Refer to the exhibit. What variation of the 802.1x Extensible Authentication Protocol (EAP) uses this authentication process?()
Exhibit:
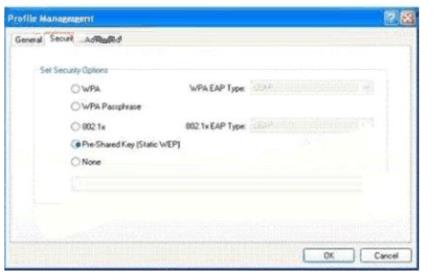
You work as a network administrator at. You study the exhibit carefully. In the wireless LAN all devices are configured with static WEP keys.
What will happen if the access point receives packets sent by the wireless client adapter that are not encrypted with the appropriate key?()
Exhibit:
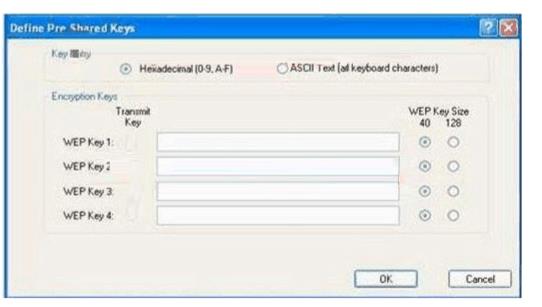
You work as a network technician at. Study the exhibit carefully. You are required configure the static WEP keys on the wireless client adapter using the Cisco ADU (Aironet Desktop Utility).
What should you have in mind when doing this?()
Exhibit, error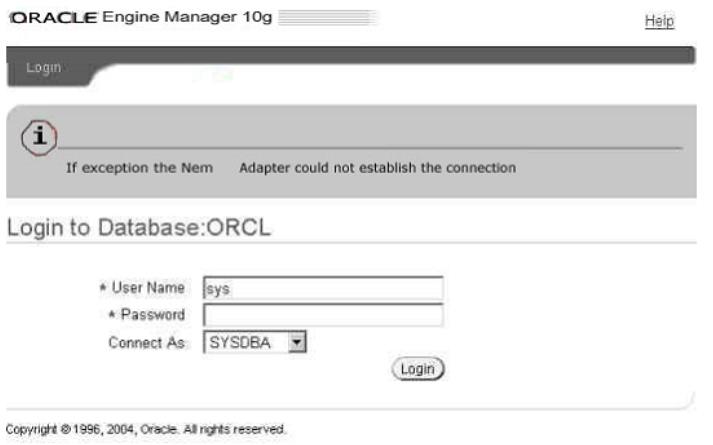
You work as a database administrator for Supportcenter.cn. When you try to connect to the database, you get an error (See exhibit). What could be the possible reason for getting such an error?()
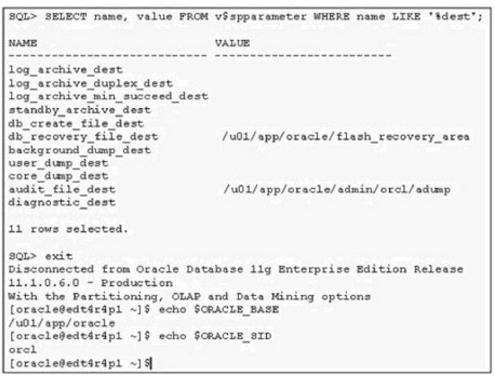
You want to check the details of few errors that users have reported. You search for the alert log fileand execute few commands to find the location of the alert log file. View the Exhibit and check the commands executed.

What is the location of the alert_orcl.log file()
You want to check the details of few errors that users have reported. You search for the alert log file andexecute few commands to find the location of the alert log file. View the Exhibit and check the commandsexecuted.
What is the location of the alert_orcl.log file()
You are a network administrator for Litware, Inc. The company’s main office is located in Lima, and branch offices are located in five other cities. The network consists of a single DNS domain named litwareinc.com. The network configuration is shown in the exhibit. (Click the Exhibit button.)
