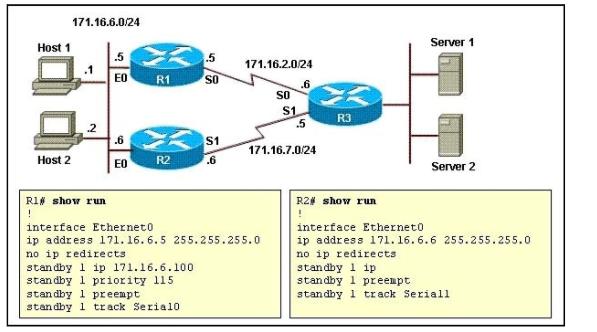
.Refer to the exhibit and the partial configuration on routers R1 and R2. Hot Standby Routing Protocol (HSRP) is configured on the network to provide network redundancy for the IP traffic. The network administrator noticed that R2 does not become active when the R1 serial0 interface goes down.
What should be changed in the configuration to fix the problem? ()
You need to recommend a solution for controlling access to the Internet.The solution must meet the museum’s security polic.
What should you include in the recommendation?()
Tiered disk systems (DS8700 and DS5020), tape backup and Cisco director(s) utilizing VSANs have been proposed as a solution. The storage specialist is asked to explain the technical
advantage of using Cisco directors and VSANs.
Which of the following is the key point to stress to the customer()
You plan to deploy a Virtual Desktop Infrastructure (VDI) for the public relations users.
You need to identify which additional software must be deployed on the network to support the planned VDI deployment.
Which additional software should you identify?()
根据写作要求,写出一篇作文。
You are Susan. Your company will hold an opening ceremony for a new factory. You are asked to write an invitation letter to David, an important client of your company. The following information should he included:the reasons to invite him; the time for the event;the place for the event;early reply expected.
You are designing a top-level OU structure to meet the business and technical requirements.
Which top-evel OU or OUs should you use? ()
A customer has installed an IBM System Storage DS8700 with 20 TB of storage, two-way processor version, 32 GB cache, and 16 Fibre Channel ports. The customer is beginning to experience throughput performance issues.
To address this performance consideration with minimal cost to the customer, which of the following should be the FIRST step to resolve the problem()
A current Sun Solaris customer has just purchased their first p5 590. During the Solution Assurance, the backup requirements were discussed.
Which of the following should be recommended to the customer with regards to restoring rootvg?()
You are employed as the Exchange administrator at Company.com.You are in the process of
installing a new Exchange Server 2010 Organization.After the installation you send a text message to an external client and receive the subsequent non-delivery report (NDR): "Delivery has failed to these recipients or groups: [email protected] ([email protected]).The recipient’s e-mail system isn’t accepting messages now.Please try resending this message later or contact the recipient directly." You attempt to e-mail the user from an external e-mail system with great success.To ensure productivity you need to make sure e-mails can be sent to external clients from within the organization.
What should you do?()
You are the network administrator for Wingtip Toys. The network consists of a single Active Directory domain named wingtiptoys.com. The Active Directory-integrated DNS zone named wingtiptoys.com is replicated to all domain controllers. Only domain controllers have the DNS service installed.The network management department requires all hosts in the manufacturing division to be registered in the DNS namespace manufacturing.wingtiptoys.com. The manufacturing.wingtiptoys.com namespace does not exist on any of the DNS servers.You need to add support for the manufacturing.wingtiptoys.com namespace to all the existing DNS servers. To reduce administrative overhead, you want to find a solution that will not require reconfiguration if DNS servers are added to the domain in the future.
What should you do?()
A customer would like to have the ability to permanently activate processor and memory resources as their workload increases.
Which of the following supports the customer requirement?()
Refer to the exhibit. Given the configuration on a Teleworker router, and knowing it was in the process of being booted, what statement would best describe the order in which the head-end peers would be selected?()
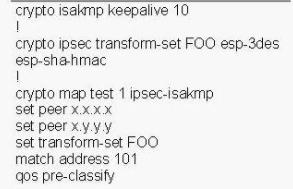

Refer to the exhibit. Users from the Engineering VLAN complain that every time Business VLAN users have a network connectivity issue,the Engineering VLAN users usually have problems experiencing slow response or network connectivity problems. After troubleshooting, anunauthorized switch 2 was found.This unauthorized switch has been a regular problem, assuming the root bridge function under thespanning-tree domain and causing the Engineering VLAN to be unstable. Which three of these actionscould be suggested to fix the problem?()
Refer to the exhibit. Users from the Engineering VLAN complain that every time Business VLAN users have a network connectivity issue, the Engineering VLAN users usually have problems experiencing slow response or network connectivity problems. After troubleshooting, an unauthorized switch 2 was found. This unauthorized switch has been a regular problem, assuming the root bridge function under the spanning-tree domain and causing the Engineering VLAN to be unstable. Which three of these actions could be suggested to fix the problem?()
A user is unable to determine the default system text editor.
How can the local administrator assist the user by identifying the default text editor for the system?()
You need to recommend a backup strategy for the servers in the San Francisco office. The strategy must meet the company's technical requirements
What should you include in the recommendation?()
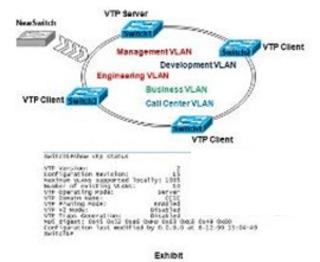
Refer to the exhibit. What two statements are true?()
At the request of a user, you issue the following command to restore a dropped table: flashback table "BIN$F2JFfMq8Q5unbC0ceE9eJg==$0" to before drop; Later, the user notifies you that the data in the table seems to be very old and out of date.
