
One of the important tables in the USERS tablespace was dropped and purged from the recycle bin at 9:00 a.m. You noticed this at 11:00 a.m. and you want to perform an incomplete recovery to recover the table.
Which statement is true?()
You are upgrading to the Oracle 10g Database and will use the Automatic Shared Memory Management feature of the Oracle 10g Database. Which background process serves as the SGA memory broker that
coordinates the sizing of the memory components?()
During Company.com planning session,Company.com presents the details of the current Network design. The network design serves four separate company facilities, each on as separate subnet. As part of a disaster recovery plan, the customer is evaluating the use of HACMP. Specifically, the have reviewed IPAT via IP aliasing and are questioning the number of IP subnets required.
Given the customer’s current configuration,what is the recommended minimum number of IP subnets that would be required?()
View the Exhibit and examine the privileges granted to the SL_REP user.
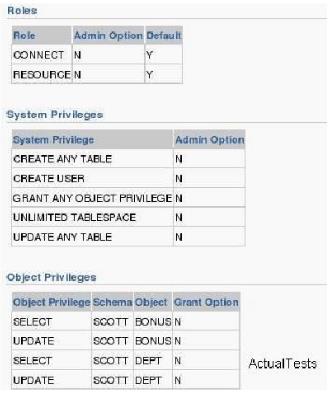
The EMP table is owned by the SCOTT user. The SL_REP user executes the following command: SQL> GRANT SELECT ON scott.emp TO hr;
Which statement describes the outcome of the command()
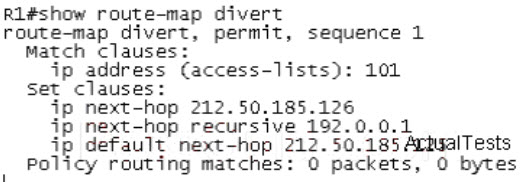
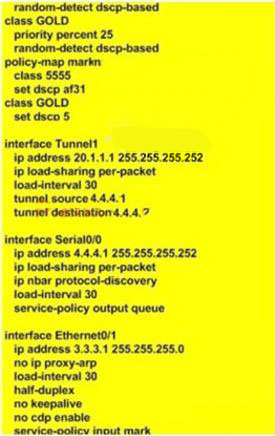
Refer to the exhibit. Based upon the configuration, you need to understand why the policy routingmatch counts are not increasing. Which would be the first logical step to take?Select the bestresponse.()
One of the key decision making factors in a very competitive opportunity will be cost. Companycom needs an aggregate rPerf rating of 120.
What is the best solution?()
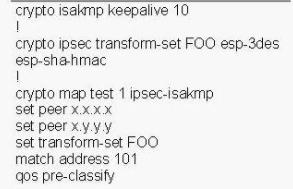
You work as a network technician at Company.com, study the exhibit provided. You are implementing this QoS configuration to improve the bandwidth guarantees for traffic towards two servers, one with the IP address 5.5.5.5 and the other with the IP address 5.5.5.4. Even after the configuration is applied, performance does not seem to improve. Which will be the most likely cause of this problem?()
Company.com has a three-node cluster with six resource groups. There are two resource groups for each node. A new hardware component will be added to one of the nodes. The customer wants to move the resource groups to other nodes,but not necessarily in the normal fallover order. Also,the resource groups must be moved at night when there is no one in the computer center. What can be done so that the resource group is moved at the most convenient normal fallover order. Also,the resource groups must be moved at night when there is no one in the computer center.
What can be done so that the resource group is moved at the most convenient time for the customer?()
Exhibit:
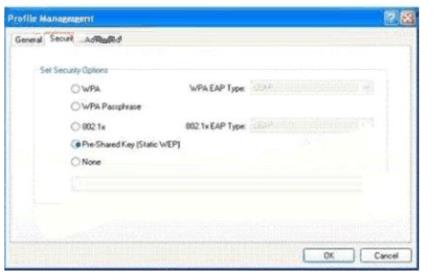
You work as a network administrator at. You study the exhibit carefully. In the wireless LAN all devices are configured with static WEP keys.
What will happen if the access point receives packets sent by the wireless client adapter that are not encrypted with the appropriate key?()
免费的网站请分享给朋友吧