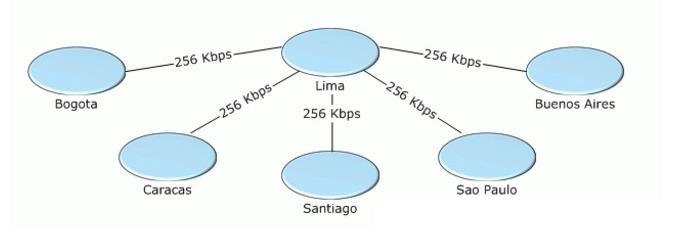
All network servers run Windows Server 2003. All client computer IP addresses are assigned by using a DHCP server that is located in each office. Client computers are reimaged often and are assigned new names each time they are reimaged. All client computers are configured to reference their local DNS server as the preferred DNS server and to reference the central DNS server as the alternate DNS server.A primary zone for litwareinc.com is configured on a server in the Lima office. Secondary zones are configured on a server in each branch office. The retry interval, the refresh interval, the expiration interval, and the default minimum Time to Live (TTL) interval are configured with the default settings.Network bandwidth utilization averages 40 percent. The network connection between the Lima office and the Bogota office fails an average of twice per day.Users in the Bogota office occasionally receive incorrect responses to queries against the local DNS server when the network connection is interrupted during a zone transfer.
You need to change the configuration of the start of authority (SOA) resource record for litwareinc.com. In addition, you need to reduce the possibility that users can query local DNS zones before successful zone transfers occur.
What should you do?()
You are the administrator of a Windows XP Professional computer named Pro1. The computer is connected to the Internet. Pro1 provides Internet access to eight other Windows XP Professional computers that are connected to Pro1. You enable Internet Connection Sharing (ICS) and Windows Firewall on Pro1. You run an application named App1 on Pro1. App1 communicates with an online training company on the Internet. To display an online seminar, the training company needs to contact the App1 application at port 5800. You want to ensure that the training company can connect to the App1 application.
What should you do?()
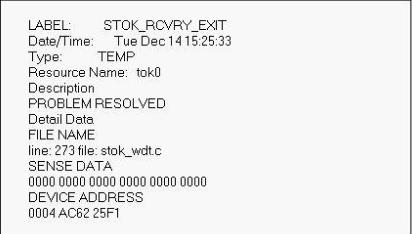
To examine the Exhibit, press the Exhibit button. Which option would produce this output from the errpt command? ()
You are employed as the Exchange administrator at Company.com.You are in the process of
installing a new Exchange Server 2010 Organization.After the installation you send a text message to an external client and receive the subsequent non-delivery report (NDR): "Delivery has failed to these recipients or groups: [email protected] ([email protected]).The recipient’s e-mail system isn’t accepting messages now.Please try resending this message later or contact the recipient directly." You attempt to e-mail the user from an external e-mail system with great success.To ensure productivity you need to make sure e-mails can be sent to external clients from within the organization.
What should you do?()
You are the network administrator for Wingtip Toys. The network consists of a single Active Directory domain named wingtiptoys.com. The Active Directory-integrated DNS zone named wingtiptoys.com is replicated to all domain controllers. Only domain controllers have the DNS service installed.The network management department requires all hosts in the manufacturing division to be registered in the DNS namespace manufacturing.wingtiptoys.com. The manufacturing.wingtiptoys.com namespace does not exist on any of the DNS servers.You need to add support for the manufacturing.wingtiptoys.com namespace to all the existing DNS servers. To reduce administrative overhead, you want to find a solution that will not require reconfiguration if DNS servers are added to the domain in the future.
