Your network contains several Windows Server 2008 R2 servers that run Windows Server Update
Services (WSUS). The WSUS servers distribute updates to all computers on the internal network. Remote users connect from their personal computers to the internal network by using a split-tunnel VPN connection.
You need to plan a strategy for patch management that deploys updates on the remote users coputers.
Your strategy must meet the following requirements:
èMinimize bandwidth use over the VPN connections.
èRequire updates to be approved on the WSUS servers before they are installed on the client computers.
What should you include in your plan?()
Your company has several branch offices. Your network consists of a single Active Directory domain.
Each branch office contains domain controllers and member servers. The domain controllers run Windows Server 2003 SP2. The member servers run Windows Server 2008 R2. Physical security of the servers at the branch offices is a concern.
You plan to implement Windows BitLocker Drive Encryption (BitLocker) on the member servers. You need to ensure that you can access the BitLocker volume if the BitLocker keys are corruptedon the member servers. The recovery information must be stored in a central location.
What should you do?()
You are the administrator of your company's network. A user named David runs Windows 2000 Professional on his portable computer. David wants to be able to work at home on files that he created at the office and stored on the company network. Prior to logging off the network and leaving the office, David enables offline files.
David calls you from home and reports that copies of his folders and files on the network are not available on his portable computer. What should you instruct David to do, so that he can proceed with his work?()
根据写作要求,写出一篇作文。
You are Susan. Your company will hold an opening ceremony for a new factory. You are asked to write an invitation letter to David, an important client of your company. The following information should he included:the reasons to invite him; the time for the event;the place for the event;early reply expected.
Your network includes the servers shown in the following table:

Per-device Remote Desktop Services client access licenses (RDS CALs) are installed on Server1. After you refresh a group of client computers with Windows 7, users on those computers can no longer connect to Server2. You need to ensure that the users can connect to remote applications.
What should you do?()
Your Windows 2000 Professional computer is configured to support two monitors. You install a DOS-based application on your computer. The application uses the Windows 2000 Professional default settings Autoexec.nt and Config.nt.
Your primary and secondary video adapter are both set to 16-bit color,1024x 768 resolution, and default refresh rates. You create a shortcut for the DOS-based application on the primary monitor’s desktop and use the default PIF settings.
Your attempt to run the DOS-based application on the primary monitor. The application opens, but the display area is scrambled. You then attempt to run the DOS-based application on the secondary monitor. The application does not open. Both monitors function correctly when you run Windows-based applications. What should you do?()
You are the network administrator for your company. The network consists of a single Active Directory domain. The network contains 10 domain controllers and 50 servers in application server roles. All servers run Windows Server 2003.
The application servers are configured with custom security settings that are specific to their roles as application servers. Application servers are required to audit account logon events, object access events, and system events. Application servers are required to have passwords that meet complexity requirements, to enforce password history, and to enforce password aging. Application servers must also be protected against man-in-the-middle attacks during authentication. You need to deploy and refresh the custom security settings on a routine basis. You also need to be able to verify the custom security settings during audits.
What should you do? ()
You want to back up your 100-GB database on a remote tape device. You are required to ensure that minimum network bandwidth is consumed while transferring the backups to the tape device.
The current consumption of your CPU is approximately 40 percent.
Which type of backup should you perform?()
You are designing a top-level OU structure to meet the business and technical requirements.
Which top-evel OU or OUs should you use? ()
The network consists of two separate autonomous systems as shown below:
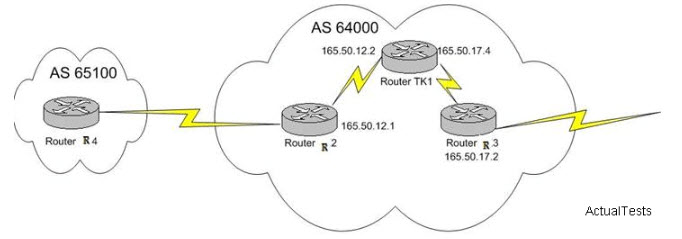
You need to configure Router R2 as a BGP route reflector and Router R1 as the client. Assumingthat Router R3 isn’t running BGP, which two of the commands below would you enter on R2 tosatisfy your goals?()
You are the administrator of Etechsol.com Enterprises. Your company consists of a small 20-user network. Management has decided to upgrade all computers to Windows 2000.
