In your production database, data manipulation language (DML) operations are executed on the SALES table.You have noticed some dubious values in the SALES table during the last few days. You are able to track
users, actions taken, and the time of the action for this particular period but the changes in data are not tracked.You decide to keep track of both the old data and new data in the table along with the user information.
Whataction would you take to achieve this task()
Your network includes the servers shown in the following table:

Per-device Remote Desktop Services client access licenses (RDS CALs) are installed on Server1. After you refresh a group of client computers with Windows 7, users on those computers can no longer connect to Server2. You need to ensure that the users can connect to remote applications.
What should you do?()
You work as a Web Developer at Certkiller.com. You are in the process of creating a Webapplication using Microsoft ASP.NET 3.5.
You host the Web application in Microsoft Internet Information Services (IIS) 6.0. You browse theapplication and receive the following error message:
Server Application Unavailable
The web application you are attempting to access on this web server is currently unavailable.Please hit the "Refresh" button in your web browser to retry your request.
You view the Application event log and discover the following message:
It is not possible to run two different versions of ASP.NET in the same IIS process. Please use theIIS Administration Tool to reconfigure your server to run the application in a separate process.
To ensure productivity you need to solve this problem as quick as possible.
What should you do?()
A customer is interested in reducing energy consumption and infrastructure consolidation for space. The customer needs a maximum of 14 servers in 7U rack.
Which IBM BladeCenter Chassis should be recommended? ()
You want to back up your 100-GB database on a remote tape device. You are required to ensure that minimum network bandwidth is consumed while transferring the backups to the tape device.
The current consumption of your CPU is approximately 40 percent.
Which type of backup should you perform?()
You are designing a top-level OU structure to meet the business and technical requirements.
Which top-evel OU or OUs should you use? ()
You have a computer that runs Windows 7. The computer is in a workgroup. You need to ensure that youcan decrypt Encrypting File System (EFS) files on the computer if you forget your password.
What are two possible ways to achieve this goal?()
Given the following RMAN commands,choose the option that reflects the order required to restore your currently operational ARCHIVELOG-mode database.()
a. restore database
b. recover database
c. shutdown immediate
d. startup
e. restore archivelog all
f. alter database open
You are a professional level SQL Server 2005 database administrator in an international corporation named Wiikigo. You are experienced in implementing high-availability solutions, monitoring the database server, and design deployment. In the company, you major job is the deployment, maintenance and support of Microsoft SQL Server 2005. You work as a database administrator for your company. There is a database named Inventory on a SQL Server 2005 computer, and the computer is named SQL01. SQL01 is utilized to aggregate manufacturing part numbers from your company’s trading partners. And the company stores the manufacturing part numbers in the Product table in the Inventory database. The company requests the users to deliver data as text files from each trading partner to SQL1 every night. The data should be imported, and no duplicate manufacturing part numbers should exist in the data which is imported from the text files, and the text files are stored in the Inventory database on SQL01. You should cut the effect on your company’s trading partners and your IT department to the least.
Which action should you perform?()
You are using an Automatic Storage Management (ASM) instance to manage the files of your production database. While studying the parameter file of the ASM instance, you find the following entry:
ASM_DISKSTRING = /devices/*
What could be the reason for this setting?()
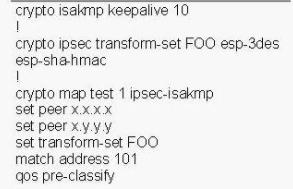
Refer to the exhibit. Given the configuration on a Teleworker router, and knowing it was in the process of being booted, what statement would best describe the order in which the head-end peers would be selected?()
Your portable computer is in sleep mode. When you resume work on the portable computer, you are not prompted for a password.
You need to ensure that you are prompted for a password each time the portable computer recovers from sleep mode.
What should you do?()
You are designing a strategy for migrating to the new environment.
Which two factions from your current environment will affect your migration strategy?()

All client computers in your network run Windows 7 Enterprise.
You need to prevent all standard user accounts from running programs that are signed by a specific publisher.
What should you do?()
Your network consists of a single Active Directory forest that contains two domains named contoso.com and litwareinc.com. All domain controllers for contoso.com are in an office located in Singapore. All domain controllers for litwareinc.com are in an office located in Los Angeles.
There is a single 128-Kbps WAN link between the two offices.All domain controllers run Windows Server 2003 Service Pack 2 (SP2) and are configured as DNS servers. Each domain controller contains a standard DNS zone for its respective domain.You need to ensure that users in the Singapore office can resolve IP addresses for servers in the Los Angeles office. The solution must minimize replication traffic over the WAN link.