What should you do?()
Refer to the exhibit. Given the configuration on a Teleworker router, and knowing it was in the process of being booted, what statement would best describe the order in which the head-end peers would be selected?()

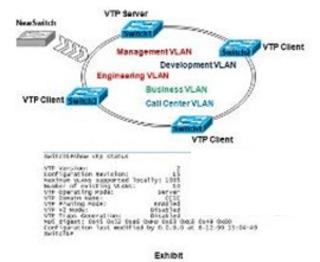
Refer to the exhibit. Users from the Engineering VLAN complain that every time Business VLAN users have a network connectivity issue,the Engineering VLAN users usually have problems experiencing slow response or network connectivity problems. After troubleshooting, anunauthorized switch 2 was found.This unauthorized switch has been a regular problem, assuming the root bridge function under thespanning-tree domain and causing the Engineering VLAN to be unstable. Which three of these actionscould be suggested to fix the problem?()
Refer to the exhibit. Users from the Engineering VLAN complain that every time Business VLAN users have a network connectivity issue, the Engineering VLAN users usually have problems experiencing slow response or network connectivity problems. After troubleshooting, an unauthorized switch 2 was found. This unauthorized switch has been a regular problem, assuming the root bridge function under the spanning-tree domain and causing the Engineering VLAN to be unstable. Which three of these actions could be suggested to fix the problem?()
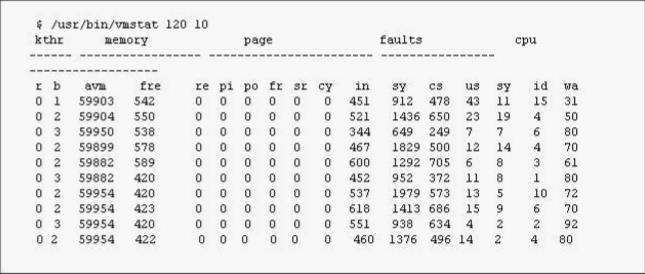
To examine the Exhibit, press the Exhibit button. While a user is compiling a C program, "vmstat 120 10" is run to determine the cause of a performance problem. Given the vmstat output as shown in the exhibit, which of the following conclusions is most appropriate to draw about the machine?()
You design a Business Intelligence (BI) solution by using SQL Server 2008.
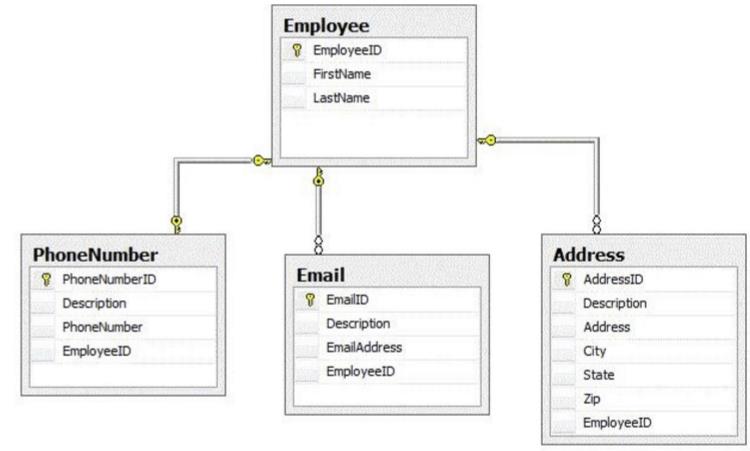
You need to load data into your online transaction processing (OLTP) database once a week by using data from a flat file. The file contains all the details about new employees who joined your company last week. The data must be loaded into the tables shown in the exhibit. (Click the Exhibit button.) Employee.EmployeeID is an identity. The safer ,easier way to help you pass any IT exams.
A SQL Server 2008 Integration Services (SSIS) package contains one data flow for each of the destination tables. In the Employee Data Flow, an OLE DB Command transformation executes a stored procedure that loads the Employee record and returns the EmployeeID value.
You need to accomplish the following tasks:
Ensure that the EmployeeID is used as a foreign key (FK) in all child tables for the correct Employee record.
Minimize the number of round trips to the database.