After having a closer examination of your company’s network, you realize that only half of the network interface cards are Net PC compliant. You decide to create Windows 2000 remote boot floppies.
What executable is used for creating RIS boot disks for non-PXE compliant clients?()
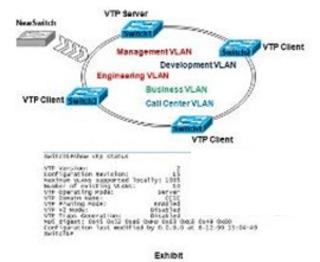
In a customer’s network, VLAN Trunking Protocol (VTP) is running with a domain named main1. VLANs 1,2,3,4,5,10,20 are active on the network. Suddenly the whole network goes down. No traffic is being passed on VLANs 2,3,4,5,10,20, however traffic passes on VLAN 1 and indicates all switches are operational. Right before the network problem occurred, a switch named TEST1 was added to the network.
What three configuration issues on TEST1 could be causing the network outage?()
You are designing a strategy for migrating to the new environment.
Which two factions from your current environment will affect your migration strategy?()

Refer to the exhibit. Users from the Engineering VLAN complain that every time Business VLAN users have a network connectivity issue, the Engineering VLAN users usually have problems experiencing slow response or network connectivity problems. After troubleshooting, an unauthorized switch 2 was found. This unauthorized switch has been a regular problem, assuming the root bridge function under the spanning-tree domain and causing the Engineering VLAN to be unstable. Which three of these actions could be suggested to fix the problem?()
All client computers in your network run Windows 7 Enterprise.
You need to prevent all standard user accounts from running programs that are signed by a specific publisher.
What should you do?()
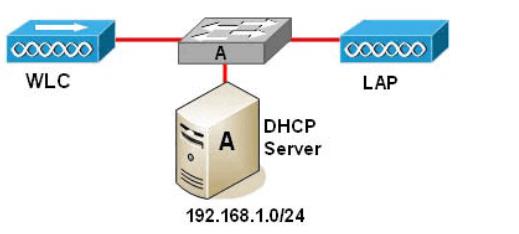
You work as a network technician at Company. Please study the exhibit carefully. In this
Company wireless network, the LAP (lightweight access point) attempts to register to a WLC (Wireless LAN Controller).
What kind of message is transmitted?()
Your network consists of a single Active Directory forest. The sales department in your company has 600 Windows Server 2008 R2 servers. You need to recommend a solution to monitor the performance of the 600 servers.
Your solution must meet the following requirements:
èGenerate alerts when the average processor usage is higher than 90 percent for 20 minutes.
èAutomatically adjust the processor monitoring threshold to allow for temporary changes in the workload.
What should you recommend?()
Your network contains several Windows Server 2008 R2 servers that run Windows Server Update
Services (WSUS). The WSUS servers distribute updates to all computers on the internal network. Remote users connect from their personal computers to the internal network by using a split-tunnel VPN connection.
You need to plan a strategy for patch management that deploys updates on the remote users coputers.
Your strategy must meet the following requirements:
èMinimize bandwidth use over the VPN connections.
èRequire updates to be approved on the WSUS servers before they are installed on the client computers.
What should you include in your plan?()
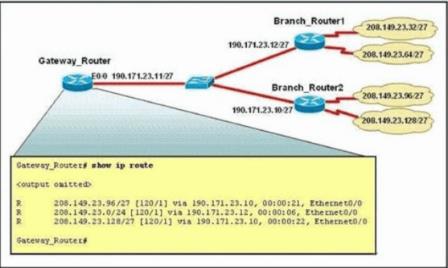
What is the most likely reason for the dispartly between the actual network numbers at the branches and the routes in the routing table on Gateway-Router?()
You have very few Cisco 7920 wireless IP phones on your network, but lots of wireless laptops. You want toincrease the bandwidth available for the laptops by decreasing the bandwidth reserved for the Cisco 7920phones.