What should you do?()
You need to recommend a backup strategy for the servers in the San Francisco office. The strategy must meet the company's technical requirements
What should you include in the recommendation?()
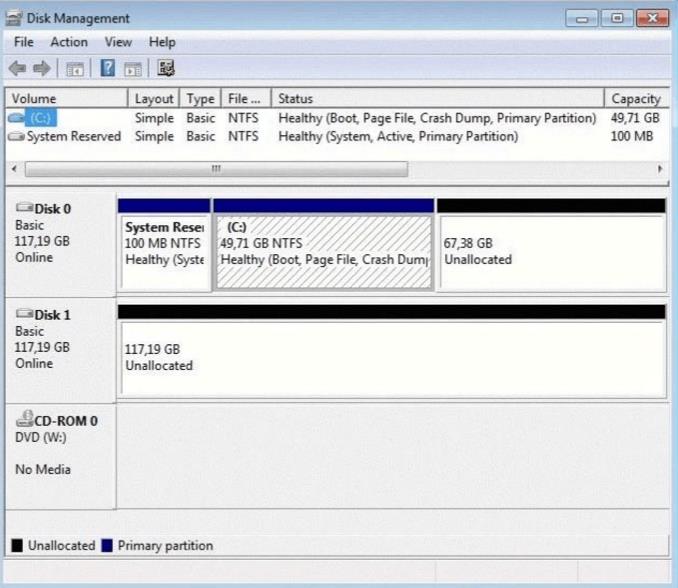
You have a computer that runs Windows 7. Your computer s disk configuration is shown in the exhibit.(Click the Exhibit button.) You need to ensure that you can create a striped volume on the computer.
What should you do?()
You work in a company which is named Wiikigo Corp. The company uses SQL Server 2008. You are the administrator of the company database. Now you are in charge of a SQL Server 2008 instance. There is a database named DB1 in the instance. In the database, a small percentage of data is modified everyday. Ever day in the morning, you have to create a read-only copy of the database for reporting purposes and make sure that you use as little disk space as possible.
In the options below, which strategy should you use?()
Your network consists of a single Active Directory forest. The sales department in your company has 600 Windows Server 2008 R2 servers. You need to recommend a solution to monitor the performance of the 600 servers.
Your solution must meet the following requirements:
èGenerate alerts when the average processor usage is higher than 90 percent for 20 minutes.
èAutomatically adjust the processor monitoring threshold to allow for temporary changes in the workload.
What should you recommend?()
You need to design a Windows Server Update Services (WSUS) infrastructure that meets the following requirements:
èThe updates must be distributed from a central location.
èAll computers must continue to receive updates in the event that a server fails.
What should you include in your design?()
Youre performing tablespace point-in-time recovery on a tablespace called USERS. If an object in that tablespace has a foreign key constraint owned by another object in the INDEX_TBS
which statement is true?()
You are building a dating web site. The client’s date of birth is collected along with lots of other information.You have created an EL function with the signature:
calcAge(java.util.Date):int and it is assigned to the name, age, in the namespace, funct. In one of your JSPsyou need to print a special message to clients who are younger than 25.
Which EL code snippet will returntrue for this condition?()
In your database instance, the STATISTICS_LEVEL initialization parameter is set to BASIC.
What isthe impact of this setting()
Your computer has Microsoft Windows Firewall enabled.
Your child plays an online game that uses connectionless traffic over port 5678 for inbound and outbound traffic.
You need to prevent your child from playing this game.
What should you do? ()
In your production database, data manipulation language (DML) operations are executed on theSALES table. You have noticed some dubious values in the SALES table during the last few days. Youare able to track users, actions taken, and the time of the action for this particular period but the changesin data are not tracked. You decide to keep track of both the old data and new data in the table along withthe user information.
What action would you take to achieve this task()
In your production database, data manipulation language (DML) operations are executed on the SALES table.You have noticed some dubious values in the SALES table during the last few days. You are able to track
users, actions taken, and the time of the action for this particular period but the changes in data are not tracked.You decide to keep track of both the old data and new data in the table along with the user information.
Whataction would you take to achieve this task()
Your company has a single Active Directory directory service domain. All servers in your environment run Windows Server 2003. You have a stand-alone server that serves as a Stand-alone root certification authority (CA). You need to ensure that a specific user can back up the CA and configure the audit parameters on the CA.
What should you do?()
Your database is running in ARCHIVELOG mode. The SCOTT.EMP table belongs to the DATA1 tablespace. The junior DBA erroneously runs a script that executes the following statement:
SQL> DROP TABLE SCOTT.EMP PURGE;
After one hour, you are performing the user managed incomplete recovery. Which datafiles will you restore from the last full backup?()
Your boss, Miss ,is interested in CEF.
What should you tell her? ()
You work as a network technician at. Your boss, Mrs. , is interested in the Spanning Tree Protocol timers.
What can you tell her regarding the default STP timers? ()
You work as a network technician at Company. Your boss, Mrs., is interested in LWAPP (Lightweight Access Point Protocol).
What should you tell her regarding this technology? ()
You work as a network technician at Company. Your boss, Mrs., is interested in the Cisco Compatible Extensions program.
What are three features of this program? ()
Your network contains an Active Directory domain. All servers run Windows Server 2008 R2.
You need to audit the deletion of registry keys on each server.
What should you do()
免费的网站请分享给朋友吧