Ensure that the package performs in the most efficient manner possible. What should you do? ()
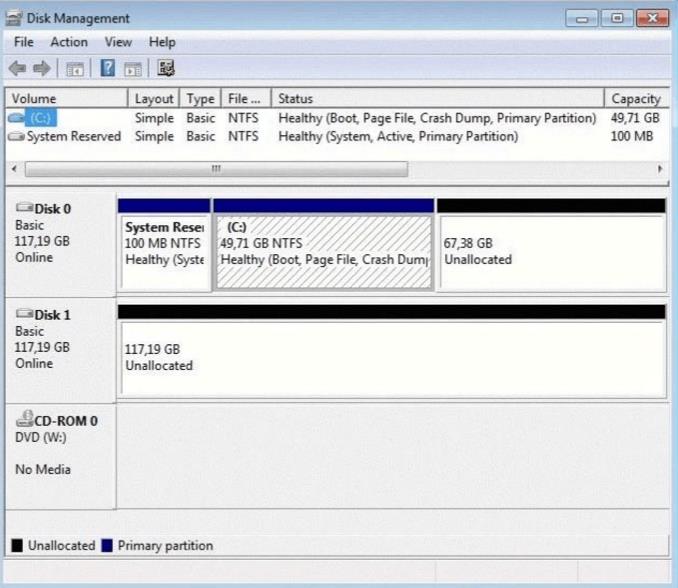
You have a computer that runs Windows 7. Your computer s disk configuration is shown in the exhibit.(Click the Exhibit button.) You need to ensure that you can create a striped volume on the computer.
What should you do?()
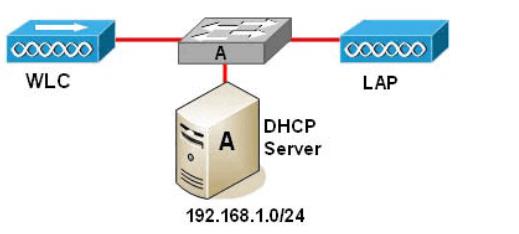
You work as a network technician at Company. Please study the exhibit carefully. In this
Company wireless network, the LAP (lightweight access point) attempts to register to a WLC (Wireless LAN Controller).
What kind of message is transmitted?()
Refer to the exhibit. What two statements are true?()
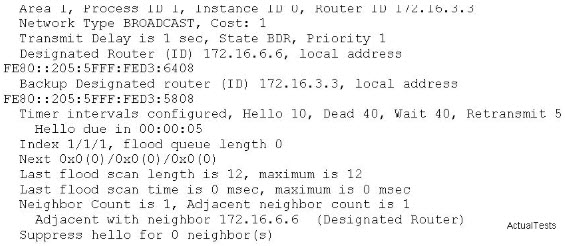
Refer to the exhibit. You would like to guarantee 7 Mb/s for FTP traffic in your LAN, as it seems that peer-to-peer traffic is taking up a large amount of bandwidth. When testing the configuration, you notice that FTP traffic doesn't reach 7 Mb/s. What is the problem?()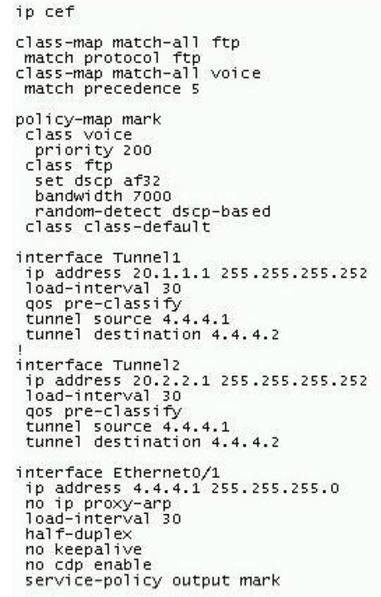
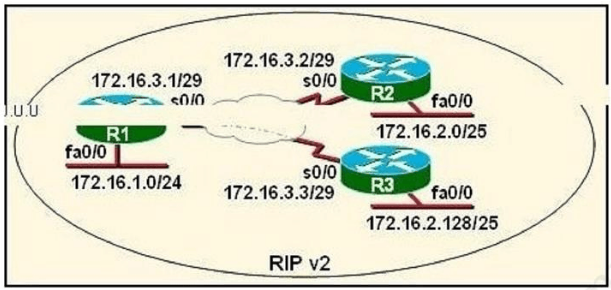
S0/0 on R1 is configured as a multipoint interface to communicate with R2 and R3 in the hub-and-spoke Frame Relay topology shown in the exhibit. Originally, static routes were configured between these routers to successfully route traffic between the attached networks. What will need to be done in order to use RIPv2 in place of the static routes?()
You are the administrator of Red Lington Enterprises. You want to upgrade 125 computers from Windows NT Workstation 4.0 to Windows 2000 Professional. You create an unattend.txt file by using the setup manager.