What is the lowest percentage of voice-allocated bandwidth you can select on the WLANcontroller?()
You have very few Cisco 7920 wireless IP phones on your network, but lots of wireless laptops.You want to increase the bandwidth available for the laptops by decreasing the bandwidth reserved forthe Cisco 7920 phones.
What is the lowest percentage of voice-allocated bandwidth you can select ontheWLAN controller?()
You have very few cisco 7920 wireless ip phones on your network, but lots of wireless laptops. You want to increase the bandwidth available for the laptops by decreasing the bandwidth
reserved for the cisco 7920 phones.
What is the lowest percentage of voice-allocated bandwidth you can select on the wlan controller?()
You have a very few Cisco 7920 wireless IP phones on your network, but lots of wireless laptops.You want to increase the bandwidth available for the laptops by decreasing the bandwidth reserved for the Cisco 7920 phones.
What is the lowest percentage of voice-allocated bandwidthyou can select on the WLAN controller?()
You have very few Cisco 7920 wireless IP phones on your network, but lots of wireless laptops. Youwant to increase the bandwidth available for the laptops by decreasing the bandwidth reserved forthe Cisco 7920 phones.
What is the lowest percentage of voice-allocated bandwidth you can select onthe WLAN controller?()
In your database instance, the STATISTICS_LEVEL initialization parameter is set to BASIC.
What isthe impact of this setting()
Your computer has Microsoft Windows Firewall enabled.
Your child plays an online game that uses connectionless traffic over port 5678 for inbound and outbound traffic.
You need to prevent your child from playing this game.
What should you do? ()
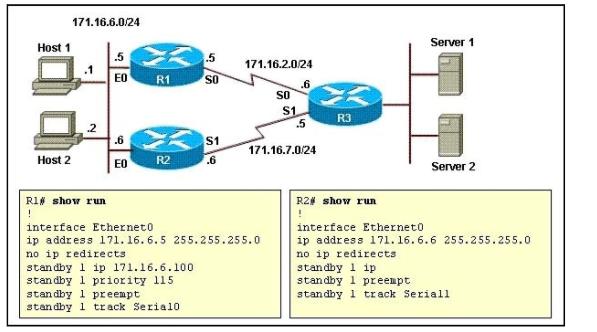
.Refer to the exhibit and the partial configuration on routers R1 and R2. Hot Standby Routing Protocol (HSRP) is configured on the network to provide network redundancy for the IP traffic. The network administrator noticed that R2 does not become active when the R1 serial0 interface goes down.
What should be changed in the configuration to fix the problem? ()
Your boss, Miss ,is interested in CEF.
What should you tell her? ()
You work as a network technician at. Your boss, Mrs. , is interested in the Spanning Tree Protocol timers.
What can you tell her regarding the default STP timers? ()
You work as a network technician at Company. Your boss, Mrs., is interested in LWAPP (Lightweight Access Point Protocol).
What should you tell her regarding this technology? ()
You work as a network technician at Company. Your boss, Mrs., is interested in the Cisco Compatible Extensions program.
What are three features of this program? ()
You are the network administrator for ExamSheet.net. Your network has 210 Windows 2000 Professional computers and eleven Windows 2000 Server computers. Users on the network save their work files in home folders on a network server. The NTFS partition that contains the home folders has Encrypting File System (EFS) enabled. A user named Sandra leaves ExamSheet.net. You decrypt the files for her manager. When the manager attempts to open any of the files, he receives the following error message: "Access is denied." You want the manager to be able to access the files.
What should do? ()
Your network contains an Active Directory domain. All servers run Windows Server 2008 R2.
You need to audit the deletion of registry keys on each server.
What should you do()
免费的网站请分享给朋友吧