Which of the following commands should be used to open a tty port configured in the /etc/uucp/Devices file as:
Direct tty2 - 9600 direct
in debug mode, ignoring modem control signal data carrier detect (DCD)?()
A customer currently buys HP ProLiant servers and EMC storage. The customer has encountered various problems getting certain servers to work with their storage.
Which of the following arguments can the Sales Specialist present to best position IBM? ()
Companycom has seven days of vmstat data on four p5 590 production LPARs of four processors each. The data shows that all four LPARs have periodic utilizations of 90-95% lasting several minutes in duration. However, the average utilizations of the four LPARs were between 15-30%. The vmstat data shows that the peak utilizations of each LPAR do not occur at the same time.
Which of the following should be set up?()
A customer is interested in reducing energy consumption and infrastructure consolidation for space. The customer needs a maximum of 14 servers in 7U rack.
Which IBM BladeCenter Chassis should be recommended? ()
You want to back up your 100-GB database on a remote tape device. You are required to ensure that minimum network bandwidth is consumed while transferring the backups to the tape device.
The current consumption of your CPU is approximately 40 percent.
Which type of backup should you perform?()
You are designing a top-level OU structure to meet the business and technical requirements.
Which top-evel OU or OUs should you use? ()
A customer has purchased three IBM System Storage DS8700 systems and would like to have their administrators trained.
Which training alternative provides the necessary training with the least financial impact()
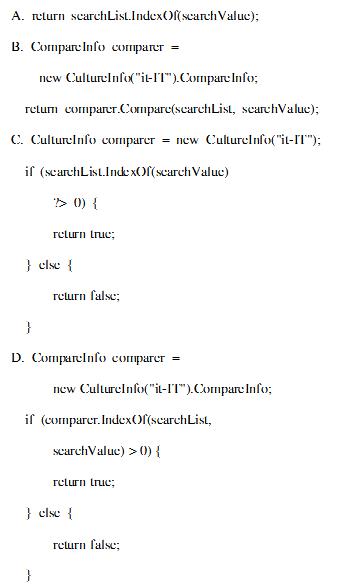
You are developing a method that searches a string for a substring. The method will be localized to Italy. Your method accepts the following parameters:
The string to be searched, which is named searchList
The string for which to search, which is named searchValue You need to write the code.
Which code segment should you use?()
An administrator is beginning a set of failover tests. The administrator would like to have clean log files foreach test.
Which command will achieve this?()
A customer has installed an IBM System Storage DS8700 with 20 TB of storage, two-way processor version, 32 GB cache, and 16 Fibre Channel ports. The customer is beginning to experience throughput performance issues.
To address this performance consideration with minimal cost to the customer, which of the following should be the FIRST step to resolve the problem()
A current Sun Solaris customer has just purchased their first p5 590. During the Solution Assurance, the backup requirements were discussed.
Which of the following should be recommended to the customer with regards to restoring rootvg?()
Which of the following statements is true regarding the initialization parameter DIAGNOSTIC_DEST?()
The default value is the value of the environment variable $ORACLE_HOME; if $ORACLE_HOME isn’t set
A customer would like to have the ability to permanently activate processor and memory resources as their workload increases.
Which of the following supports the customer requirement?()

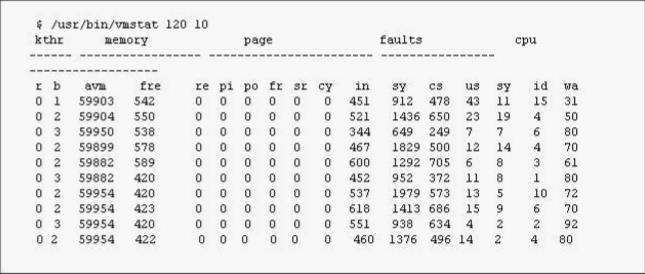
To examine the Exhibit, press the Exhibit button. While a user is compiling a C program, "vmstat 120 10" is run to determine the cause of a performance problem. Given the vmstat output as shown in the exhibit, which of the following conclusions is most appropriate to draw about the machine?()
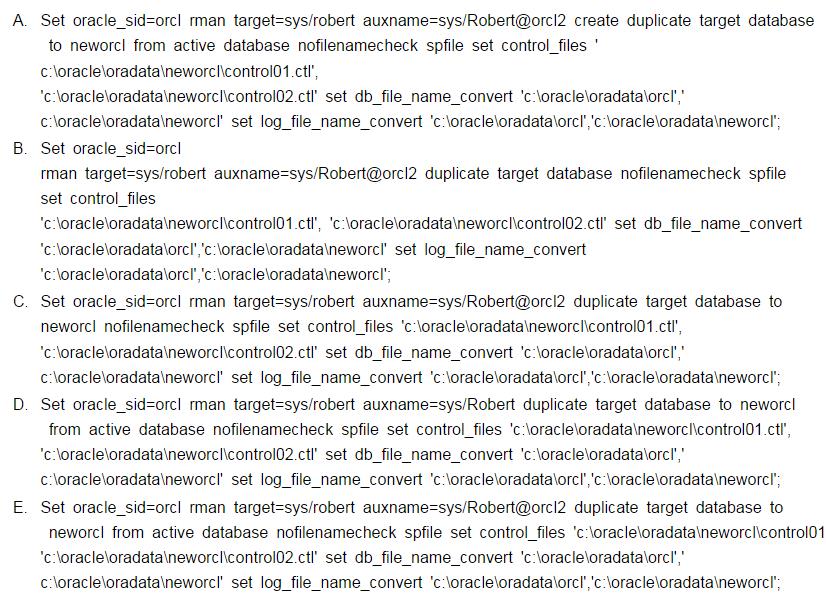
Which of the following commands will perform an active database duplication of the ORCL database to the ORCL2 database?()
You work in a company which is named Wiikigo Corp. The company uses SQL Server 2008. You are the administrator of the company database. Now you are in charge of a SQL Server 2008 instance. There is a database named DB1 in the instance. In the database, a small percentage of data is modified everyday. Ever day in the morning, you have to create a read-only copy of the database for reporting purposes and make sure that you use as little disk space as possible.