You copy the file to a floppy disk. You then start the installation on a computer in the test lab using the Windows 2000 Professional CD-ROM. After the computer starts you insert the floppy disk. Even though you set the user interaction level to full-unattended mode you are prompted for all the configuration parameters. You want to ensure that the unattended installation does not prompt you for input.
What should you do? ()
After using the alt_disk_install command to clone a system image to another disk, the system administrator noticed a large number of defined devices not allocated to the LPAR.
Which of the following is the most likely cause of this situation?()
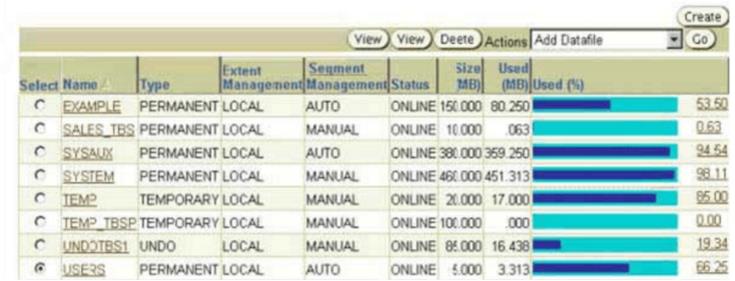
Exhibit, One of the important tables in the USERStablespace was dropped and purged from the recycle bin at 9:00 a.m. You noticed this at 11:00 a.m. and you want to perform an incomplete recovery to recover the table. Which statement is true?()
Companycom recently ordered a p5 570 and an HMC. Prior to delivery, two additional p5 570 servers were added to the order. Upon installation, the system administrator noticed that they do not have a method to connect the p5 570 servers to the HMC.
Which of the following will allow them to connect all servers to the HMC?()
View the Exhibit.
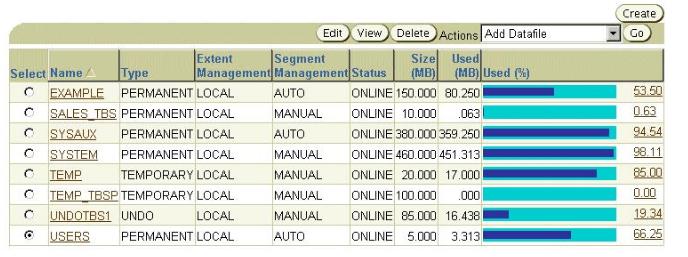
One of the important tables in the USERS tablespace was dropped and purged from the recycle bin at 9:00 a.m. You noticed this at 11:00 a.m. and you want to perform an incomplete recovery to recover the table.
