You need to recommend a management solution for the corporate Web sites that meets the museum’s security policy
What should you include in the recommendation?()
You have an enterprise subordinate certification authority (CA) configured for key archival. Three key recovery agent certificates are issued. The CA is configured to use two recovery agents.
You need to ensure that all of the recovery agent certificates can be used to recover all new private keys.
What should you do()
You deploy a mobile messaging solution with Microsoft Exchange Server 2003 Service Pack 2.
When the application is running, it must not be able to access protected registry keys.
You need to ensure that the application meets the outlined requirement.
What are two possible ways to achieve this goal?()
You have an enterprise subordinate certification authority (CA) configured for key archival. Three key recovery agent certificates are issued.
The CA is configured to use two recovery agents.
You need to ensure that all of the recovery agent certificates can be used to recover all new private keys.
What should you do()
You create an ASP.NET server control in the SampleControl namespace. The control uses a JavaScript file names Refresh.js to implement AJAX functionality.You need to ensre that the JavaScript file is included in the assembly.
Which two actions should you perform?()
You are implementing a read-only page that includes the following controls.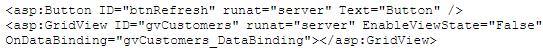
You disable view state to improve performance. You need to ensure that the page is updated to display the latest data when the user clicks the refresh button. Which code segment should you use?()
You are designing a top-level OU structure to meet the business and technical requirements.
Which top-evel OU or OUs should you use? ()
You have a computer that runs Windows 7. The computer is in a workgroup. You need to ensure that youcan decrypt Encrypting File System (EFS) files on the computer if you forget your password.
What are two possible ways to achieve this goal?()
You are developing a method that searches a string for a substring. The method will be localized to Italy. Your method accepts the following parameters:
The string to be searched, which is named searchList
The string for which to search, which is named searchValue You need to write the code.
Which code segment should you use?()
You are employed as the Exchange administrator at Company.com.You are in the process of
installing a new Exchange Server 2010 Organization.After the installation you send a text message to an external client and receive the subsequent non-delivery report (NDR): "Delivery has failed to these recipients or groups: [email protected] ([email protected]).The recipient’s e-mail system isn’t accepting messages now.Please try resending this message later or contact the recipient directly." You attempt to e-mail the user from an external e-mail system with great success.To ensure productivity you need to make sure e-mails can be sent to external clients from within the organization.
What should you do?()
You have a portable computer that runs Windows 7. You configure the computer to enter sleep mode after10 minutes of inactivity. You do not use the computer for 15 minutes and discover that the computer has notentered sleep mode. You need to identify what is preventing the computer from entering sleep mode.
What should you do?()
Your portable computer is in sleep mode. When you resume work on the portable computer, you are not prompted for a password.
You need to ensure that you are prompted for a password each time the portable computer recovers from sleep mode.
What should you do?()
You have a portable computer that runs Windows XP Professional. The computer supports Advanced Configuration and Power Interface (ACPI). You need to ensure that the computer enters Sleep Mode when you close the lid of the computer.
What should you do?()

All client computers in your network run Windows 7 Enterprise.
You need to prevent all standard user accounts from running programs that are signed by a specific publisher.
What should you do?()
You are designing a Windows 7 deployment image.
You plan to partition the hard disk of each client computer during deployment. You need to modify the unattended answer file by using a text editor.
Where should you add the disk information?()
You need to recommend a backup strategy for the servers in the San Francisco office. The strategy must meet the company's technical requirements
What should you include in the recommendation?()
You need to identify all failed logon attempts on the domain controllers.
What should you do()
A co-worker is unable to invite you to a Microsoft Windows Meeting Space meeting. You need to receive an invite to the meeting.
What should you do?()
You are designing an automated deployment process for a Windows Azure application.
The process must deploy the application to Windows Azure without any user interaction. You need to recommend a deployment strategy.
What should you recommend?()
You are planning a Windows 7 deployment infrastructure for a new company.
You have the following requirements:
Three domains
10,000 client computers No user interaction
You need to recommend a deployment infrastructure.
What should you recommend?()
Your company has a single Active Directory Domain Services (AD DS) domain and 1,000 Windows 7 computers.
You are planning to deploy a custom application.
You need to schedule the deployment to occur outside of business hours and without user interaction.
Which deployment method should you choose?()
You add an Online Responder to an Online Responder Array. You need to ensure that the new Online Responder resolves synchronization conflicts for all members of the Array.
What should you do()
You add an Online Responder to an Online Responder Array.
You need to ensure that the new Online Responder resolves synchronization conflicts for all members of the Array.
What should you do()
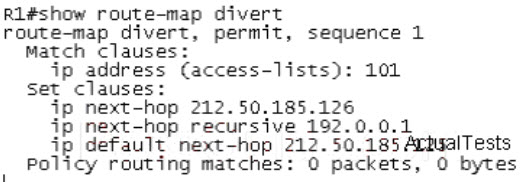
Refer to the exhibit. Based upon the configuration, you need to understand why the policy routingmatch counts are not increasing. Which would be the first logical step to take?Select the bestresponse.()
You need to configure a new Company switch to support DTP.
Which DTP switchport mode parameter sets the switch port to actively send and respond to DTP negotiation frames? ()
You have a computer that runs Windows XP Professional. You download new video card driver from the Internet, and then install the driver. You restart the computer. You discover that the newly loaded video driver is named VgaSave.
You need to restore the previous version of the video card driver.What should you do?()
You need to recommend a backup solution for the VMs that meets the museum's technical requirements.
What should you include in the recommendation?()
You need to recommend a solution for controlling access to the Internet.The solution must meet the museum’s security polic.
What should you include in the recommendation?()
You need to recommend a monitoring solution for App1 that meets the museum’s technical requirements.
What should you include in the recommendation?()
You need to recommend a management solution for the corporate Web sites that meets the museum’s security policy
What should you include in the recommendation?()
You need to recommend a technology to deploy and manage updates of Business_App for the public relations users.
The solution must meet the company’s corporate requirements.
Which technology should you recommend?()
You plan to deploy a Virtual Desktop Infrastructure (VDI) for the public relations users.
You need to identify which additional software must be deployed on the network to support the planned VDI deployment.
Which additional software should you identify?()
Your network contains an Active Directory domain. All servers run Windows Server 2008 R2.
You need to audit the deletion of registry keys on each server.
What should you do()
免费的网站请分享给朋友吧