In the options below, which strategy should you use?()
You work in a company which is named Wiikigo Corp. The company uses SQL Server 2008. You are the administrator of the company database. Now you are in charge of a SQL Server 2008 instance. There is a text file which is named SQL01.log on the E: drive. A SQL Server Agent job executes every 2 minutes and logs information to the text file. You get a report from users saying that the sever doesn't make response. As the technical support, you check and find that the SQL Server Agent service does not run and the SQL Server Agent job no longer functions. You have to identify the reason why the SQL Server Agent service is unresponsive.
In the options below, which log should you check? ()
A customer would like to share the processor resources automatically between logical partitions.
Which of the following would accomplish this requirement without user interaction? ()
Evaluate the following command:
SQL>ALTER SYSTEM SET db_securefile = ’IGNORE’;
What is the impact of this setting on the usage of SecureFiles?()
A customer wants to purchase an IBM System Storage DS8700 to support a high-performance database environment.
Which technical solution gives the customer the best relationship between I/O performance at the machine’s backend vs. capacity installed in the machine()
A customer needs 40 TB for Tier 2 Information Lifecycle Management (ILM) data installed on the System z/VM. Their current data center is critically short of floor space.
Which of the following would satisfy the customer requirement()
After using the alt_disk_install command to clone a system image to another disk, the system administrator noticed a large number of defined devices not allocated to the LPAR.
Which of the following is the most likely cause of this situation?()
You are upgrading to the Oracle 10g Database and will use the Automatic Shared Memory Management feature of the Oracle 10g Database. Which background process serves as the SGA memory broker that
coordinates the sizing of the memory components?()
During Company.com planning session,Company.com presents the details of the current Network design. The network design serves four separate company facilities, each on as separate subnet. As part of a disaster recovery plan, the customer is evaluating the use of HACMP. Specifically, the have reviewed IPAT via IP aliasing and are questioning the number of IP subnets required.
Given the customer’s current configuration,what is the recommended minimum number of IP subnets that would be required?()
Which statement is true regarding the effect of this command on the transaction in Scott’s session()

You are responsible for increasing the security within the Company LAN. Of the following choices listed below,
which is true regarding layer 2 security and mitigation techniques? ()
A client has requested an IBM System x solution. Pricing is the most sensitive decision factor. They are looking for 12 TB of storage, with a projected growth of 10-15%. As this is the only server accessing this amount of data, the customer does not require a SAN.
What should the System x Sales Specialist recommend?()
Tiered disk systems (DS8700 and DS5020), tape backup and Cisco director(s) utilizing VSANs have been proposed as a solution. The storage specialist is asked to explain the technical
advantage of using Cisco directors and VSANs.
Which of the following is the key point to stress to the customer()
You need to recommend a technology to deploy and manage updates of Business_App for the public relations users.
The solution must meet the company’s corporate requirements.
Which technology should you recommend?()
A healthcare provider has two applications that they need to redundantly protect in a SAN environment. Their patient record application runs on Oracle 11i and consists of many small, randomly accessed files. The database is kept on three clustered Sun servers and currently uses 30 TB of data space. Their imaging application that retains and manages x-rays, consists of Filenet, CommonStore, and TSM running on an IBM Power750 server, and is currently using 65
TB of data space.
Which of the following disk solutions meets the customer’s requirement()
There are 30 managed access points on the wlse. a radio scan is started but fails. Upon
inspection of the device list in the reports tab, you notice a red indicator on the wds access point. upon inspection of the wds access point through its guid, it is discovered that the security keys are not set up between the wds access point and the wlse.
Which of the following is mis configured?()
There are 30 managed access points on the WLSE. A radio scan is started but fails. Upon inspection of the device list in the reports tab, you notice a red indicator on the WDS access point.Upon inspection of the WDS access point through its GUI, it is discovered that the security keys arenot set up between the WDS access point and the WLSE.
Which of the following is misconfigured?()
Sometimes performance is more important than availability (e.g., in cases where the data can be easily re-created).
Which of the following is the appropriate disk configuration for an application that requires faster writes over availability()
免费的网站请分享给朋友吧