Which statement is true?()
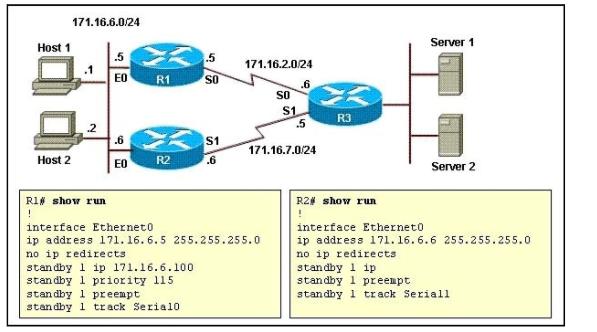
.Refer to the exhibit and the partial configuration on routers R1 and R2. Hot Standby Routing Protocol (HSRP) is configured on the network to provide network redundancy for the IP traffic. The network administrator noticed that R2 does not become active when the R1 serial0 interface goes down.
What should be changed in the configuration to fix the problem? ()
You want to enable the user, Scott, to change to the GRP1 consumer group by issuing the following code:
SQL> EXEC DBMS_SESSION.SWITCH_CURRENT_CONSUMER_GROUP
(’SCOTT’, ’GRP1’, FALSE);
How will you grant the switch privilege to the user, Scott?()
View the Exhibit and examine the privileges granted to the SL_REP user.
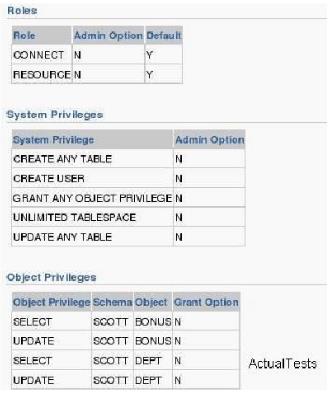
The EMP table is owned by the SCOTT user. The SL_REP user executes the following command: SQL> GRANT SELECT ON scott.emp TO hr;
Which statement describes the outcome of the command()
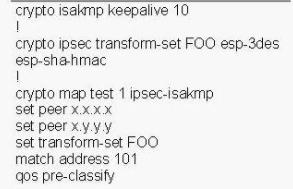
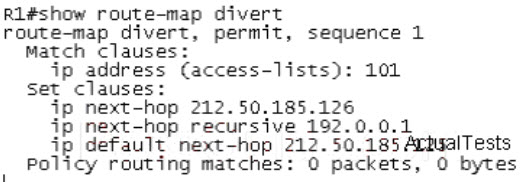
Refer to the exhibit. Based upon the configuration, you need to understand why the policy routingmatch counts are not increasing. Which would be the first logical step to take?Select the bestresponse.()
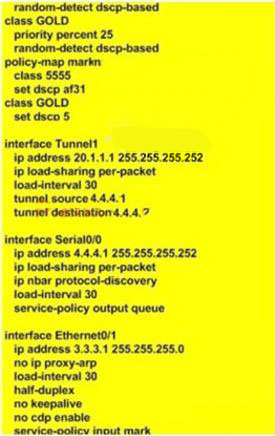
You work as a network technician at Company.com, study the exhibit provided. You are implementing this QoS configuration to improve the bandwidth guarantees for traffic towards two servers, one with the IP address 5.5.5.5 and the other with the IP address 5.5.5.4. Even after the configuration is applied, performance does not seem to improve. Which will be the most likely cause of this problem?()
You are working as a Database Administrator. Despite having a password in the data dictionary as change_on_install, you always log on to the database MYNEWDB using operating system authentication. Your organization is planning to recruit two junior-level DBAs. You decide to enable remote authentication in your database so that the new DBAs can log on to the database from their workstations to carry out administrative tasks.
To allow the new DBAs to perform the administrative tasks, you create a password file on the database server using the following command:
ORAPWD file=d:\oracle\ora9i\orapwU01 password=admin entries=4
After creating the password file, you remove the operating system authentication and change the value of the REMOTE_LOGIN_PASSWORDFILE parameter to EXCLUSIVE. You also create a net service name as MYNEWDB that allows the new DBAs to connect to the database server from their workstations using this net service name. Which command must you use to connect to the database to start it?()
免费的网站请分享给朋友吧