What might be the problem?()
Refer to the exhibit. You would like to guarantee 7 Mb/s for FTP traffic in your LAN, as it seems that peer-to-peer traffic is taking up a large amount of bandwidth. When testing the configuration, you notice that FTP traffic doesn't reach 7 Mb/s. What is the problem?()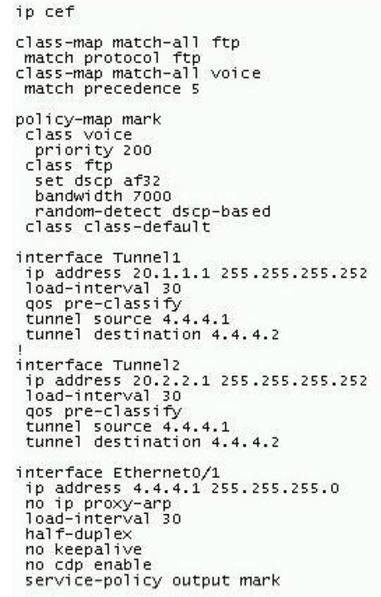
A co-worker is unable to invite you to a Microsoft Windows Meeting Space meeting. You need to receive an invite to the meeting.
What should you do?()
You are the network administrator for Company. to do an unattended installation so you create an Answer.txt file by using Setup Manager. The Answer.txt is copied to a floppy disk and you start the installation on a test computer by booting the computer with the Windows 2000 Professional CD-ROM. You insert the floppy disk after the computer starts. Although you had set the user interaction level to full unattended mode, you are prompted for all the required parameters. You want to ensure that the unattended installation upgrades the Windows 98 computers.
What should you do?()
In Recovery Manager (RMAN), you set the retention policy to NONE by executing the following command:
CONFIGURE RETENTION POLICY TO NONE;
What would be the impact of this setting?()
A customer wants to purchase an IBM System Storage DS8700 to support a high-performance database environment.
Which technical solution gives the customer the best relationship between I/O performance at the machine’s backend vs. capacity installed in the machine()
While installing the equipment for a new two-node cluster, it is discovered that the disk subsystem Rack has one connection to the power mains. The explanation given was that the disks are to be mirrored between the two disk drawers in the rack and that a failure in either of the disk drawers would simply result in half of the disk being lost.
What can be done to avoid a single point of failure?()
After using the alt_disk_install command to clone a system image to another disk, the system administrator noticed a large number of defined devices not allocated to the LPAR.
Which of the following is the most likely cause of this situation?()
Companycom recently ordered a p5 570 and an HMC. Prior to delivery, two additional p5 570 servers were added to the order. Upon installation, the system administrator noticed that they do not have a method to connect the p5 570 servers to the HMC.
Which of the following will allow them to connect all servers to the HMC?()
.Refer to the exhibit and the partial configuration on routers R1 and R2. Hot Standby Routing Protocol (HSRP) is configured on the network to provide network redundancy for the IP traffic. The network administrator noticed that R2 does not become active when the R1 serial0 interface goes down.
What should be changed in the configuration to fix the problem? ()

You want to enable the user, Scott, to change to the GRP1 consumer group by issuing the following code:
SQL> EXEC DBMS_SESSION.SWITCH_CURRENT_CONSUMER_GROUP
(’SCOTT’, ’GRP1’, FALSE);
How will you grant the switch privilege to the user, Scott?()
A banking user with the userid of ’joe’ is unable to rsh from SYSTEMA to SYSTEMB without having to retype their password, but they can rsh from SYSTEMB to SYSTEMA. No other users are experiencing the same issue.
Both systems have a /home/joe/.rhosts file that contain the proper references to the other host. The /home/joe/.rhosts files on both SYSTEMA and SYSTEMB are owned by userid ’joe’.
Which of the following is the most likely cause of this problem()
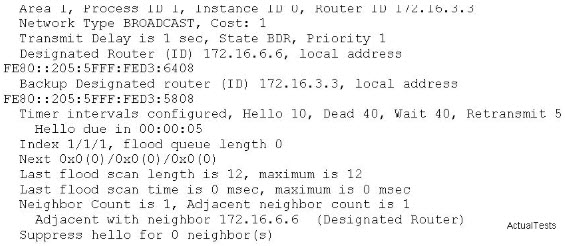
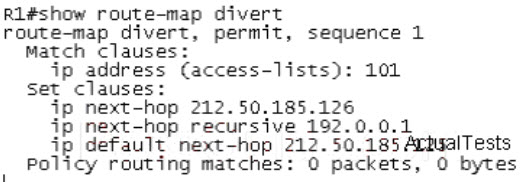
Refer to the exhibit. Based upon the configuration, you need to understand why the policy routingmatch counts are not increasing. Which would be the first logical step to take?Select the bestresponse.()
You need to configure a new Company switch to support DTP.
Which DTP switchport mode parameter sets the switch port to actively send and respond to DTP negotiation frames? ()
You are working as a Database Administrator. Despite having a password in the data dictionary as change_on_install, you always log on to the database MYNEWDB using operating system authentication. Your organization is planning to recruit two junior-level DBAs. You decide to enable remote authentication in your database so that the new DBAs can log on to the database from their workstations to carry out administrative tasks.
To allow the new DBAs to perform the administrative tasks, you create a password file on the database server using the following command:
ORAPWD file=d:\oracle\ora9i\orapwU01 password=admin entries=4
After creating the password file, you remove the operating system authentication and change the value of the REMOTE_LOGIN_PASSWORDFILE parameter to EXCLUSIVE. You also create a net service name as MYNEWDB that allows the new DBAs to connect to the database server from their workstations using this net service name. Which command must you use to connect to the database to start it?()
免费的网站请分享给朋友吧